Contents:
The massive breach includes information from multiple breaches, totaling 12 terabytes of data spread across 26 billion records.
This is likely the biggest data breach that has ever been found; it includes information about users of LinkedIn, Twitter, Weibo, Tencent, and other platforms.
Who discovered the data set?
The MOAB was brought to light by cybersecurity researcher Bob Dyachenko and the Cybernews team.
The experts discovered billions of exposed records on an open instance whose owner is unlikely to be identified.
What type of data does it contain?
The breach is extensive, covering 3,800 folders, each linked to a separate data breach. It contains a mix of sensitive information, from personal details to login credentials, some of which might be previously unpublished.
While the team found over 26 billion records, duplicates are highly likely. However, the leaked data contains far more than just credentials; the majority of the exposed data is sensitive and therefore valuable to malicious actors.
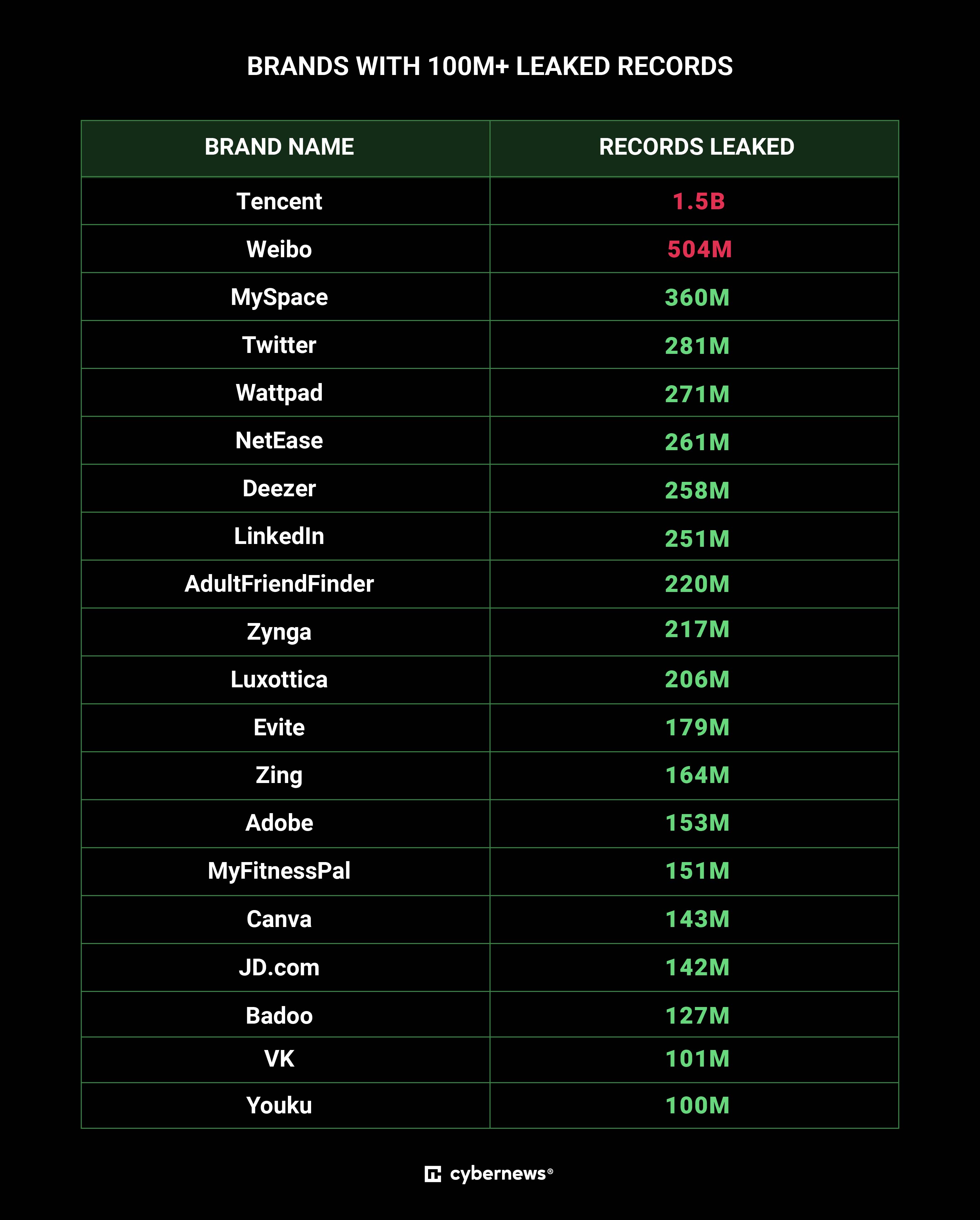
List of brands with over 100M leaked records (source)
A cursory examination of the data tree exposes an enormous quantity of records accumulated from prior breaches. Tencent QQ, a popular Chinese messaging app, has the most records with 1.4 billion.
Weibo, MySpace, Twitter, Deezer, Linkedin, AdultFriendFinder, Adobe, Canva, VK, Daily Motion, Dropbox, and Telegram are just a few of the many companies and organizations that allegedly have hundreds of millions of records.
Documents from a number of US, Brazilian, German, Philippine, and Turkish government agencies are also among those leaked.
The group claims that the supermassive MOAB may have never-before-seen effects on consumers. Criminals might launch an upsurge of credential-stuffing attacks because so many people reuse passwords and usernames.
Potential consequences
The consequences of such a leak are serious. The exposed data can be used in identity theft, phishing attempts, and unauthorized access to accounts. As the researchers put it, the data can be used by threat actors for various malicious activities.
In response to the threat, experts are emphasizing the importance of preventive measures. Individuals are advised to:
- use strong, unique passwords for each of their accounts
- check for password duplicates and immediately set up new protection for accounts that share the same passwords.
- enable multi-factor authentication
- stay alert to phishing attempts
Cybernews also has a data leak checker that you can use to see if any of your personal information has been compromised in past breaches.
If you liked this piece, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










