Contents:
Looking for the best zero trust solutions in 2026? We’ve got your back.
In this article, we’ll discuss the best options available to help you make an informed decision.
Here’s a quick glance for you:
- Heimdal XDR: Best platform. Enhances security by adopting a Zero Trust model, ensuring that only essential permissions are granted to users and applications.
- Zscaler: Best for cloud-native security. Provides integrated security stack including SWG, cloud firewall, DLP, sandboxing, and SSL inspection for comprehensive threat detection.
- Fortinet: best for granular access control. Offers fine-grained access policies for remote and in-office users with continuous trust verification.
- Crowdstrike Falcon Zero Trust: Best for endpoint security. Delivers advanced endpoint security and real-time threat detection through a cloud-native architecture.
- Cloudflare: Best for performance optimization. Integrates performance optimization with robust DDoS protection to enhance both security and speed.
- Perimeter 81: Best for Remote Workforce Security. Simplifies and secures remote access to company networks and resources, ideal for dispersed workforces.
- Palo Alto Zero Trust: Best for firewall capabilities. Utilizes next-gen firewall technology and threat intelligence for secure cloud resource access and management.
- Okta Identity-Driven Security: Best for identity-driven security. Uses a sign-on system to securely connect users with technology, supporting identity lifecycle management and adaptive authentication.
- JumpCloud Open Directory Platform: Best for cross-OS management. Manages cross-OS servers, devices, and user identities from a single interface with strong integration options.
- BeyondTrust: Best for comprehensive IAM and endpoint security. Offers a range of zero trust solutions for identity and access management and endpoint security with detailed audit trails.
Best Zero Trust Solutions (2026)
1. Heimdal XDR
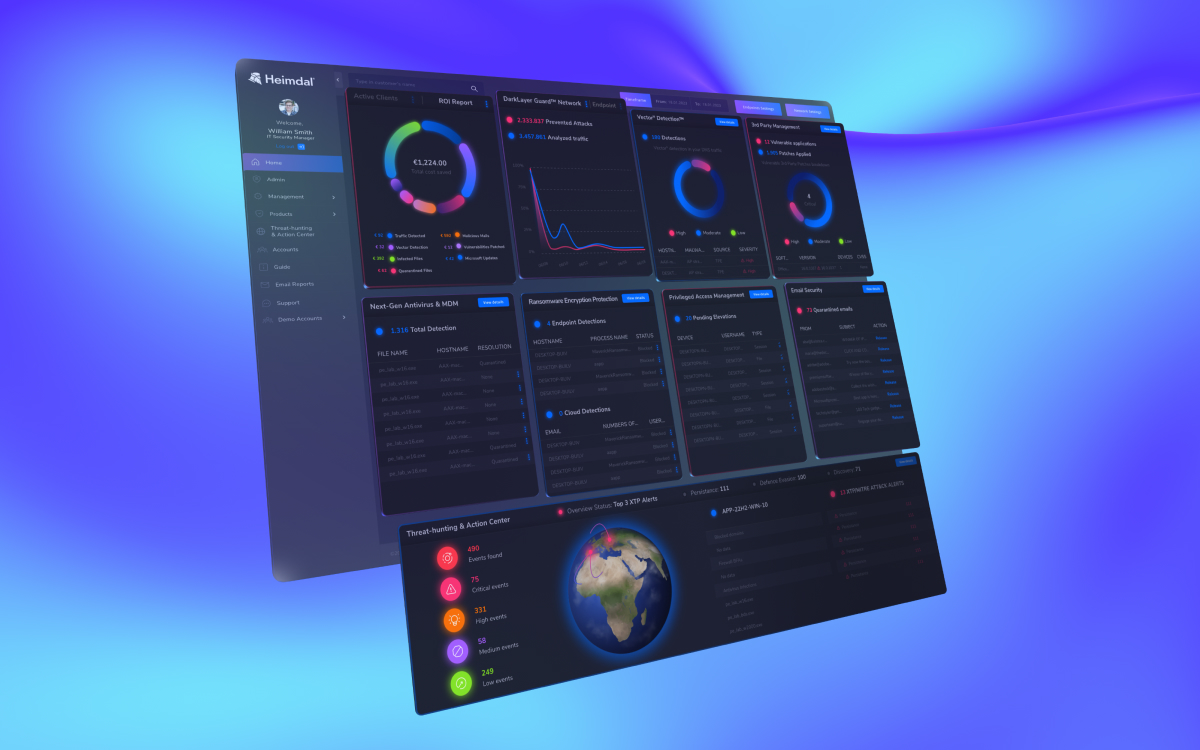
If you are looking for a solution that puts your security on first place and enhances its products with the Zero Trust model, look no further than Heimdal’s XDR platform, the widest cybersecurity platform on the market today.
