Contents:
As a result of an attack against the Hospital for Sick Children (SickKids), the LockBit ransomware gang has formally apologized and released a free decryptor for the hospital.
Toronto’s SickKids Hospital is a teaching and research hospital that treats sick children. An attack on the hospital’s internal and corporate systems, phone lines, and website occurred on December 18th.
Even though the attack only encrypted a few systems, SickKids stated that it caused delays in receiving lab and imaging results and longer wait times for patients.
SickKids announced that 50% of its priority systems, including those causing diagnostic or treatment delays, had been restored.
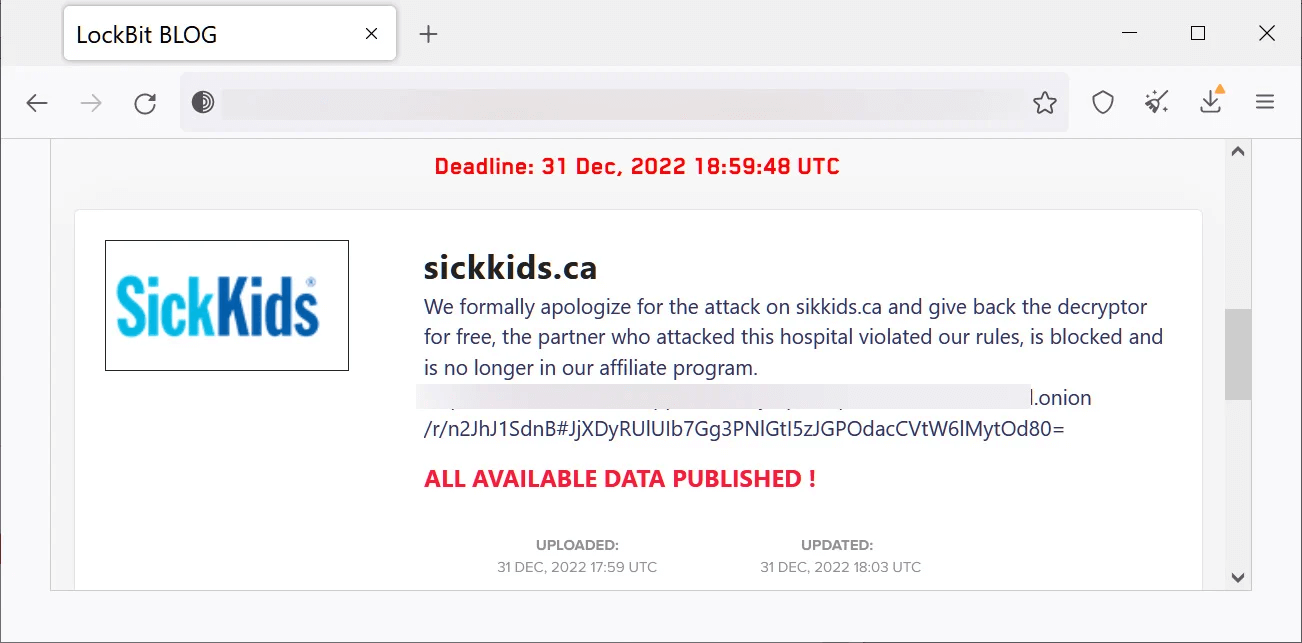
The LockBit Ransomware Gang Apologized for the Attack
Two days after SickKids’ latest announcement, the LockBit ransomware gang apologized for the attack and released a free decryptor.
We apologize formally for the attack on sikkids.ca and provide the decryptor for free. However, the partner who attacked this hospital violated our rules and has been blocked from joining our affiliate program.
As there is no additional Windows decryptor, the attacker could only encrypt virtual machines on the hospital’s network.
As a Ransomware-as-a-Service, LockBit’s operators maintain the encryptors and websites, while its affiliates breach victims’ networks, steal data, and encrypt their devices.
The LockBit operators keep approximately 20% of all ransom payments, while the affiliate receives the rest.
Despite allowing its affiliates to encrypt pharmaceutical companies, dentists, and plastic surgeons, it prohibits its affiliates from encrypting “medical institutions” where attacks could result in death.
A ransomware operation’s policies state that it is forbidden to encrypt files in institutions that may cause death, such as cardiology centers, neurosurgery departments, maternity hospitals, and the like, that is, institutions where surgery can be performed using high-tech equipment and computers.
According to the policies, stealing data from any medical institution is permissible.
One ransomware gang’s affiliates encrypted the hospital’s devices, and they were removed from the operation and given a free decryptor.
This does not explain why LockBit did not provide a decryptor sooner, especially since SickKids has been working to restore operations since the 18th.
LockBit has a history of encrypting hospitals without providing encryptors, as seen in its attack against the Center Hospitalier Sud Francilien (CHSF) in France, where a $10 million ransom was demanded, and patient data was eventually leaked.
During the attack on the French hospital, patients were referred to other medical centers, and surgeries were postponed, which could have resulted in significant patient risks.
Despite being against policies, BleepingComputer had contacted LockBit to understand why they were demanding a ransom from CHSF but have yet to receive a response.
In the past, there have been occasions where a ransomware gang has provided its victims with a decryption tool. For example, after increased pressure from international law enforcement, the Conti Ransomware operation provided a free decryptor to Ireland’s national health service, the HSE, in May 2021.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










