Contents:
Privileged access management (PAM) tools have changed a lot over the last few years. Once, you could rely on a fairly standard set of features across all providers.
Now, the unique security challenges of cloud technology have ushered in a whole range of new tools and acronyms.
From PASM to PEDM, CIEM, secrets management, and more, understanding what tools and products you need isn’t an easy task.
And if you’re trying to identify the best PAM product for your business, BeyondTrust and CyberArk are some of the most well-known privileged access management solutions on the market.
But despite offering a sophisticated set of security tools, there are plenty of reasons to think twice about whether these products are right for you. In this blog, we discuss the pros and cons of both PAM providers and the best alternatives you can consider.
BeyondTrust: Pros and Cons for PAM
BeyondTrust is one of the biggest players in the PAM scene, with thousands of customers spread around the world. The company offers a wide range of PAM features and functionality, across several different products. Here are two of the most important:
- Privileged Remote Access (PRA) – Including features to manage privileged access, secure remote access, manage privileged sessions, and authenticate users. This is the core PAM product and generally focuses on more traditional PASM tools.
- Password safe – Includes some real-time session management features, as well as credential, key, and secrets management.
- Endpoint privilege manager – This is essentially the suite of privileged elevation and delegation management (PEDM) tools. It also includes features to control application usage and to defend against ransomware.
While these are two separate products, there’s a good degree of crossover in the functionality they offer. Indeed, they’re intended to be used together and can be purchased as part of the ‘Total PASM’ bundle.
In this piece, we’ll compare features across both security solutions – but it’s important to be aware that both will be needed to get the full functionality that’s available.
BeyondTrust is generally considered an enterprise-grade tool. Its customers are often global businesses with complex IT environments across both cloud and on-premises systems.
The platform therefore offers a wide range of tools, support, and features to help these companies effectively secure their IT networks. Main features include:
- Password management;
- Session management;
- Threat detection and response;
- Privilege elevation;
- Secure credential storage;
- Remote secure access for users and 3rd parties;
- Centralized reporting and management
BeyondTrust: Pros
When users and analysts praise BeyondTrust, they generally focus on the breadth of tools on offer. Together, the products offer some of the most extensive security support and functionality on the market.
- Product capabilities – BeyondTrust’s various products combine to offer an extensive suite of PAM tools. This includes privileged account and session management (PASM) as well as more recent innovations like privileged accounts and delegation management (PEDM), cloud infrastructure entitlements management (CIEM), and secrets management.
- Support – Users can use BeyondTrust’s products on a wide range of systems, including UNIX, Linux, macOS, and Windows, across cloud, hybrid, and on-premises environments.
- Discovery – Users and reviewers generally rate the strength of the discovery capabilities, saying they are easy to use and can effectively identify endpoints and accounts.
BeyondTrust: Cons
BeyondTrust certainly offers a sophisticated set of features. But that doesn’t mean it’s the right product for every organization.
The menu system is a bit dated. Sometimes the application takes a little longer than expected to load. It has a somewhat clunky interface and some areas can accidentally be clicked causing issues due to no pop-up warning.
BeyondTrust User Review, via TrustRadius
- Too many licenses – BeyondTrust functionality is split across a confusing array of different tools. As well as the three discussed above, there are also several legacy products (such as Cloud Privilege Access Broker), that duplicate the functionality in these products. The overlapping and opaque featureset creates confusion and often requires multiple licenses, which increases costs.
- Price – BeyondTrust doesn’t publish pricing information, but reviewers and analysts consistently report that it’s one of the most expensive tools on the market. This is also particularly the case when you account for the multiple licenses you’ll need to get full coverage.
- PEDM functionality – PEDM functionality isn’t fully integrated into the Total PASM package, which can increase the number of licenses an organization needs. Even in the Endpoint Privilege Manager product, important tools are missing, such as multi-factor authentication as well as the ability to dynamically elevate permissions for specific files, folders, and applications.
- Integrations – BeyondTrust tools also lack vital integrations with DNS, antivirus and firewall, and ransomware encryption protection tools. This can make effective compliance and risk management a challenge.