A highlight from the platform is the Heimdal’s Privilege Elevation and Delegation Management (PEDM) solution enhances security by adopting a Zero Trust model, ensuring that only essential permissions are granted to users and applications.
This approach significantly reduces the risk of unauthorized access and minimizes potential attack surfaces within an organization.
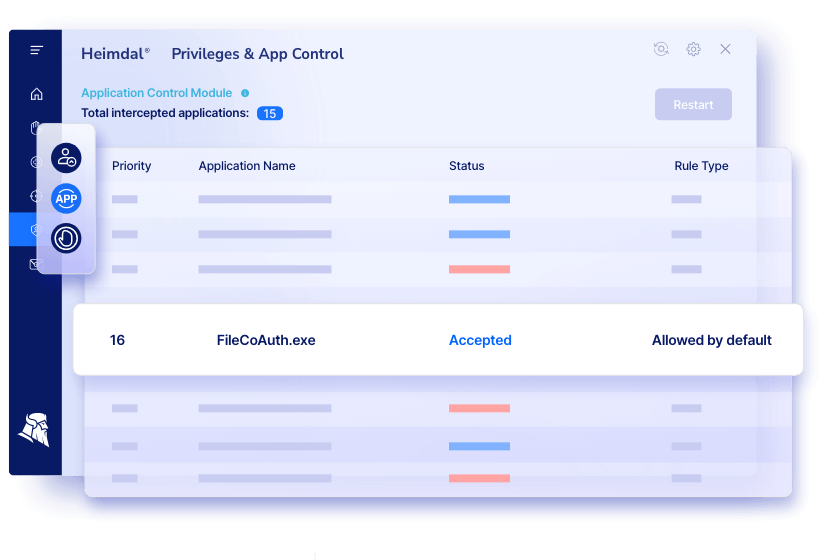
By leveraging Heimdal PEDM, IT professionals, system administrators, and security teams can seamlessly manage and elevate privileges based on user roles. The solution ensures that authorized individuals have the necessary access while preventing privilege abuse, aligning with Zero Trust principles.
The Zero Trust security model operates on the principle of “never trust, always verify,” meaning that no user or application is inherently trusted, regardless of their location within or outside the network.
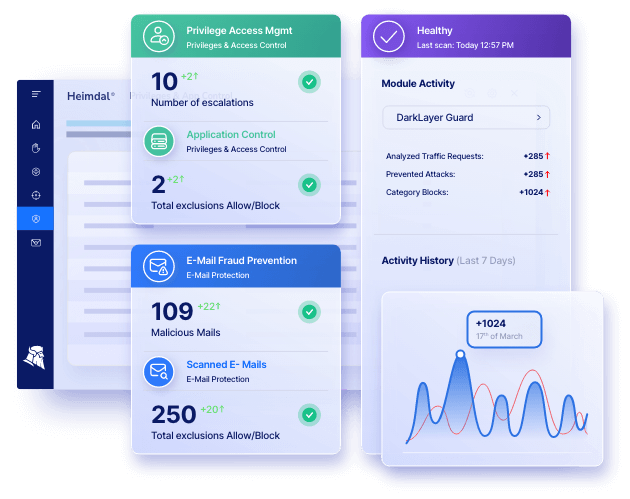
Heimdal’s PEDM solution implements this by granting just-in-time access, providing temporary elevated privileges only when necessary, and enforcing strict access controls. This proactive approach mitigates the risks associated with prolonged exposure to privileged access, thereby enhancing the organization’s security posture.
