Contents:
A few months ago, my colleague Bianca Soare wrote a very comprehensive article on what virus and worm mean. Understanding what the terms virus, worm and malware refer to is the perfect starting point for understanding how the Crypto Virus (and other ransomware) works, so let us have a closer look. Malware is the umbrella that accommodates all these terms, as we also mention in our Cybersecurity Glossary: This is a short version for “malicious software” and it works as an umbrella term that refers to software that is defined by malicious intent. This type of ill-intentioned software can disrupt normal computer operations, harvest confidential information, obtain unauthorized access to computer systems, display unwanted advertising and more. Viruses can be defined as follows: A computer virus is a type of malicious software capable of self-replication. A virus needs human intervention to run and it can copy itself into other computer programs, data files, or in certain sections of your computer, such as the boot sector of the hard drive. Once this happens, these elements will become infected. Computer viruses are designed to harm computers and information systems and can spread through the Internet, through malicious downloads, infected email attachments, malicious programs, files, or documents. Viruses can steal data, destroy information, log keystrokes and more. Ransomware, on the other hand, […] is a type of malware (malicious software) which encrypts all the data on a PC or mobile device, blocking the data owner’s access to it. After the infection happens, the victim receives a message that tells him/her that a certain amount of money must be paid (usually in Bitcoins) in order to get the decryption key. Usually, there is also a time-limit for the ransom to be paid. There is no guarantee that, if the victim pays the ransom, he/she will get the decryption key.
What is Crypto Virus? Crypto Virus Definition
By definition, a Crypto Virus is […] a computer virus that contains and uses a public key. Usually, the public key belongs to the author of the virus, though there are other possibilities as well. For instance, a virus or worm may generate and use its own key pair at run-time […]. Crypto viruses may utilize secret sharing to hide information and may communicate by reading posts from public bulletin boards […]. Crypto trojans and crypto worms are the same as crypto viruses, except they are Trojan horses and worms, respectively. Note that under this definition, a virus that uses a symmetric key and not a public key is not a cryptovirus […]. A Crypto virus encrypts files on the computers it infects and then broadcasts a message in which a fine is demanded in order to regain access to the files. There is also a time limit in which the money can be paid before the files are ultimately destroyed for good. A key element (pun intended) in understanding how Crypto viruses and ransomware work is the concept of keys. It comes from the cryptography domain – “the practice and study of techniques for secure communication in the presence of third parties called adversaries.” Symmetric-key cryptography, the only encryption type generally known until June 1976, is an encryption method in which the sender of the communication and the receiver share the same key.
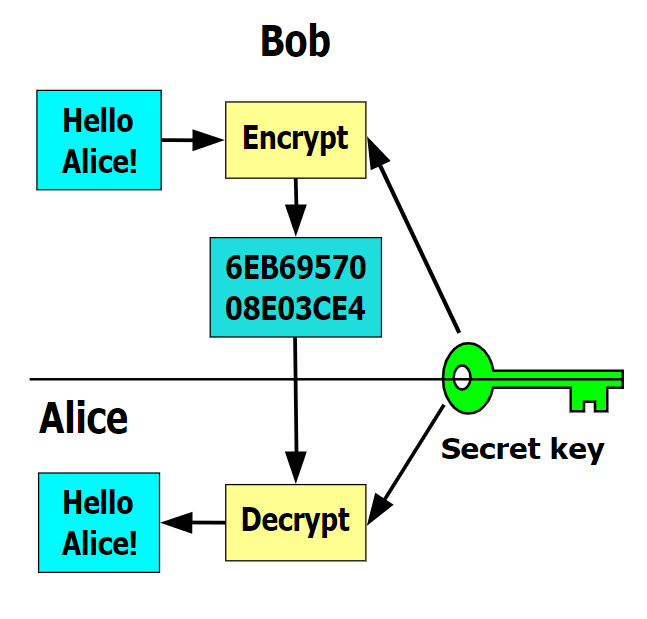
In 1976, the notion of public or asymmetric-key cryptography appeared. In this case, two different but mathematically related keys are used—a public key and a private key. A public key system is so constructed that calculation of one key (the ‘private key’) is computationally infeasible from the other (the ‘public key’), even though they are necessarily related. Instead, both keys are generated secretly, as an interrelated pair. […] In public-key cryptosystems, the public key may be freely distributed, while its paired private key must remain secret. In a public-key encryption system, the public key is used for encryption, while the private or secret key is used for decryption.

