Contents:
Data obfuscation is an important tool for businesses in this digital age, but many are left wondering what it actually is and how to use it. In this article, we will be demystifying data obfuscation and exploring its potential benefits for your business, so that you can make the most of the technology available to you.
What Is Data Obfuscation?
Data obfuscation is the process of making data unreadable or difficult to understand, thus making it useless to malicious actors. In test and development environments, developers and testers need realistic data to build and test software, but they do not need to see the real data.
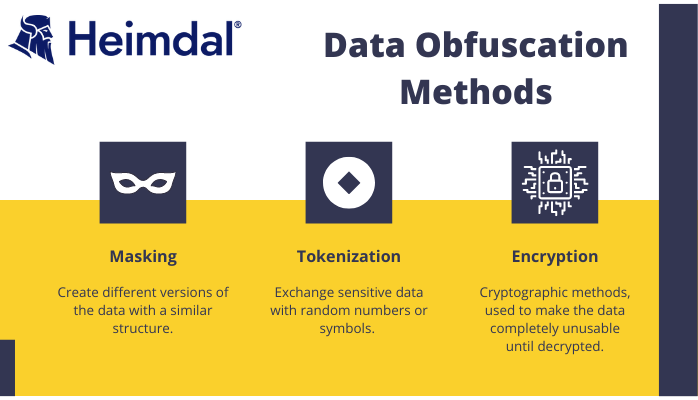
There are a number of different ways that data can be obfuscated, including encryption, tokenization, and masking.
- Masking is a way to create different versions of the data with a similar structure. The data type does not change, only the value change. In other words, masking replaces certain elements of the data with fictitious values, making it difficult to interpret without knowing the specific rules that were used.
- Data encryption uses cryptographic methods, usually symmetric or private or public key systems to make the data completely unusable until decrypted. Encryption is very secure and is the most common method of data obfuscation, yet when you encrypt your data, you cannot manipulate or analyze it.
- Data tokenization implies exchanging sensitive data with random numbers or symbols, making it impossible to reconstruct the original information without the special token. Only authorized users can connect the token to the original data.
Data obfuscation can be an effective way to protect your business’s confidential information. However, it is important to remember that any method of obfuscation can be circumvented if someone is determined enough. The best way to protect your data is to combine multiple methods of obfuscation, making it as difficult as possible for unauthorized individuals to access or understand your information.
Other Data Obfuscation Methods
There are several other techniques your organization can use to obfuscate data:
- Non-deterministic randomization— is replacing the real value with a random value, within certain parameters that ensure the value is still valid.
- Shuffling— means changing the order of digits in a number or code that does not necessarily have a meaning.
- Blurring— involves adding a different number, while remaining in the general vicinity of the original number. For example, changing the amount of funds in a bank account to a random value within 10% of the original amount.
- Nulling— is replacing original values with a symbol that represents a null character, such as ####-####-####-9887 for a credit card number.
- Repeatable masking— refers to replacing a value with a random value, but making sure that the original values are always mapped to the same replacement values.
- Substitution— deals with replacing the original number with one value from a closed dictionary of values. for example, replacing a name with a name randomly selected from a list of 10,000 possible names.
- Custom rules—it is important to specify rules to retain the validity of special data formats, such as social security numbers, addresses, phone numbers, etc. For example, to perform obfuscation of addresses, you will need to use a geographical database and ensure you are replacing each element of the address with a valid value—street number, street name, city, country, etc.
Benefits of Using Data Obfuscation
There are many benefits of using data obfuscation to protect your business data. Here are some of the most important benefits:
- Risk and regulatory compliance: In other words, obfuscation will help you comply with data privacy laws. Data privacy laws such as the General Data Protection Regulation (GDPR) require businesses to take steps to protect the personal data of their customers and employees. One way to do this is by obfuscating the data so that it is not easily accessible or decipherable.
- Flexibility: Data obfuscation is also highly customizable. You can select which data fields get masked and exactly how to select and format each substitute value.
- Data sharing: By obscuring the data, you can prevent unauthorized access while still allowing authorized parties to view and use the information.
- Data governance: Data obfuscation is an integral part of controlling data access. Indeed, many business operations don’t require free access to actual data. If non-production environments do not need personal data, it’s best to keep sensitive information concealed – which will protect your organization from potential risks. As such, an obfuscation plan should be incorporated into your data governance framework.
Data Obfuscation Best Practices
Data obfuscation can be used to protect sensitive information from being accessed by unauthorized individuals, or to make it more difficult for attackers to exploit vulnerabilities in systems. There are a number of best practices when it comes to implementing data obfuscation in your business:
- Unless there is a specific need for your obfuscation technique to be reversible, use irreversible data masking. It is the surest way to protect sensitive data, and the masked dataset will be equally useful as test data.
- Encrypting data at rest and in transit will ensure that only authorized individuals with the correct decryption key can access the data.
