Contents:
The news was released to the public by a threat actor known as “UNKN”, the public-facing representative of a rival ransomware gang known as REvil.
In the post that was discovered by Dmitry Smilyanets on an exploit hacking forum – “Unkn” shared a message that is supposed to have originated from Darkside, that explained how the threat actors have been denied access to their public data leak site, payment, and CND servers due to a law enforcement action.
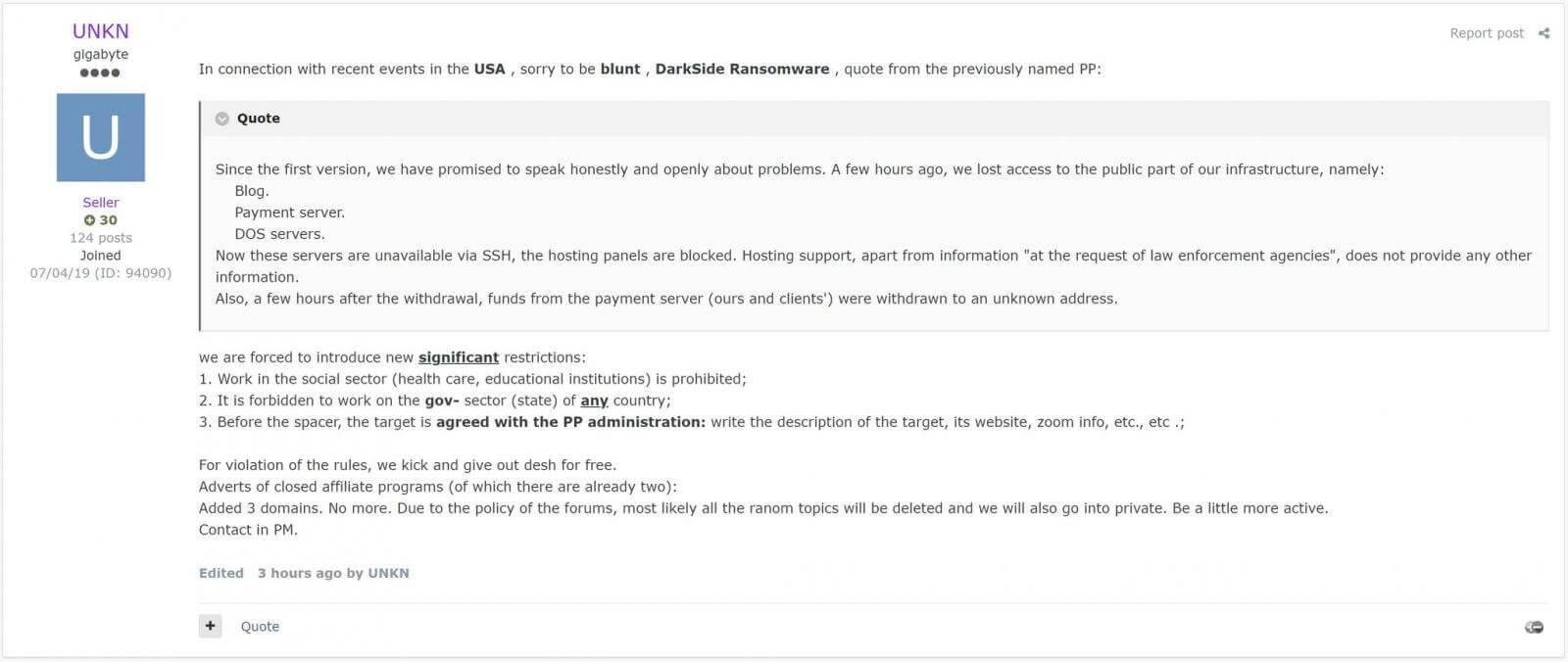
The forum post shared by Unkn relates explicitly the information shared by Darkside
A few hours ago, we lost access to the public part of our infrastructure, namely: Blog, Payment server, DOS servers.
Now, these servers are unavailable via SSH, the hosting panels are blocked. Hosting support, apart from information “at the request of law enforcement agencies, does not provide any other information.
The post originated from Darksupp, described as the operator of Darkside.
This comes after recent firm declarations made by top US officials, including the US President – Biden after official FBI declarations that stated the Colonial Pipeline incident was linked to Darkside Ransomware. At some point in time, a Russian-led attack has been speculated only for the link with the Russian Government to be dismissed by President Biden.
We do not believe — I emphasize, we do not believe the Russian government was involved in this attack. But we do have strong reason to believe that criminals who did the attack are living in Russia. That’s where it came from — were from Russia.
We have been in direct communication with Moscow about the imperative for responsible countries to take decisive action against these ransomware networks.
Security specialists and journalists have noted that the Darkside website has no longer been available starting late last week and there were speculations that the law enforcement representatives have taken down the website.