Key Features:
- Effortless Zero Trust Implementation: Grants users and applications only the essential permissions they need, significantly decreasing the risk of unauthorized access and minimizing potential attack surfaces.
- Unified Access Management: Provides meticulous control over user privileges from a single platform, empowering security specialists to efficiently escalate and de-escalate user and application rights. It enables the definition of flexible user group policies and the management of local admin rights.
- Regulatory Compliance: Offers comprehensive reporting and auditing capabilities to demonstrate compliance with standards such as Cyber Essentials, GDPR, and NIST. This feature generates necessary audit trails to ensure adherence to relevant regulations.
- Total Privilege Management: Defines and manages role-based access controls and delegation policies. Approves or denies privilege requests through an intuitive dashboard or mobile device, tracks sessions, prevents elevation for system files, revokes admin rights in real-time, sets escalation periods, and terminates processes after session expiration.
- Just-in-Time Secured Privilege Access: Implements just-in-time access controls, granting temporarily elevated privileges to users only when necessary. This feature effectively mitigates the risk of prolonged exposure to privileged access and reduces attack surfaces, including vulnerabilities in Microsoft 365 operating systems.
- Unparalleled Reporting & Compliance: Generates comprehensive reports and tracks privileged access/session activities, ensuring compliance with international or regional regulatory requirements. Facilitates seamless audits.
- Seamless Integration: Integrates with Heimdal Endpoint and DNS solutions to contain threats and prevent lateral spread. Enhances security posture with Heimdal Application Control for advanced software management and incorporates tools like ServiceNow for improved efficiency and control.
Pros:
- Provides unified control over user privileges with easy escalation and de-escalation.
- Comprehensive reporting and auditing capabilities ensure adherence to standards like GDPR and NIST.
- Grants temporary elevated privileges only when necessary, reducing prolonged exposure to risks.
- Integrates with Heimdal Endpoint, DNS solutions, and other tools like ServiceNow for enhanced efficiency and security.
Cons:
- New users may require some time to become proficient due to the learning curve.
- A stable internet connection is essential for effective operation.
Pricing:
Prices are flexible based on seat count (1–20,000+) and server count (1–100+), with discounts available for multi-year subscriptions and combined DNS Security for Perimeter and Endpoint.
The product does so much and quite well. The value for everything is outstanding. With the latest version that’s in RC, one could argue it could replace your RMM too as they’ve added BitLocker management and scripting. –the agent is very lightweight, easy to install/manage –threat investigation is quite good. Coming from SentinelOne I find it easier to dig deep into an issue –SOC is very responsive, support is great.
2. Zscaler
Zscaler’s integrated security stack includes SWG, cloud firewall, DLP, sandboxing, and SSL inspection to prevent unauthorized access. It uses machine learning for threat detection, inspecting all traffic, including encrypted traffic, for malicious content.
Microtunneling establishes secure connections for individual user requests.
The Zscaler Private Access (ZPA) service secures access to private applications and services, adapting authorization dynamically based on user location, device type, application access history, and threat intelligence. ZTE integrates with existing Identity and IAM solutions and IDPs.
Key Features:
- Integrated Cloud Security: Emphasizing integrated cloud security, Zscaler’s ZTNA solutions secure access to cloud applications and services.
- User and Device Context: Zscaler enhances security measures by incorporating user and device context into access decisions.
- Cloud-Native ZTNA: Known for its cloud-native approach, Zscaler offers scalable and flexible Zero Trust Network Access solutions.
- Secure Web Gateways: Zscaler’s Zero Trust solutions include secure web gateways to protect against web-based threats and ensure safe internet access.
Pros:
- Provides customizable, granular access controls.
- Offers advanced security features.
Cons:
- Needs a fast internet connection for proper functioning.
- Advertised number of PoPs may not apply to all services.
Pricing:
It offers customized pricing which requires a consultation call.
Zscaler is great, but I’m not convinced their infrastructure team is all that skilled or properly funded. Some really basic issues popped up in some of the countries where we deployed it. But it can be as invasive or not as your company wants it to be just like the cisco vpn. Many companies automatically pass through medical related websites so that never shows up in your history. and any security team would never tell anyone what they saw when reviewing the logs as it’s a breach of ethics.