- Determine the data masking techniques, rules, and formats for each piece of sensitive data. Organizing data into groups with common characteristics can simplify this process.
- Scrambling data makes it harder for unauthorized individuals to read or make sense of it. Data scrambling can be done using algorithms or by physically altering its structure (e.g., using random character strings).
- Generating false data can be used to mislead attackers or throw them off course entirely. For example, you could generate fake login credentials that would lead an attacker astray if they managed to compromise a system.
- Implementing access control measures: This limits who can access sensitive information and what they can do with it. For example, you could require users to authenticate themselves before being able to view certain files or restrict what actions they can perform on sensitive data.
To ensure successful data masking, data integrity must be preserved. This is critical for the masked data to be as useful as the original information.
Ultimately, the best way to use data obfuscation will depend on the needs of the business and the type of data involved. But with careful planning and execution, businesses can use data obfuscation to their advantage without sacrificing too much in terms of transparency or usability.
How Does a Data Obfuscation Strategy Look?
Planning, data management, and execution are all crucial components of a successful data obfuscation implementation.
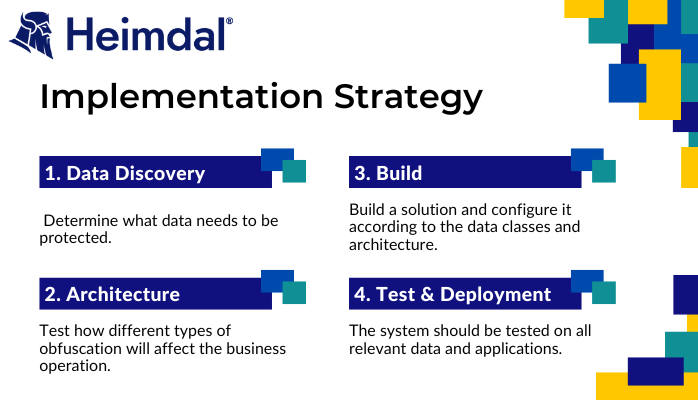
1. Data Discovery
Data obfuscation begins with determining what data needs to be protected. Each company has specific security requirements, data complexity, internal policies, and compliance requirements. In the end, this step identifies data classes, determines the risk of data breaches associated with each class, and determines whether data obfuscation can reduce those risks.
2. Architecture
It is typical for an organization to classify data into public, sensitive, and classified at the data discovery stage based on business classes, functional classes, or compliance standards.
When classes need to be obfuscated, it’s important to test how different types of obfuscation will affect the business operation, as it must continue to function normally even under continuous obfuscation.
3. Build
In this step, the organization builds a solution to perform obfuscation in practice and configures it according to the data classes and architecture that were previously defined. This includes:
- How to integrate the data obfuscation component with existing data stores and applications.
- Preparation of datasets and storage infrastructure to store obfuscated versions of the data.
- How to start the change management process.
- Defining obfuscation rules for different types of data.
4. Testing and Deployment
To ensure obfuscation is really secure and does not impact business operations, the system should be tested on all relevant data and applications once it has been built. A test datastore is created and part of the production dataset is obfuscated.
The organization must conduct user acceptance testing (UAT) as the project approaches deployment, define organizational roles for obfuscation, and create scripts to automate obfuscation.
Using data masking for data governance, risk, and compliance has many benefits. However, implementing it properly may take time and resources. By following best practices, the process will be much more efficient. By automating data masking processes wherever possible and starting with a solid strategy, you will be able to cut costs and effort.
Challenges Associated with Data Obfuscation
Data obfuscation is the process of making data unreadable or difficult to understand. It can be used to protect information from unauthorized access or to make it more difficult for someone to reverse engineer a system. However, there are several challenges associated with data obfuscation:
- Scalability: as the amount of data increases, it becomes more difficult to obfuscate all of it without affecting performance.
- Security: if the data is not properly obfuscated, it may be possible for an attacker to bypass the protection and gain access to the underlying information.
- Manageability: keeping track of which data is obfuscated and how can be difficult, especially in a large organization.
- Support: some applications and systems may not work correctly if certain types of data are obfuscated.
Specifically, here are some of the challenges for each obfuscation method:
- Encryption – It is possible to obfuscate structured and unstructured data using encryption, but format-preserving schema offer less security.
- Tokenization – It is difficult to scale the performance and security of tokenization as a database grows in size. Tokenization is strictly for structured data fields such as credit card numbers or Social Security numbers.
- Data masking – There is a downside to data masking’s great customizability: you have to customize each field to your specifications.
To Conclude…
Obtaining data obfuscation requires acknowledging that certain information is sensitive. Data obfuscation is an important tool to have in your business arsenal. It helps you protect sensitive customer data and can also be used to increase the security of internal databases. By understanding what it is, how it works, and how it relates to other security measures, you can ensure that your data remains secure from malicious actors. With the right implementation of data obfuscation techniques, you can rest assured that no one will be able to access or misuse your valuable customer information, even if they were able to breach your systems.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security