Contents:
Before we dive into what is Hive ransomware, you might have heard the good news. This past week, on January 26th, to be exact, the FBI successfully shut down the Hive ransomware group and saved victims over a hundred million dollars in ransom payments and remediation costs.
But this is not to say that we’re totally safe and that we are out of the woods.
As ransomware continues to be a national security threat and ransomware gangs like BlackMatter, REvil, and DarkSide are constantly evolving, developing new tools, and changing tactics, we thought we’d give you a quick overview of Hive ransomware, including who they are, what they are, who they target, and more.
So let’s jump in!
What Is Hive Ransomware?
Hive ransomware was first discovered in June 2021 and it’s an affiliate-based ransomware where cybercriminals use to target healthcare facilities, nonprofits, retailers, energy providers, and other sectors worldwide. This Ransomware-as-a-Service model enables affiliates to utilize Hive ransomware as they see fit.
The operator of Hive ransomware uses common ransomware tactics, techniques, and procedures to compromise victims’ devices, exfiltrate sensitive data, and encrypt business files.
In addition to phishing emails containing malicious attachments, leaked VPN credentials, and exploiting vulnerabilities on external assets, their affiliates compromise their victims’ networks. Moreover, Hive places a plain-text ransom note that threatens the victim’s data to be published on the TOR website ‘HiveLeaks’ unless they meet the attacker’s demands.
The Hive ransomware group is thought to be a Russian organization. Some of its affiliates are said to have migrated to Hive around May 2022, as the Conti group shut down its attack infrastructure.
The belief stems from the fact that Conti and Hive have simultaneously leaked the same victims on both of their leak sites, such as the attack on Costa Rican government infrastructures.
Below you’ll see some pictures of Hive’s admin panel and disclaimers:
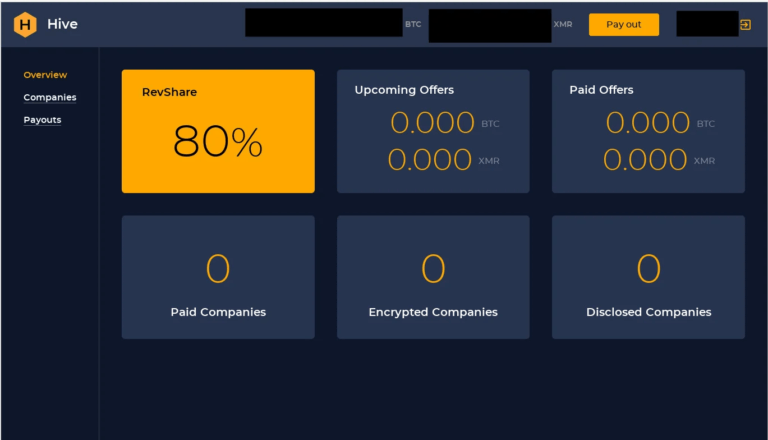
Hive’s admin panel.
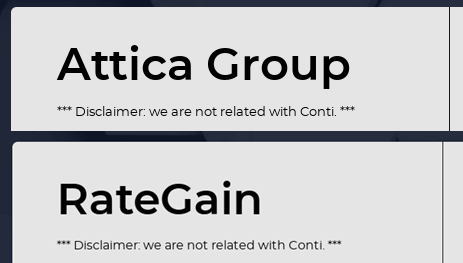
Hive’s ransomware disclaimer.
According to the Hive TOR leak site, Hive Ransomware has targeted institutes from more than 20 countries since its emergence, from the far west, the USA, to the far east, Japan.
Now let’s take a closer look at how Hive ransomware operates and what tactics they use.
How Does Hive Ransomware Work?
According to the FBI, the Hive ransomware gang uses a variety of TTPs for their attacks. Phishing tricks are regularly employed to gain initial access, which Verizon states is a factor in 82% of all breaches. Then, they use various malware-laden attachments to infiltrate critical systems & Remote Desktop Control to move horizontally across the network.
Early versions of Hive variants were developed in GoLang. In mid-2022, when the public decryptor was released, they might have turned to Rust, specifically version 5, to create new versions of their malware.
Hive ransomware encrypts critical files, then distributes two malicious scripts (hive.bat and shadow.bat) for cleanup. The group then threatened to leak the encrypted information on the dark web on HiveLeaks.
When compromising a victim network, Hive ransomware actors leak data and encrypt files on the web. In addition, the actors leave a ransom note on each affected directory on the victim’s system, which provides instructions on acquiring decryption software.
Hive uses spear-phishing emails with attachments to access the victim’s network. After obtaining the victim’s credentials, it uses Remote Desktop Protocol (RDP) to infect the network laterally.