3. Fortinet Zero Trust Network Access
Fortinet’s Zero Trust Network Access (ZTNA) allows network and security teams to enforce fine-grained access policies for both remote and in-office users. It can control access to applications hosted on-premises, in the public cloud, or delivered via SaaS.
Operating from a least-privilege stance, Fortinet ZTNA restricts users to only the applications and services permitted by their role. Access policies can also be based on device type, location, time of day, and device posture.
Trust is verified with each access attempt, not just during the initial connection, ensuring that any changes in privilege are enforced immediately.
Key Features:
- Flexible Deployment: Enables ZTNA policy enforcement for the entire workforce, anytime and anywhere.
- Granular Access Control: Grants users and devices access to specific applications within predetermined parameters and permissions.
- Ongoing Verification: Verifies user identity, device identity, device security posture, and user access rights prior to granting application access.
- Client-Initiated Model: Provides continuously validated, secure access to applications, improving endpoint security (visibility and control) and user experience (prioritizing performance of mission-critical applications).
- Integrated Capability: Fortinet’s ZTNA requires no additional licenses or cost, as it is an embedded feature in FortiOS and FortiClient, allowing organizations to transition from VPN access to ZTNA at their own pace.
- Automatic Encrypted Tunnels: Automatically creates TLS-encrypted tunnels from endpoints to the access proxy, allowing agencies to inspect network traffic while ensuring it is hidden from unauthorized users or devices.
Pros:
- Powerful and reliable SD-WAN Services.
- Industry-validated powerful IPS Services.
Cons:
- Forti DNS server may become unavailable at times.
- Their log service has room for improvement.
Pricing:
It offers customized pricing.
It takes a lot of buy-in to the ecosystem to get the most out of it. In certain situations, that’s great, in others, not so much. My main issue with fortinet at the moment is the stream of CVE’s. For being such a security focused company, their firmware QA seems really lacking lately. So, I recommend them, but I only deploy them when I require features. They are the only reasonable option for, and there’s a good buy-in on the ecosystem.
4. CrowdStrike Falcon Zero Trust
CrowdStrike offers Zero Trust protection for hybrid enterprise workloads, multi-OS endpoints, and various directories such as Microsoft Active Directory and Azure Active Directory. This solution enables security teams to achieve robust Zero Trust without the need to handle large volumes of data, threat feeds, hardware, or software.
It replaces VPNs by granting authorized users unrestricted internet access. CrowdStrike’s Security Cloud, renowned in the industry, simplifies the implementation of seamless Zero Trust for businesses of all sizes, eliminating operational complexities.
Key Features:
- Endpoint Security Excellence: CrowdStrike leverages its expertise in endpoint security to offer advanced protection at the device level through its Zero Trust offerings.
- Real-Time Threat Detection: CrowdStrike integrates real-time threat detection into its Zero Trust solutions, swiftly responding to security incidents and minimizing the impact of cyber threats.
- Cloud-Native Architecture: CrowdStrike ensures flexibility and scalability in its Zero Trust Network Access solutions by embracing a cloud-native architecture.
- Behavioral Analytics: CrowdStrike enhances security effectiveness with behavioral analytics, identifying and mitigating anomalous activities through its Zero Trust solutions.
Pros:
- Silent agents with minimal impact on computation and user notifications.
- Strong interoperability with other AVs or EDRs, operating smoothly without conflicts.
- Handles large asset information comfortably without browser lag.
Cons:
- UI changes in Falcon Management Console complicate instructional document maintenance.
- Lacks basic AV features like On-Demand Scan on non-specific Windows versions.
- Machine Learning alerts are sometimes overwhelmed with excessive information, requiring extensive investigation.
Pricing:
It starts at $99.99 annually per device.
My experience with CS was incredible. The product is pricey, and certain add-ons are pricier than they should be IMO, but the product was super solid for me.
5. Cloudflare Zero Trust
Cloudflare operates globally, offering integrated Zero Trust solutions that enhance both security and performance. With a specific emphasis on safeguarding cloud resources and providing robust DDoS protection, Cloudflare enables organizations to securely access and manage their digital assets across distributed networks.
By replacing traditional security perimeters with its expansive global network, Cloudflare makes the internet faster and safer for teams worldwide.