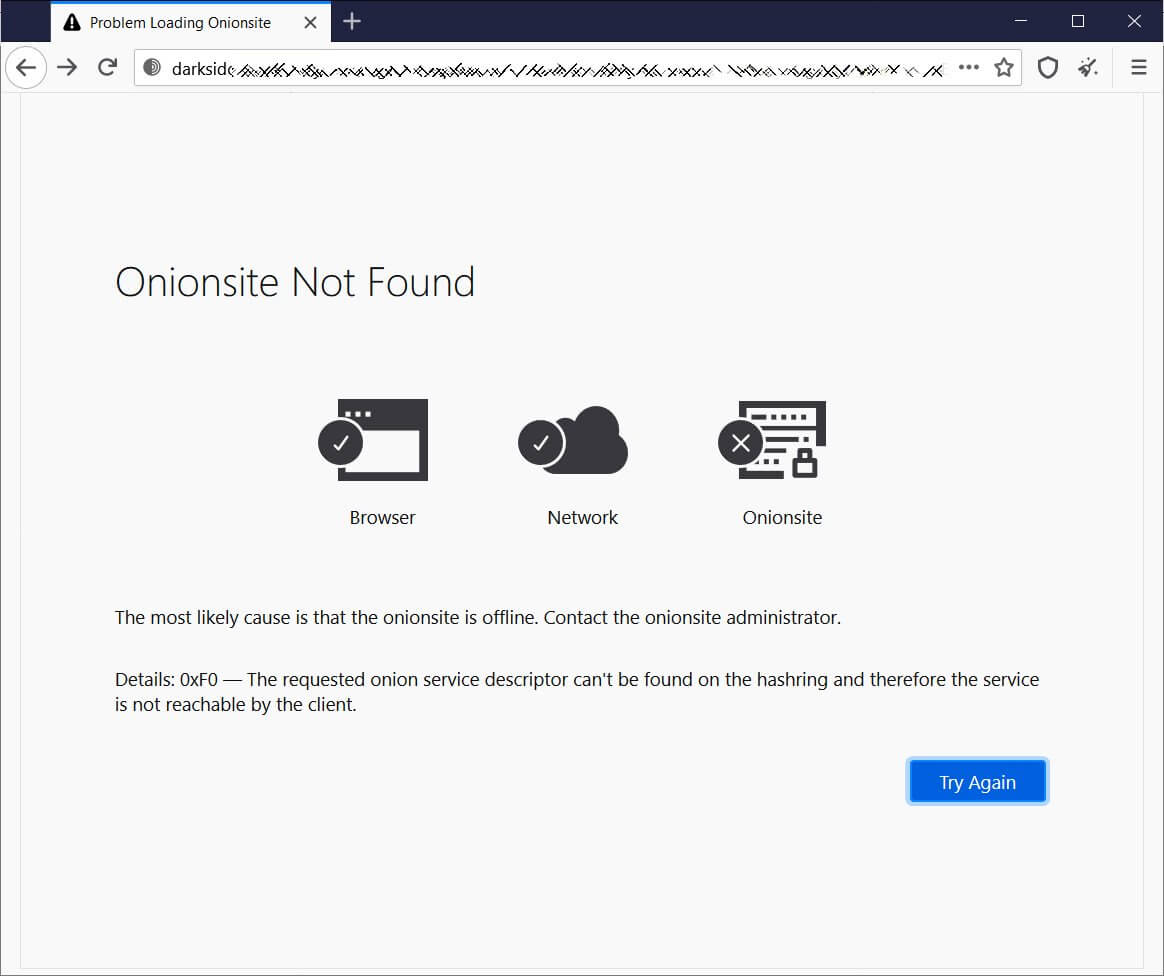
On a side note, it has been assumed that the Darkside Ransomware gang might try to pull an exit scam.
The Gang has shut down their affiliate program also after, between Bernntag and Colonial Pipeline they may have pulled 9.4 million USD in ransom payments, and basically, they are blaming law enforcement actions who “are stealing the money” – this way they will not have to pay their affiliates in the operation.
These assumptions are confirmed via a message sent by Darkside to their affiliates of this RaaS operations:
Starting from version one, we promised to speak about problems honestly and openly. A couple of hours ago, we lost access to the public part of our infrastructure, in particular to the
- Blog
- payment server
- CDN servers
At the moment, these servers cannot be accessed via SSH, and the hosting panels have been blocked.
The hosting support service doesn’t provide any information except “at the request of law enforcement authorities.” In addition, a couple of hours after the seizure, funds from the payment server (belonging to us and our clients) were withdrawn to an unknown account.
The following actions will be taken to solve the current issue: You will be given decryption tools for all the companies that haven’t paid yet.
After that, you will be free to communicate with them wherever you want in any way you want. Contact the support service. We will withdraw the deposit to resolve the issues with all the affected users.
The approximate date of compensation is May 23 (due to the fact that the deposit is to be put on hold for 10 days on XSS).
In view of the above and due to the pressure from the US, the affiliate program is closed. Stay safe and good luck.
The landing page, servers, and other resources will be taken down within 48 hours.
After these events, REvil ransomware decided to impose restrictions on who they attack.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
UNKN, the REvils representative, states that their affiliates have now to gain permission on who they encrypt and can no longer encrypt or event target entities that work in the social sector nor gov-sector (state) of any country.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