Ransomware, on the other hand, which is also called “cryptoviral extortion”, uses the following protocol:
- [attacker→victim] The attacker generates a key pair and places the corresponding public key in the malware. The malware is released.
- [victim→attacker] To carry out the cryptoviral extortion attack, the malware generates a random symmetric key and encrypts the victim’s data with it. It uses the public key in the malware to encrypt the symmetric key. This is known as hybrid encryption and it results in a small asymmetric ciphertext as well as the symmetric ciphertext of the victim’s data. It zeroes the symmetric key and the original plaintext data to prevent recovery. It puts up a message to the user that includes the asymmetric ciphertext and how to pay the ransom. The victim sends the asymmetric ciphertext and e-money to the attacker.
- [attacker→victim] The attacker receives the payment, deciphers the asymmetric ciphertext with the attacker’s private key, and sends the symmetric key to the victim. The victim deciphers the encrypted data with the needed symmetric key thereby completing the cryptovirology attack.
If you want to read more on how ransomware works, our blog contains dozens of articles focusing on specific types and ransomware attacks. Petya, Ryuk, Sodinokibi and the famous WannaCry are just a few examples.
What Were the Most Famous Crypto Virus Examples?
1. CryptoLocker
CryptoLocker is usually the most common example of Crypto Virus attack. It emerged in September 2013 and continued until May the following year. However, CryptoLocker could not multiply itself as a virus would. It spread by using the notorious Gameover ZeuS botnet – a network of compromised computers remotely controllable by the botnet’s operator, without the consent or even knowledge of the owners. The CryptoLocker attack targets got infected by downloading and opening malicious email attachments that then executed the malware hidden inside. CryptoLocker did use, though, an asymmetric encryption method. The cybercriminals kept for themselves both the public and the private keys. During the CryptoLocker sustained attack, roughly 500,000 computers around the world were affected and the victims who agreed to pay brought the CryptoLocker team around $3 million. Among the devices compromised by CryptoLocker, there were even “two NASA computers, according to an internal document obtained by Motherboard. The ransomware […] infected a computer at the NASA Ames Research Center in California on October 23, 2013, <<resulting in the loss of access to NASA data,>> according to the document. It also hit another computer at the visitor center of the Kennedy Space Center in Florida two days later.”
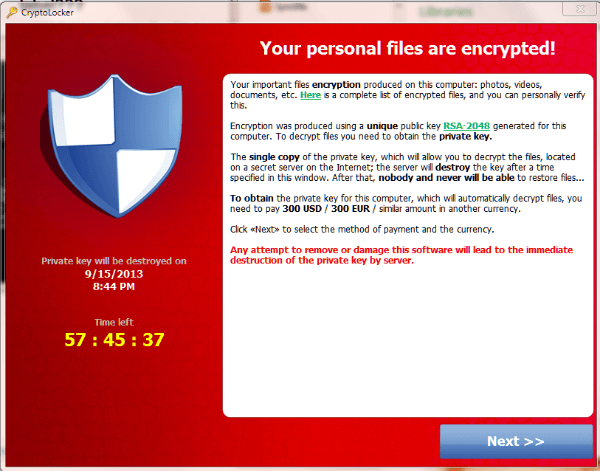
Fortunately, the two computers were fully backed up – “This is standard practice at NASA, where <<95% of data is SBU [sensitive but unclassified] and everything is backed up in triplicate […]>>”. As it is recommended, NASA did not agree to pay the ransom. CryptoLocker ended with Operation Tovar, during which an international coalition of law enforcement agencies took down the GameOver ZeuS botnet.
