Contents:
According to a report released by Accenture Security on Tuesday, it appears that Hades Ransomware group has taken further steps in an apparent bid to confuse investigators who have tried to work out who exactly the operators are.
Who is Behind Hades Ransomware?
Back in March, CrowdStrike researchers linked Russian cybercriminal gang Evil Corp to Hades ransomware after noticing a “significant code overlap.”
Hades ransomware shares the majority of its functionality with WastedLocker; the ISFB-inspired static configuration, multi-staged persistence/installation process, file/directory enumeration and encryption functionality are largely unchanged. Hades did receive minor modifications, and the removed features included those that were uniquely characteristic of INDRIK SPIDER’s previous ransomware families — WastedLocker and BitPaymer.
First discovered in December 2020 by cybersecurity analysts, Hades ransomware was named after a Tor hidden website that victims are instructed to visit.
A ransom note named ‘HOW-TO-DECRYPT-[extension].txt’ is created when Hades encrypts a victim’s systems, resembling the notes sent by REvil ransomware. The ransom note redirects the victims to a Tor site with info about the attack and has a Tox messenger address they can use to contact the ransomware operators.
Accenture researchers believe “is not yet able to confidently make attribution claims”, while other analysts have variously described Hades as a new group, suggested it is connected to the well-known Evil Corp, or linked its activity to a Chinese nation-state hacking outfit thought to be behind this year’s Microsoft Exchange Server attack.
The report shows that since March, Hades ransomware targeted new victims in the consumer goods and services, insurance and manufacturing, and distribution industry sectors.
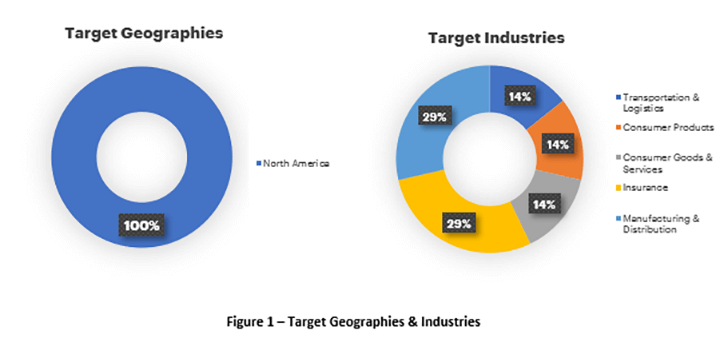
Image Source: Accenture Security
Additionally, the threat actors have added the Phoenix Cryptolocker variant to their arsenal, “to deter attribution claims or campaign links.” Another thing observed by the researchers is that while the Hades operators have been consistent in their tactics, targeting, and procedures, “some unique and destructive actions were observed across intrusions, such as targeted enumeration of cloud environments and destruction of cloud-native backups or snapshots.”
Finally, the Accenture researchers declared that they are moderately confident the operators don’t use an affiliate model or offer ransomware-as-a-service, both being popular ways for ransomware gangs to make more money.
A Potential Ransomware Rebranding Trend?
These observations into Hades ransomware arrive as well-known ransomware groups are undergoing a revamp. DarkSide ransomware, which is responsible for the Colonial Pipeline attack, said it was disbanding following massive negative publicity and law enforcement attention from the May incident.
Likewise, the Avaddon ransomware gang disappeared this month under mysterious circumstances after sending a ZIP file with the decryption keys for all victims affected.
Many cybersecurity specialists say that maybe these ransomware groups are just experiencing a rebranding phase, as threat actor groups did in the past.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










