Contents:
The hacking gang behind the BlackMatter Ransomware goes on with its malicious activity. Now they developed a Linux BlackMatter Ransomware variant. Through a Linux encryptor, the targeted machine is none other than VMware’s ESXi.
What Is This Linux BlackMatter Ransomware Variant About?
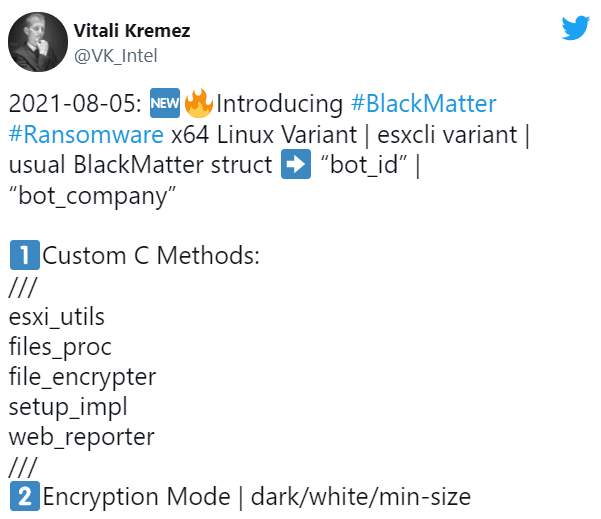
The matter of the Linux BlackMatter Ransomware variant has been analyzed by MalwareHunterTeam. As BleepingComputer Publication states, details of the discovery follow as below:
- A Linux ELF64 encryptor was found.
- This is related to BlackMatter ransomware group.
- Its target: servers belonging to VMware ESXi and it was specifically built to attack these servers.
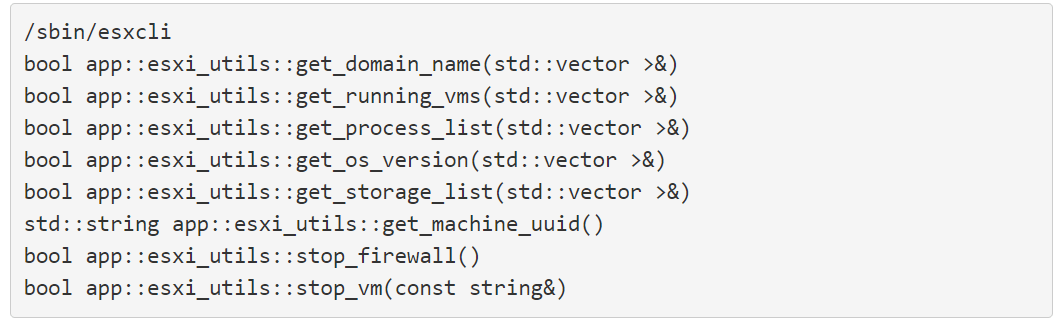
- How? Via an ‘esxi_utils’ library. This way hackers can perform whatever action they want on the server.
- The esxcli command-line management tool will be used that would determine each function from this library to execute a different command: for instance, stopping or listing a VM or making the firewall cease working.
These details were shared with BleepingComputer by Vitali Kremez, a reverse engineer from Advanced Intel.
Analyzing the sample below regarding the Linux BlackMatter Ransomware variant he clarified that for example the function stop_firewall() you can see in the last lines will trigger the command esxcli network firewall set –enabled false, while the function stop_vm() will lead to esxcli vm process kill –type=force –world-id [ID] command.
What is interesting to note here is a method hacking groups use to safely encrypt data. When attacking ESXi serves, firstly they shut down the virtual machines, then they encrypt the drive. After the VM is off than certain documents corresponding to certain extensions will be encrypted. And what’s more dangerous here is that with just one command a big number of servers can be encrypted.
Who Is BlackMatter Ransomware and When Did They Appear?
BlackMatter is actually a newly formed malicious gang that emerged last month. It is said that they take after the DarkSide and REvil groups. Their activity consisted in recruiting many cybercriminals to attack organizations from the U.S., U.K., Canada, or Australia. Their goal was to gain access to the corporate networks and what was interesting about them is that they declared to exclude some industries from their attack lists, industries like healthcare, oil & gas, critical infrastructure, and so on.
It is thought to be a better form of DarkSide because it was determined that the encryption routines are the same as those used by the latter which stopped its activity after the matter with Colonial Pipeline.
Why ESXi?
The main reason why this company is targeted by ransomware groups it’s because it has increased its popularity related to their shifting to virtual machines that support their servers for more advanced resource maintenance and rehabilitation after a disaster.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security