Contents:
The REvil ransomware (aka Sodinokibi) threat actors are now employing a Linux encryptor that targets and encrypts Vmware ESXi virtual computers.
Discovered in April 2019, Revil, also known as Sodinokibi, is a highly evasive and upgraded ransomware, which uses a special social engineering move – the ones who spread it threaten to double the ransom if not paid within a certain number of days. This aspect makes Sodinoki ransomware dangerous for both small and large businesses.
As the organization is transitioning to virtual machines for easier backups, device management, and efficient utilization of services, more and more ransomware cybercriminals produce their own instruments to encrypt a large number of VMs storage.
Last month, Advanced Intelligence, LLC Head of Research Yelisey Boguslavskiy shared a forum post from the REvil group where they corroborated that they had launched a Linux variant of their encryptor that was also able to work on NAS devices.
#REvil just directly confirmed that they have added an operating Linux version portable for NAS as well. pic.twitter.com/Fc6p2H62vf
— Yelisey Boguslavskiy (@y_advintel) May 9, 2021
Another Linux version of the REvil ransomware that seems to target ESXi servers has been discovered yesterday by the security researcher MalwareHunterTeam.
Advanced Intel’s Vitali Kremez looked into the new REvil Linux version and told BleepingComputer it is an ELF64 executable that includes the same configuration options used by the more ordinary Windows executable.
According to the researcher, that this is the first known time the Linux ransomware variant has been publicly obtainable since it was released.
When carried out on a server, a cybercriminal can specify the path to encrypt and enable a silent mode, as shown by the usage instructions below.
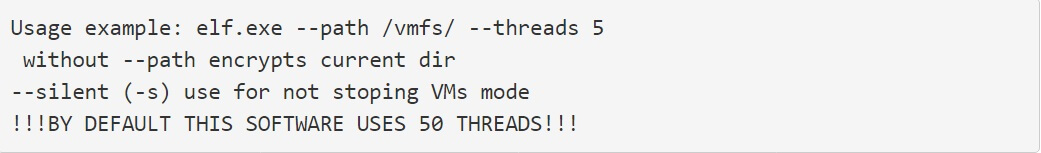
When executed on ESXi servers, it will run the esxcli command line tool to list all running ESXi virtual machines and terminate them.
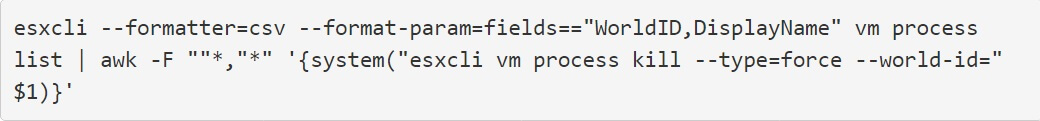
This command is used to close the virtual machine disk (VMDK) files stored in the /vmfs/ folder so that the REvil ransomware malware can encrypt the files without them being locked by ESXi.
If a virtual computer is not properly closed before encrypting its file, it could cause data corruption.
Some Darkside affiliates have a tendency to forget to stop all the ESXi daemons before kicking off the encryption. The result is that sometimes encrypted data can be interlaced with unencrypted data or that the footer containing the file key is partially overwritten. Same result.
— Fabian Wosar (@fwosar) April 14, 2021
This way REvil ransomware can encrypt multiple machines in the same time with a single command.
CTO of Emsisoft Fabian Wosar told BleepingComputer that Babuk, RansomExx/Defray, Mespinoza, GoGoogle, DarkSide, and Hellokitty ransomware gangs have also designed Linux encryptors to target ESXi virtual computers.
As stated by Wosar, the majority of the ransomware gangs implemented a Linux-based version of their ransomware in order to target ESXi specifically.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