CyberArk: Pros and Cons for PAM
CyberArk’s PAM offering is similar to BeyondTrust in many ways. First, it explicitly targets global enterprises and has a broad set of features to accommodate this market position. Generally, its products are also among the most expensive on the market as a result.
CyberArk also splits its functionality across multiple tools, though the package is generally more straightforward than with BeyondTrust. Here’s what’s on offer:
- Privileged access manager – This is CyberArk’s standard PASM offering. It involved features to manage privileged credentials, including the enterprise password vault, privileged session manager, privileged vault web access, and a central policy manager.
- Endpoint privilege manager – Contains a range of tools to manage the tools of specific endpoints. These help IT teams reduce their attack surface and implement least privilege. This is essentially the PEDM offering.
CyberArk also has a range of other tools that customers can purchase as bolt-ons, including products to manage identity, governance, and administration (IGA) and secrets management. In this section, we’ll focus on the features available through their main PAM suite.
CyberArk has been one of the biggest players in the PAM scene for decades. In fact, it pioneered many of the tools that have since become commonplace in other products, such as secrets management and CIEM functionality.
But like BeyondTrust, the size and enterprise focus of the company creates a few downsides, largely coming down to the cost and complexity of the product – as well as the number of different licenses needed to achieve full coverage.
CyberArk: Pros
Much of CyberArk’s strength comes from its large customer base, partner ecosystem, and long heritage in the industry.
- Scale – CyberArk has the largest market share for PAM products. This allows it to be responsive to market changes and effectively support the complex, multi-faceted environments of global enterprises.
- PAM innovations – CyberArk is proactive in bringing new features to market. This includes tools like just-in-time access, CIEM, secrets management, and more.
- Partner ecoystem – CyberArk has a large partner ecosystem and offers a wide range of integrations with other technologies.
CyberArk: Cons
It is complex to install and upgrade. Vendor engagement is a must for installation.
CyberArk User Review, via G2
As you can expect from a company CyberArk’s size, it’s not plain sailing for all users. While powerful, the products can be confusing and difficult to use:
- Price – While CyberArk doesn’t publish pricing information, it’s consistently reported to be one of the most expensive products on the market.
- Complex and rigid – CyberArk’s products are complex to use. Users often mention that the features are difficult to configure, maintain, and upgrade. Generally, they’re more suited to security teams with specific technical expertise.
- Overlapping products – Like BeyondTrust, CyberArk splits its PAM functionality over several separate subscriptions. As well as increasing costs, this also makes it difficult to work out which products and features the customer needs.
- Technical support – CyberArk’s support is generally less effective than its competitors. In fact, Gartner rated them among the lowest of all providers analyzed in the 2023 magic quadrant.
BeyondTrust vs. CyberArk: Reviews
BeyondTrust and CyberArk’s PAM products are both well-represented on online review sites. Here are some of the headline review scores:
Gartner:
- BeyondTrust: 4.4/10 (880 reviews total)
- CyberArk: 4.5/5 (232 review total)
G2:
- BeyondTrust: 4.4/5 (30 reviews total)
- CyberArk: 4.5/5 (61 reviews total)
TrustRadius:
- BeyondTrust: 9.1/10 (29 review total)
- CyberArk: 8/10 (60 reviews total)
Both products are clearly popular among their users. But by digging through the details of the reviews, we can understand a little more about what specifically users appreciate about both platforms – and where they fall short.
For BeyondTrust, much of the positive praise came down to the platform’s sophisticated set of PAM features, and the breadth of support offered – particularly concerning third-party users. Users also highlighted its ability to audit privileged accounts, create data trails, and ensure compliance with regulatory requirements.
This is all consistent with BeyondTrust’s reputation as a sophisticated PAM tool for enterprises.
BeyondTrust Privileged Remote Access allows us to grant secure remote access to specific resources in our internal networks to those external partners. It supports many types of applications and has a good granularity in terms of the types of privileges you can allow.”
