Contents:
The malicious actors’ dubbed as HelloKitty ransomware are apparently using a Linux variant targeting VMware’s ESXi virtual machine platform for maximum damage.
As enterprises are moving towards virtual machines for easier backup and resource management, ransomware gangs are also evolving their tactics in an attempt to create Linux encryptors for targeting these servers.
We observed that over the past year, an increasing number of ransomware gangs releasing Linux encryptors targeting this platform appeared.
ESXi is not strictly Linux as it uses its own customer kernel, but it does share similar characteristics like the ability to run ELF64 Linux executables.
The security researchers from MalwareHunterTeam discovered numerous Linux ELF64 versions of the HelloKitty ransomware that were targeting ESXi servers and the virtual machines running on them.
Seems no one mentioned yet, so let me do it: the Linux version of HelloKitty ransomware was already using esxcli at least in early March for stopping VMs…@VK_Intel @demonslay335 pic.twitter.com/atSv0OO7YL
— MalwareHunterTeam (@malwrhunterteam) July 14, 2021
It was previously known that HelloKitty uses a Linux encryptor, but this was the first time when the researchers spotted a sample.
The research team shared samples of the ransomware with the news publication BleepingComputer.
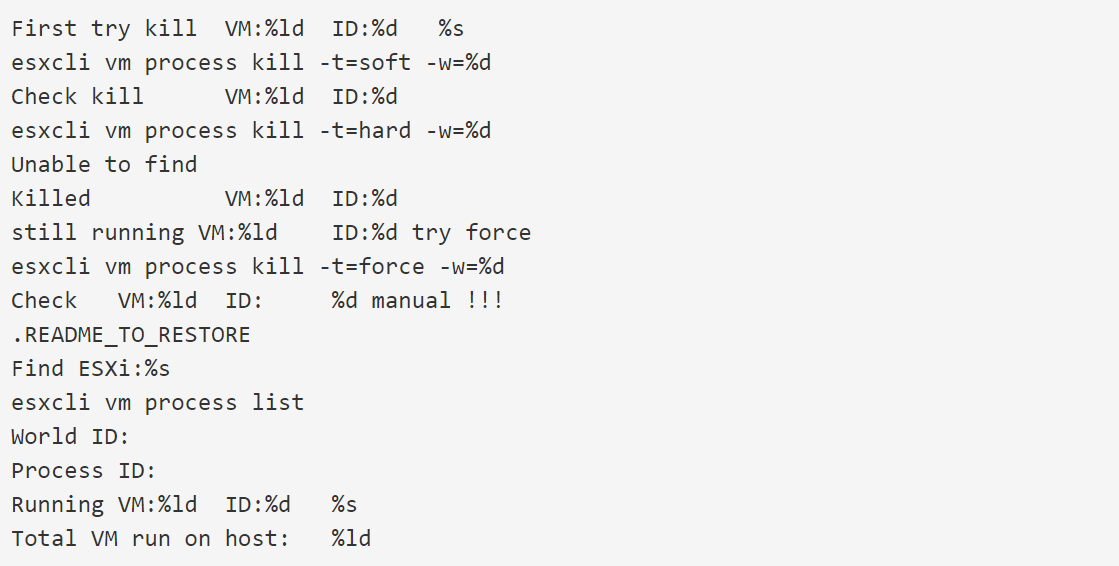
In the shared samples it’s easy to see the strings referencing ESXi and the ransomware’s attempts to shut down running virtual machines.
In this way, we can see that the ransomware uses ESXi’s esxcli command-line management tool in order to list the running virtual machines on the server and then shut them down.
The ransomware gangs that are going after ESXi servers will shut down the virtual machines before encrypting the files in order to prevent the files from being locked and to avoid data corruption.
When shutting down the virtual machines, the ransomware will first try a graceful shutdown using the ‘soft’ command.
If there are still VMs running, it will try an immediate shutdown of virtual machines using the ‘hard’ command, and finally, in the case in which the machines are still running, the malware will use the ‘force’ command to shut down any running VMs forcefully.
Once the virtual machines are shut down, the ransomware will start encrypting .vmdk (virtual hard disk), .vmsd (metadata and snapshot information), and .vmsn (contains the active state of the VM) files, in this way allowing the ransomware gang to encrypt many virtual machines just with a single command.
Find Out More About HelloKitty
HelloKity ransomware is operating since November 2020, but since that moment, the threat actors have not been particularly active when compared to other human-operated ransomware operations.
CD Projekt Red is their most well-known attack. In this attack, the threat actors encrypted devices and claimed to have stolen source code for Cyberpunk 2077, Witcher 3, Gwent, and other well-known games.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










