Contents:
The double-extortion ransomware group dubbed Hive also encrypts Linux and FreeBSD with new malware versions designed specifically for these operating systems.
According to ESET, a Slovak internet security company that provides anti-virus and firewall products, Hive ransomware’s new encryption tools are currently at the development stage and still lack functionality.
During ESET’s investigation, the Linux version also proved to be highly problematic, with encryption malfunctioning when the virus was run with an exact path.
It also supports a single command line parameter (-no-wipe). Hive’s Windows ransomware, on the other hand, has up to five execution options, including ending processes and skipping disk cleaning, as well as ignoring uninteresting files and older documents.
As explained by BleepingComputer, the ransomware’s Linux variant also fails to encrypt when performed without root privileges because it tries to drop the ransom note on damaged devices’ root file systems.
Just like the Windows version, these variants are written in Golang, but the strings, package names and function names have been obfuscated, likely with gobfuscate.
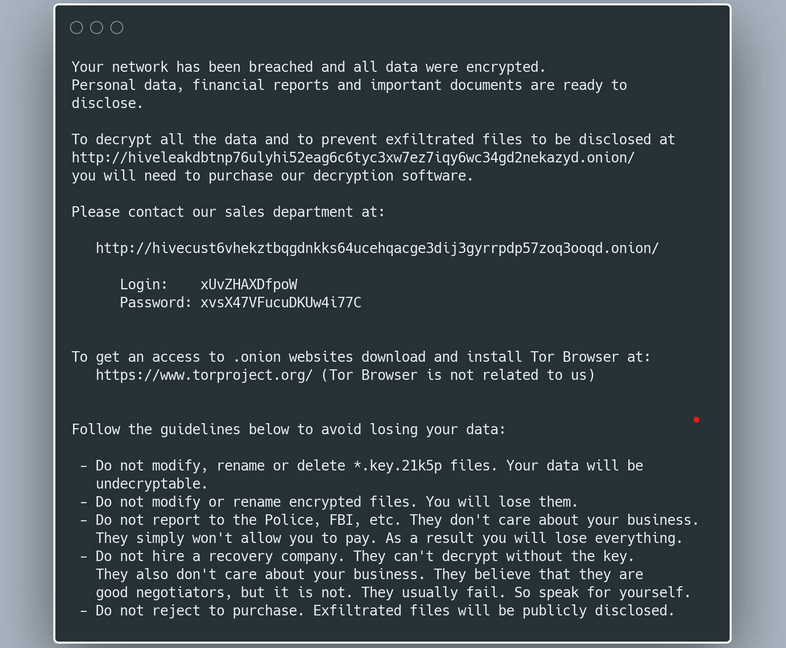
First noticed in June 2021, Hive ransomware has already impacted over 30 companies, counting only those that failed to pay the requested ransom. According to the FBI, the Hive group employs a variety of tactics, methods, and procedures to compromise targeted systems.
.hive #Ransomware
C3ACEB1E2EB3A6A3EC54E32EE620721E pic.twitter.com/HAJGyklnKu— dnwls0719 (@fbgwls245) June 26, 2021
Hive is another ransomware organization that has started attacking Linux systems as their corporate targets began switching to virtual machines (VM) for easier backups, device management, and efficient utilization of services.
Ransomware developers can encrypt numerous servers simultaneously with a single command by attacking virtual machines.
Other Ransomware Gangs Developed Linux Encryptors
In June 2021, the REvil ransomware (aka Sodinokibi) threat actors have been noticed by researchers employing a Linux encryptor that targeted and encrypted Vmware ESXi virtual computers.
CTO of Emsisoft Fabian Wosar told BleepingComputer that Babuk, RansomExx/Defray, Mespinoza, GoGoogle, DarkSide, and Hellokitty ransomware gangs have also designed Linux encryptors to target ESXi virtual computers.
As stated by Wosar, the majority of the ransomware gangs implemented a Linux-based version of their ransomware in order to target ESXi specifically.
Fabian Wosar’s statement was rapidly confirmed as in July, we saw malicious actors dubbed as HelloKitty ransomware using a Linux variant targeting VMware’s ESXi virtual machine platform for maximum damage.
Also, in August, BlackMatter ransomware gang developed a Linux BlackMatter ransomware variant to target VMware’s ESXi.
As mentioned by BleepingComputer, Snatch and PureLocker ransomware groups have previously utilized Linux variants in their operations.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