Hive terminates backups, restores, anti-virus, antispyware, and file copies to avoid anti-malware. When Hive encrypts files and saves them with a .hive extension, it creates batch files called hive.bat and shadow.bat, which contain commands to delete
Hive’s executable, disc backup copies, snapshots, and batch files. To reduce forensic evidence available, the malware uses this technique.
Lastly, a ransom note is dropped by Hive into each affected directory. The notice explains that encrypted files cannot be decrypted without the master key in the actors’ possession.
The note also contains the login details for the HiveLeaks TOR website, which the victim can use to pay the ransom. It threatens to leak sensitive data to HiveLeaks.
Here’s a snap from the Hive ransom note:
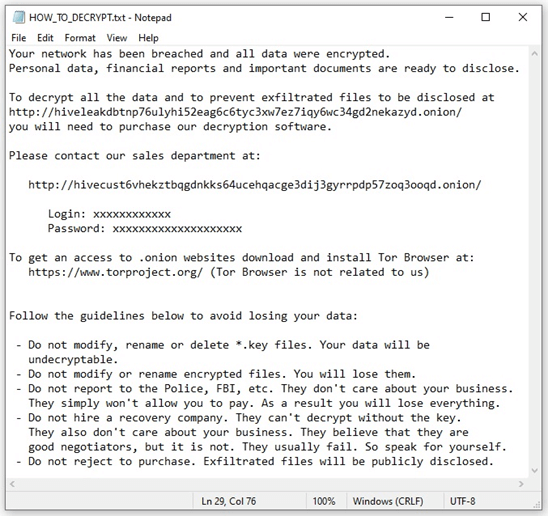
Hive ransomware actors communicate the ransom amount and payment deadline to victim organizations via live chat. The Hive actors negotiate ransom demands in U.S. dollars, with initial amounts ranging from several thousand dollars to millions. They demand bitcoin payment.
Networks of victim organizations that have restored their networks without paying a ransom have been reinfected with Hive ransomware or another ransomware variant by Hive actors.
Hive Ransomware Rust Variant Assessment
Cybersecurity researchers analyzed Hive Ransomware v5 in Rust, which uses string encryption to make it more mysterious. Strings are stored in .rdata and decrypted during runtime by XORing with constants. Unfortunately, detection is not always accurate since the constants used to decrypt the exact string vary from sample to sample.
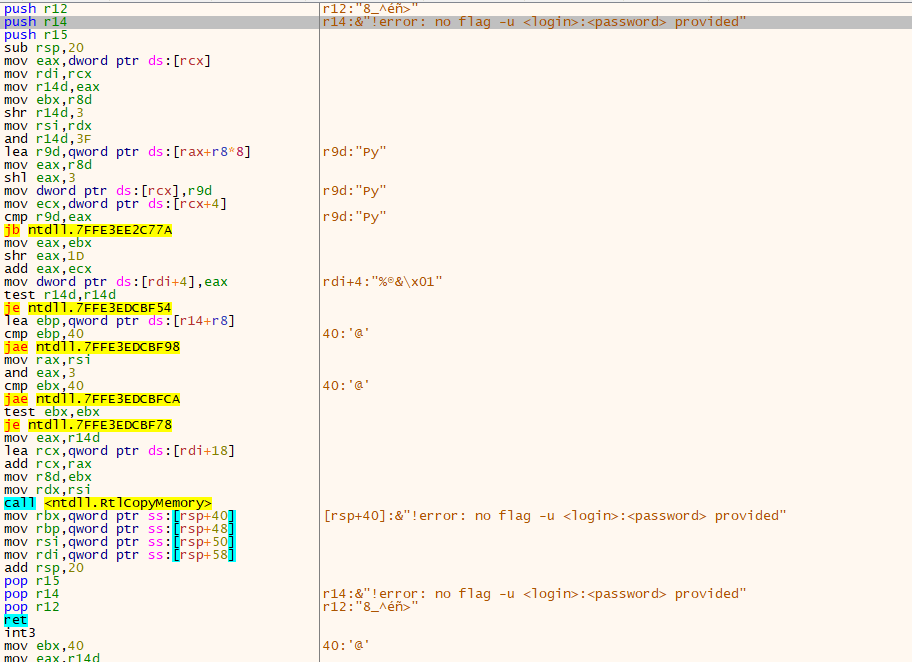
Analysts cannot obtain the credentials from the sample because they are provided on the command line with the “-u” parameter. An attacker can encrypt files only on remote shares or local files or set a minimum file size for encryption.