Key Features:
- Performance Optimization: Cloudflare integrates performance optimization into its Zero Trust offerings, leveraging its content delivery network (CDN) services to enhance both security and speed.
- Zero Trust for Cloud Resources: Specializing in securing cloud resources, Cloudflare offers organizations a robust framework for securely accessing and managing assets hosted in the cloud.
- Distributed Denial of Service (DDoS) Protection: Cloudflare’s Zero Trust solutions include features for DDoS protection, effectively safeguarding organizations against disruptive cyber attacks.
Pros:
- Robust Web Application Firewall (WAF) for enhanced web security.
- Seamless integration with popular AI frameworks and APIs.
Cons:
- Limited edge computing capabilities and scalability for AI usage.
- Needs improvement in developer-friendly features for easier adoption of AI capabilities.
- Challenges with adopting complex privacy rules on the platform.
Pricing:
It starts at $7 per user per month. Plus, you can also ask for a custom quote.
I am very disappointed with the service. I have been trying for two weeks now to upgrade my plan and have revived no help from their billing department. I have 3 tickets in with no responses!
6. Perimeter 81
Perimeter 81 replaces outdated security measures such as VPNs and firewalls, simplifying and securing remote access to company networks and resources through its Remote Access VPN.
The platform enables multi-tenant management and global gateway deployment, ensuring dispersed workforces securely access corporate resources, whether hosted on-premises or in the cloud.
Key Features:
- Software-Defined Perimeter: Leveraging a software-defined perimeter, Perimeter 81 provides organizations granular control over resource access.
- Zero Trust for Remote Workers: Specializing in securing remote access, Perimeter 81 is ideal for organizations with distributed workforces.
- Intuitive Management Interface: Perimeter 81 offers an intuitive management interface for efficient configuration and monitoring of Zero Trust security policies.
Pros:
- Easy and seamless VPN location switching.
- Simple one-button VPN selection on Mac, perfect for uninterrupted meetings.
Cons:
- Occasional failure to connect automatically to VPN, requiring manual reconnection.
- Intermittent VPN connectivity issues affecting performance, necessitating occasional disabling during virtual meetings.
- Long connection times to the system can be frustrating.
Pricing:
It starts at $8 per user per month.
We use Perimeter 81 and would/do recommend it. Super low touch and reliable (hope I didn’t jinx it). Also, they were pretty reasonable with their minimums and have been quite responsive.
7. Palo Alto Zero Trust Enterprise
Palo Alto Networks’ Zero Trust Enterprise emphasizes security. Security teams aim to implement zero trust principles, follow security practice recommendations, and optimize procurement across the business.
ZTNA technology enables secure remote access to applications and services, applying predefined access control criteria.
Prisma Access by Palo Alto Networks ZTNA 2.0 continuously inspects security and verifies trust, protecting all data and allowing access only to authorized individuals.
Key Features:
- Next-Gen Firewall Capabilities: Palo Alto Networks integrates advanced firewall technology into its Zero Trust solutions, leveraging its leadership in next-generation firewall capabilities.
- Cloud Security Focus: It prioritizes cloud security, offering organizations a secure framework to access and manage cloud resources.
- Threat Intelligence: It enhances the security efficacy of its Zero Trust solutions by leveraging comprehensive threat intelligence to stay ahead of emerging threats.
Pros:
- Enables businesses to implement access control rules tailored to specific locations or devices.
Cons:
- Preventing vulnerable or unpatched devices from accessing corporate services.
- Improvement needed in the initial setup and operational processes.
Pricing:
It offers customized pricing.
Moving to Prisma was pretty flawless until our file share/excel power users. We did make some internal geographic I.T. moves which could have added to the problem. I personally think Prisma is much more complicated to set up and they don’t have a true IDP integration.
8. Okta Identity-Driven Security
Okta uses a sign-on system to securely connect the right people with the right technology for both remote and on-premises teams, enabling a “Zero Trust” approach.
By providing a framework for secure identification and context-aware access, Okta helps businesses overcome challenges and speed up their zero-trust security strategy.