2. CryptoWall
CryptoWall is another famous example of a Crypto Virus. It usually spread through email as a malicious attachment or through infected websites and it has even been linked “to some ad sites that serve up advertising for many common websites users visit on a daily basis, further spreading its distribution.” In a CryptoWall infection, all files matching the CryptoWall’s predetermined list of supported file extensions will get copied. As copies are created, the files are encrypted using a public key, while the originals are deleted from the hard drive. The process also includes the files located on external drives and network shares – “basically, any drive that’s assigned a drive letter will be added to the list. Also, cloud-based storage that stores a local copy of the files on the drive will be affected, and changes will propagate to the cloud as the files are changed”. Moreover, “once the encryption process has completed, CryptoWall will execute some commands locally to stop the Volume Shadow Copy Service (VSS) that runs on all modern versions of Windows. VSS is the service that controls the backup and restoration of data on a host computer. It also controls file versioning, a feature introduced in Windows 7 that keeps histories of changes made to files. The file may be rolled back or restored to a previous version in the event of an unintended change or catastrophic event that causes the integrity of the file to have been modified. The command run by the virus stops the service altogether and also adds the command argument to clear/delete the existing cache, making it even more difficult to recover files through versioning or system restore.” As InfoSecurity notes, CryptoWall has caused $325 million in damages.
Ransomware & Crypto Virus – Prevention Strategies
Although ransomware and Crypto Virus attacks have different M.O.’s, their consequences are similar. Because of the attack, their victims will lose time, money, files, maybe even business partners and clients, not to mention that a data breach also leads to brand damage and possible legal actions due to non-compliance. The good part is that all these nuisances can be avoided by taking a few prevention measures:
Patch, patch, patch
Unpatched software known vulnerabilities represent open doors for cybercriminal’s malware. It’s important to always keep your operating system and the applications you use up to date. In order to help your company streamline the patching process, we have developed Heimdal™ Patch & Asset Management, a patch management solution for Windows and 3rd party software.
Use a powerful antivirus solution
Antivirus solutions are essential for the protection of a company’s systems. Our Heimdal™ Next-Gen Antivirus & MDM will use signature-based code scanning to monitor the activity of your organization’s files in order to protect your endpoints against malware, ransomware, APTs and other types of threats. You can perform file scans in real-time, as a permanently active process, or you can run scheduled or on-demand scans for your endpoints to detect any suspicious activity.
Use a firewall too
Firewalls can also prove extremely helpful in avoiding ransomware attacks. Heimdal™ Next-Gen Antivirus & MDM’s firewall component prevents incoming attacks by monitoring login activity, stops brute force attacks, and lets you isolate devices if necessary.
Protect your email
Many crypto viruses and ransomware attacks start with an unfortunate email that has malicious attachments – which are ultimately downloaded and opened. For this reason, email protection is a really necessary addition to any cybersecurity strategy. Our Heimdal™ Email Security can help you avoid malware, malicious URLs and prevent phishing and ransomware. Heimdal® Email Security
Show hidden file-extensions
CryptoLocker is usually spread, for example, through files that have the extension “.PDF.EXE”, because Windows hides by default known file extensions. Re-enable the option to see the full extensions and you will be able to avoid threats much easier.
Browse safely
It’s important to make sure that the browsers your company uses are up to date and use encryption. Moreover, ads and JavaScript should be disabled by default. You can find more tips on browser security in one of our previous articles.
Back up, back up, back up
Having your data backed up is an essential security measure not only when it comes to avoiding the unpleasant consequences of a Crypto Virus or ransomware, but also in case of theft or natural accidents. More advice on backups here.
TRAIN YOUR EMPLOYEES!
Your employees must know the basics of cybersecurity threats and how to avoid them. As Security Boulevard mentions, “security awareness training shouldn’t be treated as something separate but should be built into each person’s job duties. Once employees at any level see how security awareness fits into their responsibilities, security best practices will be built in and become second nature.”
Wrapping Up
As we have seen, both ransomware and all variants of Crypto Virus have dangerous (potential) consequences for any company that becomes a target. Don’t forget that prevention is the best defense! Also, please remember that Heimdal™ Security always has your back and that our team is here to help you protect your home and your company and to create a cybersecurity culture to the benefit of anyone who wants to learn more about it. Drop a line below if you have any comments, questions or suggestions – we are all ears and can’t wait to hear your opinion!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