Below are the parameters for the Rust variant of Hive ransomware:
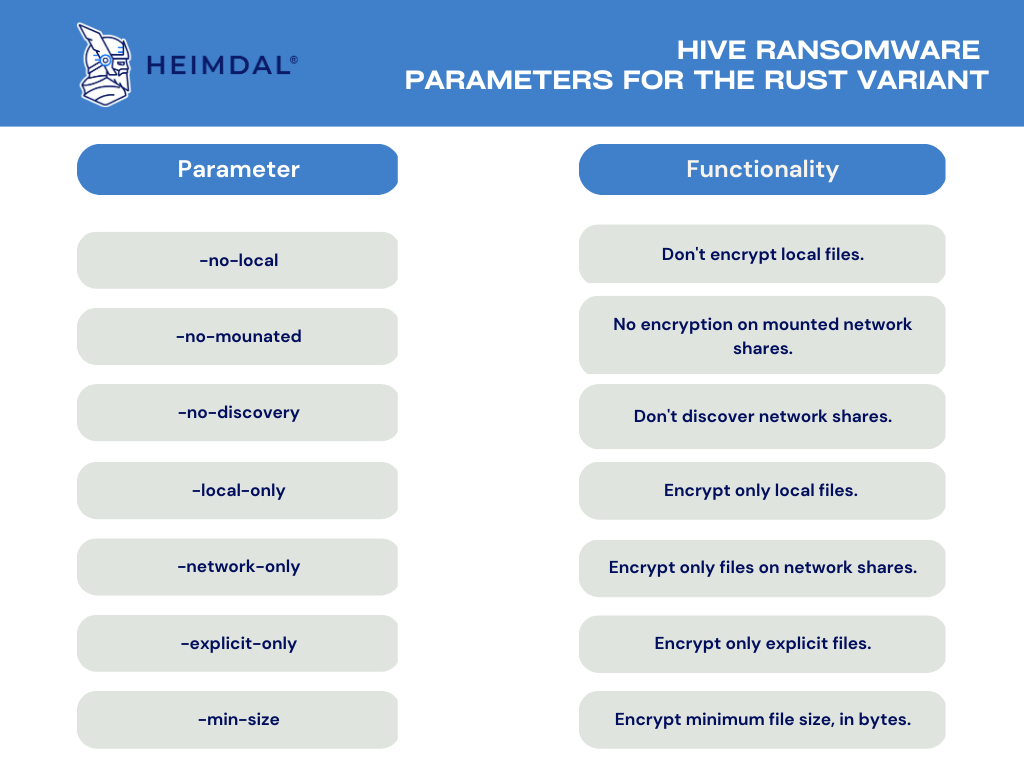
In the Rust variant of Hive Ransomware, attackers must first know the parameters. With this advancement, it is difficult for the researcher and analyst teams to find parameters in encrypted strings. Another typical result we saw while monitoring the processing activity was using “vssadmin.exe” to clean the backup with the “delete shadows /all /quiet” parameters.
Another discovery made during the analysis is that different algorithms are used in the Rust variant, such as:
- Elliptic Curve Diffie-Hellmann (ECDH) with Curve25519;
- XChaCha20-Poly1305 authenticated encryption method with ChaCha20 symmetric cipher.
The Rust variant does not encrypt the following file extensions:
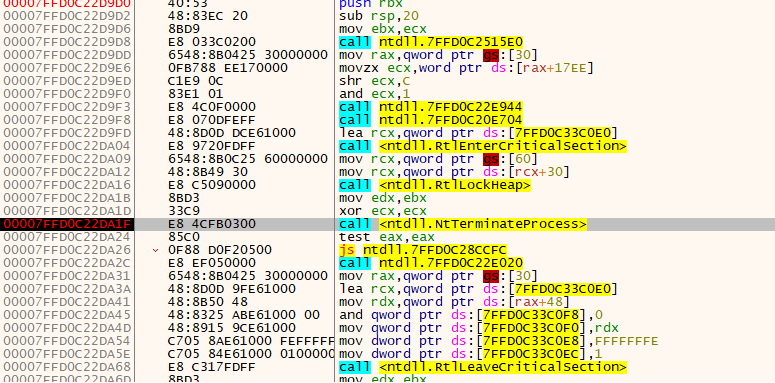
When cybersecurity researchers examined the function call made at the address “00000000004613AF,” they discovered that the NtTerminateProcess API call was made at the address “000000000047867B” within it.
By changing the RIP, it is possible to avoid anti-analysis at these addresses.
What are Hive’s Target Countries and Industries?