Okta integrates with leading security providers and your entire IT ecosystem for a unified Zero Trust approach. Okta also offers a free Zero Trust Assessment tool to evaluate your maturity level and guide your next steps.
Key Features:
- Identity Lifecycle Management: Okta’s Zero Trust solutions include robust features for secure and efficient onboarding and offboarding of users.
- Single Sign-On (SSO) Integration: Okta specializes in seamlessly integrating SSO capabilities into its Zero Trust Network Access offerings for a streamlined user experience.
- Adaptive Authentication: Okta dynamically adjusts authentication requirements based on user behavior and risk factors, enhancing security.
Pros:
- Users can access applications through a single sign-on (SSO) interface.
- Offers detailed security reporting.
- Provides options for passwordless sign-on.
Cons:
- A la carte functionality can result in escalating costs.
- Primarily focused on web login management, making it less ideal for complex developer environments.
- Does not offer an on-premises option.
Pricing:
Its pricing starts at $2 per user per month.
It was bad enough that we didn’t go through with the purchase after demoing it.
9. JumpCloud Open Directory Platform
JumpCloud aims to be the all-in-one solution for zero trust identity and access management.
Built on open standards, its cloud-based Open Directory Platform enables seamless management of cross-OS servers, devices, and user identities, including single sign-on (SSO), conditional access, and passwordless access, all from a single pane of glass.
Key Features:
- Unified Management: Manage all server, device, and user identities across different operating systems from a single interface.
- Single Sign-On (SSO): Simplifies user access with one set of credentials for multiple applications and resources.
- Conditional and Passwordless Access: Enhance security and user experience with adaptive authentication and passwordless options.
- Integration Options: Connect and expand your toolset with integrations for popular services like AWS Identity Center, Google Workspace, Microsoft 365, Active Directory, HRIS platforms, and network infrastructure resources.
Pros:
- Comprehensive platform supporting numerous integrations.
- Flexible access control enforcement.
Cons:
- Extra charges for certain options.
- Limited support for legacy or on-premises systems.
- Steep learning curve.
Pricing:
Pricing starts at $9 per user per month, but the various pricing options and features can be confusing when compared.
We use JumpCloud at my work, I would stay away honestly. They have features that are half-baked and continue to develop new ones rather than stabilize their existing feature set. As well, it leads to more configuration issues if you’re self-hosting a SIEM, as they manage EVERYTHING through Powershell CONSTANTLY.
10. BeyondTrust
BeyondTrust, formerly known as Bomgar, offers a range of zero trust solutions for identity and access management and endpoint security.
While it covers various aspects of zero trust, the piecemeal approach can increase overall costs and complicate implementation.
Key Features:
- Endpoint Privilege Management: Allows users to approve and revoke access to critical systems, providing a detailed audit trail.
- Password Safe: Manages access to and usage of privileged credentials and SSH keys, enhancing security.
- DevOps Secret Safe: Centralizes secrets management using REST APIs and CLI tools to streamline DevOps workflows and integrate APIs seamlessly.
- Privileged Remote Access: Secures access to workstations, including internal and external cloud infrastructure, eliminating the need for a VPN.
- Remote Support: Enables IT to remotely monitor, access, and control customer devices, both on and off the corporate network.
Pros:
- Manages permissions using AD, LDAPS, RADIUS, and Kerberos.
- Extends Microsoft AD authentication, SSO, and Group Policy Configuration Management.
Cons:
- Requires purchasing additional add-ons.
- Complex initial setup.
- High licensing costs.
Pricing:
It offers customized pricing.
I didn’t go beyond a demo with BeyondTrust because they’re entirely group policy based just like PolicyPak. This simply doesn’t allow you to be agile, and doesn’t allow you to be flexible. They’re also the oldest offerings in the PAM industry… Which makes them way too expensive for their feature set and capabilities.
What Is Zero Trust?
Zero trust is a security strategy where no user, app, service, or device is trusted by default.
It follows the principle of least-privileged access, requiring trust to be established based on the entity’s context and security posture before any connection is allowed. This trust is continuously reassessed for every new connection, even if the entity was previously authenticated.
Zero Trust is designed to secure modern digital infrastructures and data, addressing challenges like remote work, hybrid cloud environments, and ransomware. While various vendors have their own definitions of Zero Trust, there are recognized standards that can help align it with your organization’s needs.