BeyondTrust User Review, via TrustRadius
But as we’ve discussed above, there are also several drawbacks. The themes here are remarkably consistent from review to review. Users who highlighted the downsides of the platform generally focused on the high price and complexity of the product, as well as the layout of the user interface.
The price for a product like this is higher than most. If you’re on a budget, you probably can’t justify the higher cost.
BeyondTrust User Review, via G2
For CyberArk, the feedback was generally quite similar. Users praised the featureset and ability to keep complex environments secure. They also drew particular attention to the strength of the password management capabilities.
It allows our IT personnel to use their privileged accounts without having to remember their passwords. It also keeps our staff compliant with the complexities of passwords.
CyberArk User Review, via TrustRadius
But like BeyondTrust, ease of use was the most common drawback mentioned by reviewers. Generally, they conclude that an experienced security team is needed to effectively configure and maintain the product. They also mentioned that the high cost of the product was another key drawback,
Configuration is a bit too complicated. It will need a good experienced team to support it.
CyberArk User Review, via G2
All in all, BeyondTrust and CyberArk are both well-liked among their customer bases. But many of their pros and cons are the same, meaning there’s ultimately not a great deal to choose between them. With either product, you can expect a sophisticated set of cybersecurity features. But in both cases, the trade-off is going to be a platform that’s expensive and difficult to manage.
At the same time, there’s a good chance you’re going to need to purchase multiple subscriptions to get the full coverage.
Ultimately, both products are designed for large enterprises with highly developed security teams. If that’s not the case for your business, there’s a good chance you’ll be better off looking elsewhere.
Heimdal: The Best Alternative to BeyondTrust and CyberArk
If you’re on the lookout for an alternative to BeyondTrust or CyberArk, you’re not alone. In fact, there are plenty of businesses that find these products prohibitively expensive and confusing.
Instead, why not try something else? With Heimdal®, you get access to a single unified security platform for all your cybersecurity functionality.
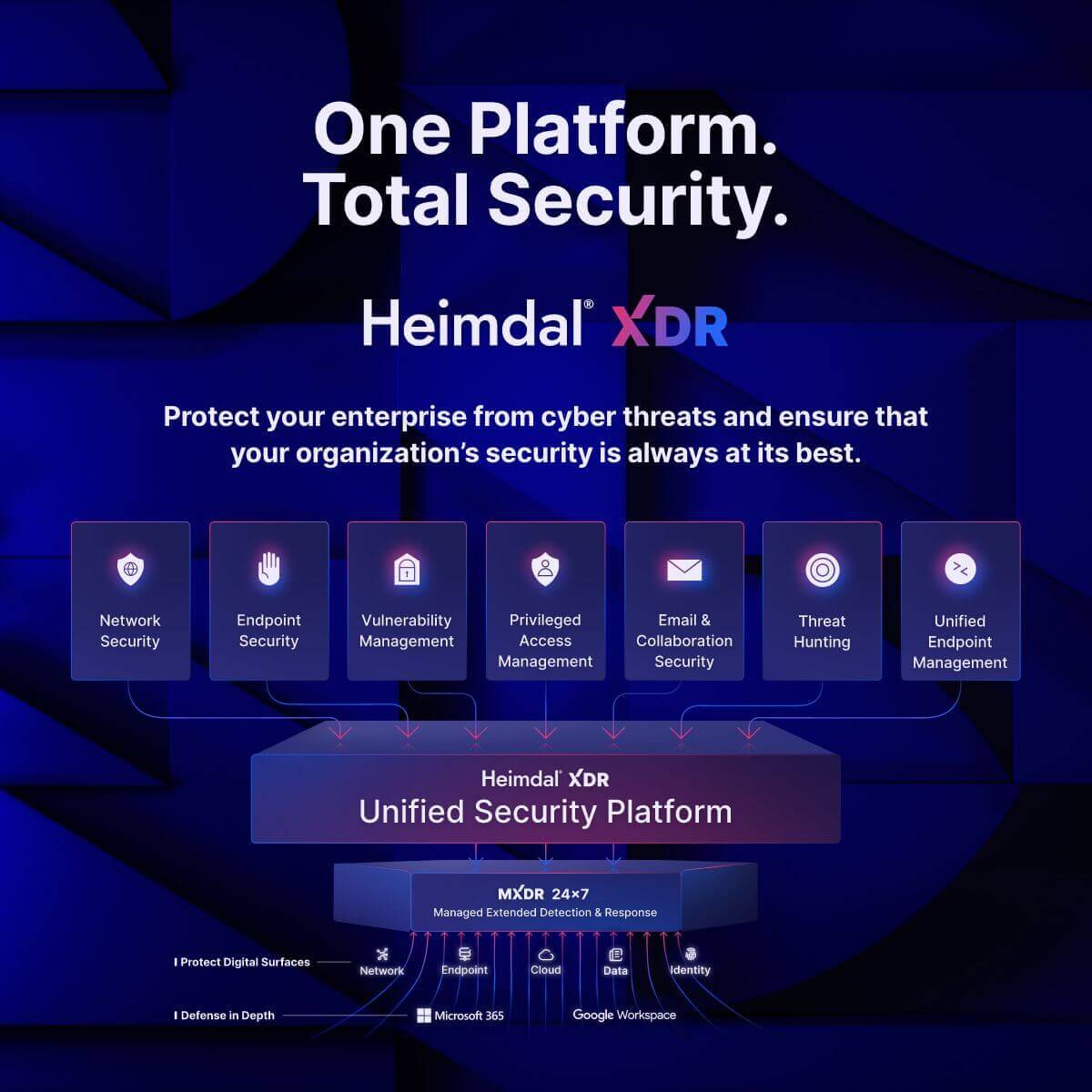
Like the products we describe elsewhere in this blog, Heimdal® offers some of the most sophisticated PASM and PEDM functionality on the market. But unlike these platforms, it’s not just a siloed PAM product. Instead, it comes as part of a wider suite of security services, all available from a single unified dashboard. Here’s what that includes:
