Contents:
A new ransomware group that calls itself BlackMatter is claiming to be a successor to now-defunct Darkside and REvil, two other notorious ransomware threat actors responsible for the cyberattacks on Colonial Pipeline and Kaseya.
The “newcomers” have launched themselves on the dark web, and are actively trying to recruit criminal partners and affiliates to attack large companies in the United States, UK, Canada, and Australia.
Last week, experts at Recorded Future cybersecurity company and security researcher pancak3 shared that a new cybercriminal called BlackMatter had posted to hacking forums where they want to buy access to corporate networks.
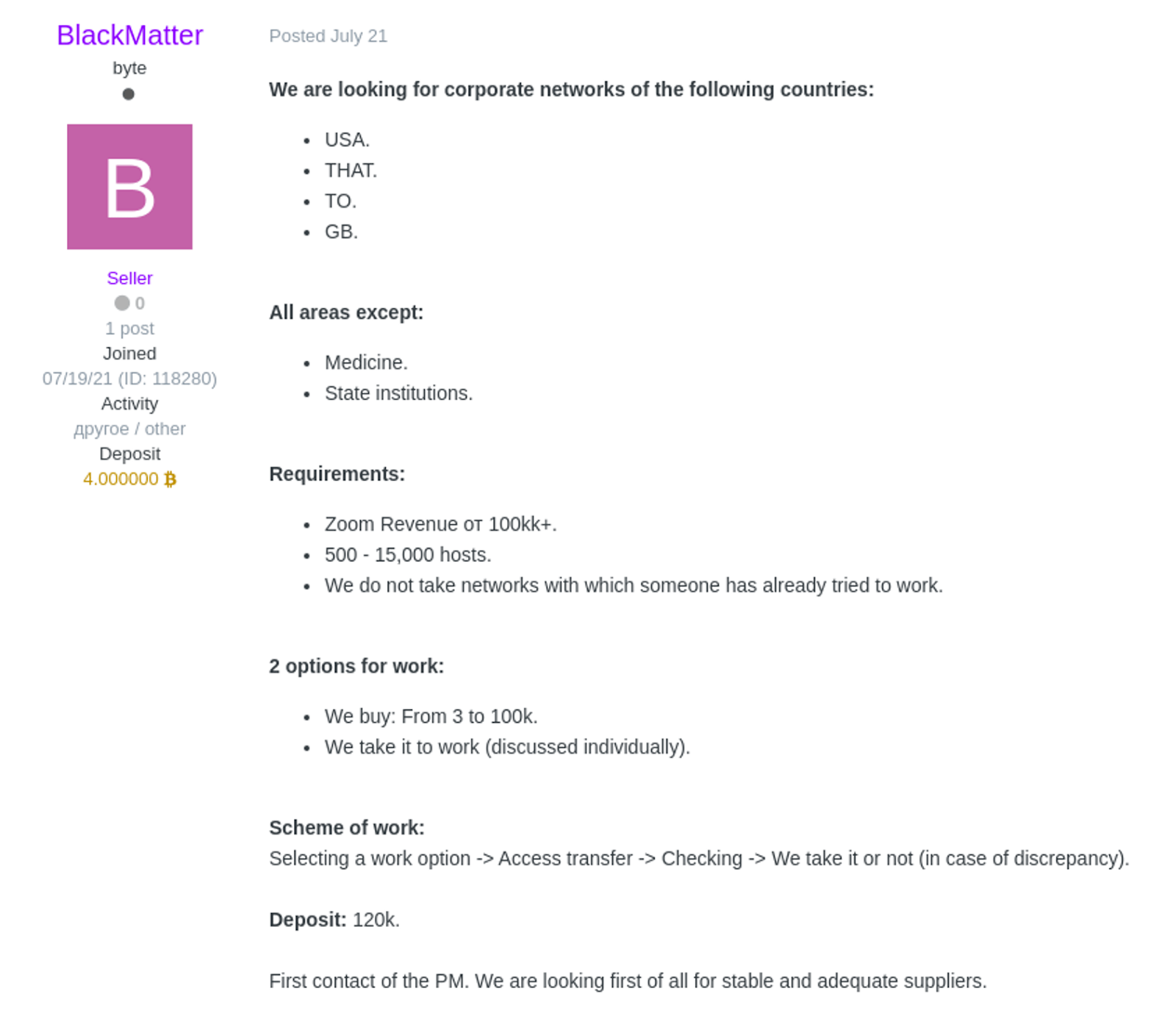
The threat actors stated they are looking to purchase access to impacted corporate networks comprising anywhere between 500 and 15,000 devices in the U.S., Canada, Australia, and the U.K. and with revenues of over $100 million or more a year.
They also said it should be a new network that other hacking groups have not already targeted.
In order to prove they are a serious player, the ransomware threat actor put $120,000 in bitcoin down in the Exile hacking forum’s cryptocurrency wallet.