The Importance of Zero Trust Solutions
According to the 2024 data breach investigations report, 15% of breaches involved a third party or supplier, such as software supply chains, hosting partner infrastructures, or data custodians.
This highlights the critical need for implementing Zero Trust solutions to protect against vulnerabilities arising from third-party and supplier breaches.
Here are the key reasons to implement Zero Trust solutions:
1. Protection Against Advanced Threats
By strictly controlling access and continuously monitoring for suspicious activity, Zero Trust reduces the potential points of attack and helps safeguard against vulnerabilities introduced through suppliers and partners, mitigating the risks associated with third-party breaches.
2. Improved Access Control
Zero Trust grants users and devices the minimum level of access necessary, reducing the risk of unauthorized access to sensitive information, and dynamically adjusts access requirements based on the user’s context and behavior, enhancing security without sacrificing user experience.
3. Support for Modern Work Environments
Zero Trust ensures that remote workers can securely access company resources from anywhere, maintaining robust security controls outside the traditional office perimeter, and provides consistent security across local, cloud, and hybrid environments, addressing the complexities of modern IT infrastructures.
4. Compliance and Governance
Zero Trust helps organizations meet stringent regulatory requirements for data protection by enforcing strong security policies, and comprehensive logging and monitoring facilitate easier compliance audits while providing detailed insights into access patterns and potential security incidents.
How to Choose the Best Zero Trust Solutions?
There’s no one-size-fits-all solution when it comes to choosing a Zero Trust or any other cybersecurity solution. However, there are a few points that you should take care of while comparing different options:
1. Understand Your Security Requirements
Assess your current security posture, identify gaps, and determine specific areas where Zero Trust can add value, such as user authentication, device security, network segmentation, or data protection.
2. Compare Integration Capabilities
Ensure the solution integrates seamlessly with your existing IT infrastructure, including cloud services, on-premises systems, and third-party applications, and supports industry-standard protocols and APIs to facilitate integration.
3. Consider Scalability and Flexibility
Choose a solution that can scale with your organization’s growth and adapt to changing security needs, and opt for platforms that offer modular features, allowing you to implement Zero Trust incrementally.
4. Check for Comprehensive Coverage
Verify that the solution covers all critical aspects of Zero Trust, including identity and access management, device security, network security, and data security, and ensures continuous monitoring and real-time threat detection.
5. Assess User Experience and Usability
Evaluate the user interface and ease of use for both administrators and end-users, and look for solutions that offer a balance between strong security measures and minimal user disruption.
6. Review Vendor Reputation and Support
Research vendor reliability, customer reviews, and industry reputation, and ensure the provider offers robust customer support, including training, documentation, and technical assistance.
7. Analyze Cost and ROI
Compare the pricing models of different solutions, considering both initial costs and long-term value, and assess the return on investment by considering the potential reduction in security incidents and operational efficiencies gained.
8. Look for Compliance Features
Ensure the solution helps you meet regulatory requirements relevant to your industry, and check for features that facilitate compliance reporting and auditing.
Why Heimdal?
Heimdal stands out as the best Zero Trust solution due to its comprehensive Privilege Elevation and Delegation Management (PEDM) capabilities.
By granting users and applications only the essential permissions they need, Heimdal significantly reduces the risk of unauthorized access and minimizes potential attack surfaces.
Its just-in-time access controls and unified platform for managing user privileges ensure robust security and compliance to its users.
Frequently Asked Questions (FAQs)
Which is one of the most popular international standards referred to as Zero Trust?
The US National Institute of Standards and Technology (NIST) describes Zero Trust in its 2020 standards as an “evolving set of cybersecurity paradigms that shift defenses from static, network-based perimeters to a focus on users, assets, and resources.”
Which three 3 of practices are core principles of Zero Trust?
The three core principles of Zero Trust are Least Privilege Access, Always Verify, and Risk Mitigation.
What are the first steps in Zero Trust?
The initial stage of implementing Zero Trust involves identifying and evaluating all network users, their roles, associated devices, and the applications and services essential for their operations.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