- Network security;
- Endpoint security;
- Vulnerability management;
- Privileged access management;
- Email and collaboration security;
- Threat hunting;
- Unified endpoint management.
So why should you choose Heimdal® over CyberArk or BeyondTrust? Here’s what you need to know:
One Product, One License
BeyondTrust and CyberArk both require customers to buy multiple licenses just to get the full range of PAM functionality. That doesn’t even include other areas of cybersecurity. With Heimdal®, you get a single license and a single platform – eliminating confusion and redundant licenses once and for all.
It’s Not All About PAM
BeyondTrust and CyberArk are sophisticated PAM products. But they’re not designed to handle vulnerability management, endpoint detection – or a whole range of other cybersecurity tasks. Heimdal® is a one-stop shop for all your cybersecurity needs, with flexible modules across the whole range of standard security functionality.
No More Prohibitive Costs
BeyondTrust and CyberArk are some of the most expensive products on the market. With Heimdal, you get simple, scalable, and affordable licensing.
With CyberArk and BeyondTrust, you get access to a single provider for just your PAM needs, often split over a confusing array of different products and services. With Heimdal®, you get a single platform and license for all your cybersecurity needs – with the same sophisticated PAM features that you need to stay secure.
Get in touch to request your demo today.
BeyondTrust vs CyberArk: FAQs
What is the difference between BeyondTrust and CyberArk?
BeyondTrust and CyberArk are both established cybersecurity vendors that provide specialist privileged access management tools.
Both are targeted towards enterprises and generally offer a sophisticated set of features. Users of BeyondTrust generally appreciate the strength of the PASM and PEDM features,, as well as the reporting capabilities. CyberArk is generally praised for the strength of its password management features.
Is CyberArk the best PAM product?
CyberArk tends to be the preferred options for large global enterprises with established security teams. For other organizations, the platform can be prohibitively expensive and complicated and require too many overlapping licenses to gain full protection. For this reason, many potential customers prefer to look elsewhere.
What is BeyondTrust used for?
BeyondTrust is a cybersecurity platform that allows you to implement proactive protections to protect privileged data. Users can achieve this by controlling privilege, access, credentials, and secrets.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security