While forums containing ransomware ads are now forbidden on the XSS and Exploit, the threat actor did not indicate how they would employ the network access.
BlackMatter Ransomware, a “Nice” Hacking Gang?
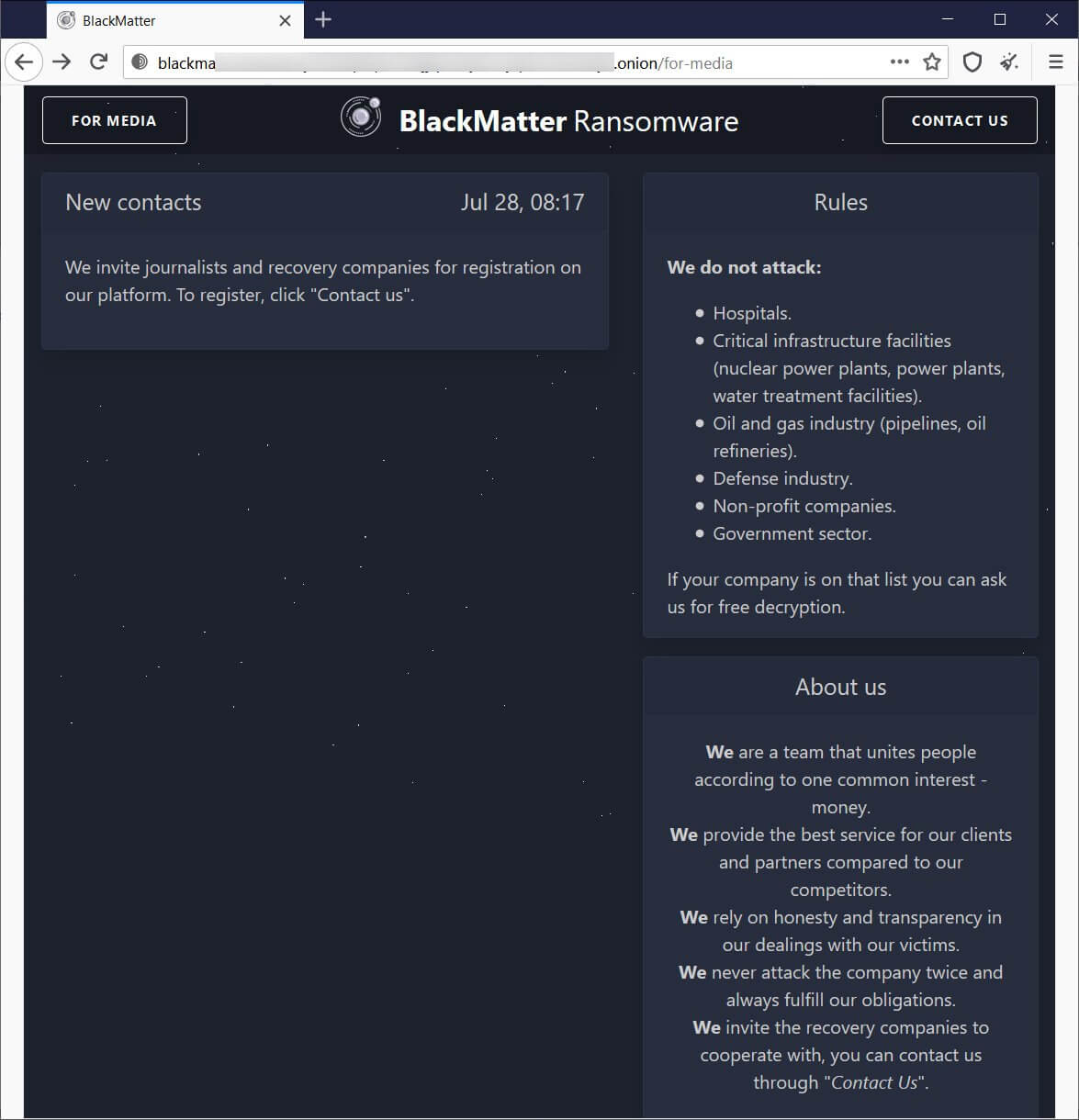
In addition to posting information about themselves, the operators behind the new BlackMatter operation promised not to target organizations in several industries, including healthcare, critical infrastructure (nuclear power plants, power plants, water treatment facilities), oil and gas, defense, non-profit organizations, and government sectors.
According to the cybersecurity firm, the group’s ransomware executables come in several formats so that they can encrypt different operating systems and device structure.
The BlackMatter ransomware group targets multiple device architectures, including Windows, Linux, and ESXi servers.
The ransomware is provided for several different operating systems versions and architectures and is deliverable in a variety of formats, including a Windows variant with SafeMode support (EXE / Reflective DLL / PowerShell) and a Linux variant with NAS support: Synology, OpenMediaVault, FreeNAS (TrueNAS).