Hive has a TOR leak site where victims can share countdowns. However, this website only shares victims who did not comply and did not pay the ransom demanded. As an aside, according to research conducted at the end of 2021, Hive targets three organizations on average per day.
The study also discovered that Hive compromised 355 organizations, with only 55 victims sharing information on their TOR leak site.
Nearly 30 countries have been affected by Hive Ransomware attacks from its TOR leak site. When we examine the targeted countries closely, the United States is a top target. With 93 attacks, the United States accounts for nearly half of all Hive Ransomware attacks.
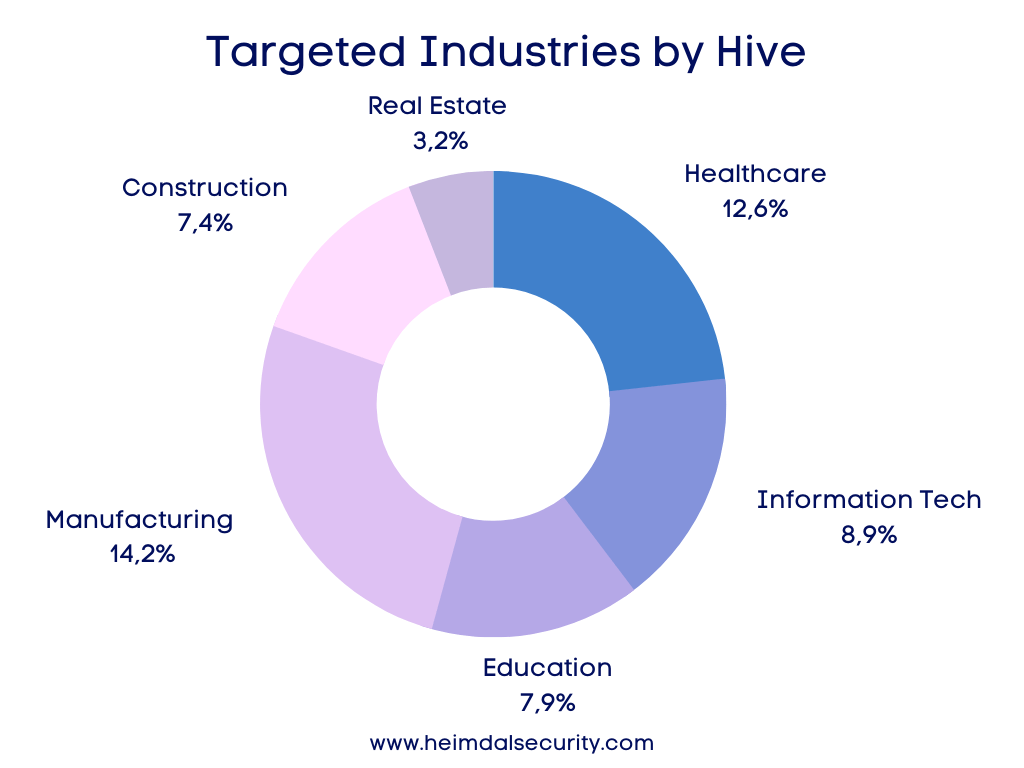
Four industries stand out above the rest when we look at the statistics for the industries in terms of Hive Ransomware attacks. Hive Ransomware has been observed to target over 30 sectors, such as:
- Healthcare 12,6%;
- Manufacturing 14,2%;
- Information Technology 8,9%;
- Education 7,9%;
- Construction 7,4%;
- Real Estate 3,2%.
To avoid causing harm to people, some ransomware groups operating as RaaS claim to avoid targeting institutes such as healthcare.
For example, LockBit apologized for its latest attack on a healthcare institute and severed ties with the responsible affiliate. However, Hive’s attacks on healthcare providers demonstrate that the organization’s operators have no moral incentive to avoid attacking such organizations.
Now we know that Hive ransomware has been busted. For now. But bear in mind that it has no limitations when deciding who to target. They attack regardless of whether it is a large manufacturing organization or a small healthcare institute. However, given how Hive Ransomware operates, organizations of all sizes should be aware of its existence and take appropriate precautions.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
How Can Heimdal Help?
As with most ransomware attacks, Heimdal® provides its customers with an exceptional integrated cybersecurity suite, including Ransomware Encryption Protection, which is universally compatible with any antivirus solution and 100% signature-free, ensuring superior detection and remediation of all types of ransomware.
You can avoid ransomware by doing a few simple things. Cybercriminals have the same impact on your data and security as you do. Feel free to read our articles on preventing and mitigating ransomware attacks to expand your knowledge of ransomware protection.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