According to BlackMatter, the Windows ransomware variant was successfully tested on Windows Server 2003+ x86/x64 and Windows 7+ x64 / x86. The Linux ransomware variant was successfully tested on ESXI 5+, Ubuntu, Debian, and CentOs. Supported file systems for Linux include VMFS, VFFS, NFS, VSAN.
As stated by BleepingComputer, at the moment there are multiple organizations targeted by the BlackMatter ransomware asking for ransom varying from $3 to $4 million.
Last week, one victim has already paid a $4 million ransom to the ransomware group in order to have the stolen data deleted and obtain both a Windows and Linux ESXi decryptor.
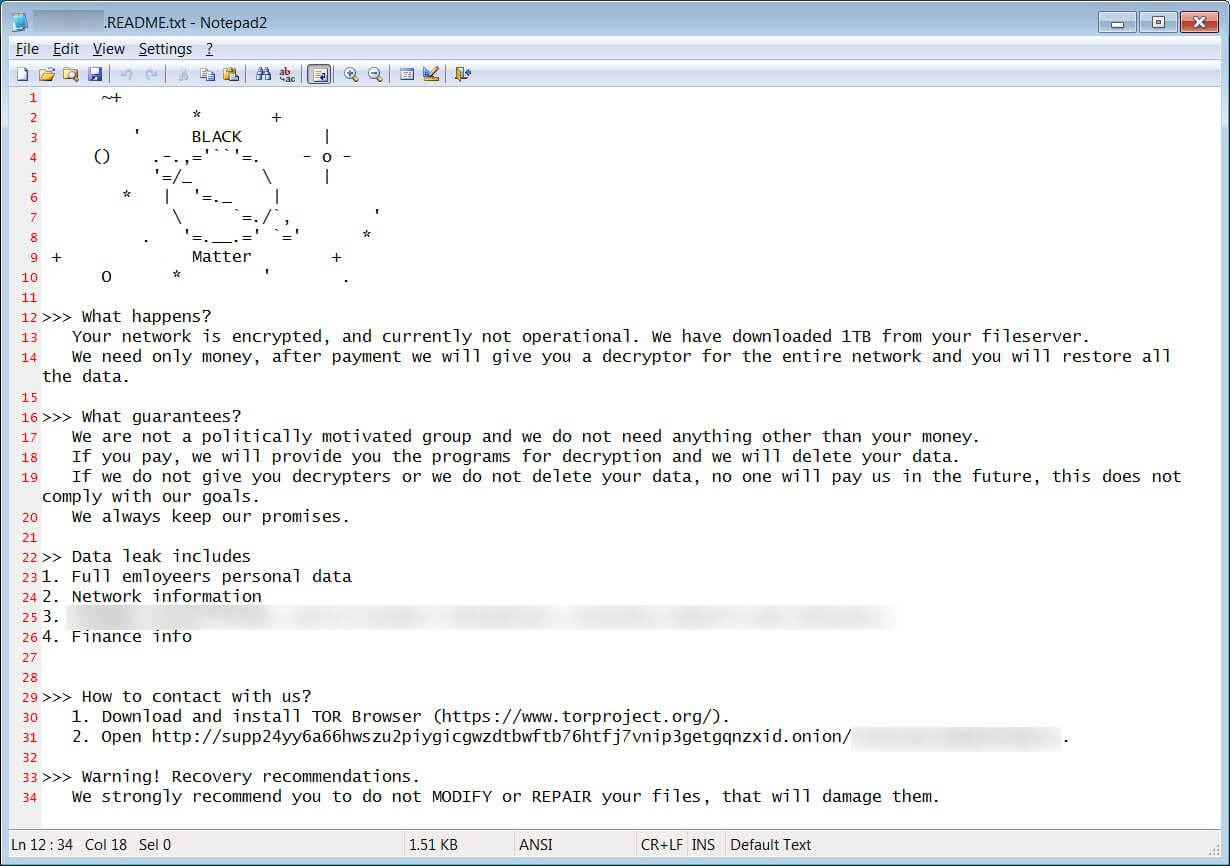
Darkside Ransomware Rebranded As BlackMatter
Emsisoft CTO and ransomware specialist Fabian Wosar analyzed a decryptor found by BleepingComputer from a BlackMatter victim and confirmed that the new ransomware gang is using the same unique encryption techniques that DarkSide had used in their cyberattacks.
Even if it is not 100% sure that Darkside has rebranded as BlackMatter, the multitude of similarities make it hard to believe otherwise.
The identical encryption algorithms, the same vocabulary used on the BlackMatter websites, the desire of being noticed by media, and similar color themes for their TOR sites make us believe that BlackMatter and DarkSide are one and the same.
It would also explain the reason why the new ransomware group doesn’t want to attack the oil and gas industry, considering that the Colonial Pipeline attack caused the DarkSide shutdown in the first place.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










