Contents:
Kevin Mitnick, once dubbed the World’s Most Famous Hacker said that “hackers are breaking the systems for profit. Before, it was about intellectual curiosity and pursuit of knowledge and thrill, and now hacking is big business.” As defenders, it’s our job to put them out of business or, at the very least, provide some good sport.
In this article, I want to explore how common tools such as those from the Google Workspace suit can lead to a full-fledged business compromise.
For this purpose, I’m going to leverage a less-known X-Frame Options header vulnerability associated with the Google Docs’ ‘Send Feedback’ feature.
What you’ll learn in this article
- Another attack surface to cover and address.
- The importance of using secure tools even for day-to-day tasks.
- Alternative ways to bypass the security controls of commonly used applications.
- How to draft a security policy to deal with this attack vector.
Google Workspace Contributing to Data Breaches and Shadow IT
At its core, Google Workspace is a suite that should enhance productivity and make collaboration easier, regardless of workflow. However, if used incorrectly, it can become a liability. To this end, before going into any specifics, I invite you to ponder on the following aspects.
- The most effective business compromise methods aren’t the most obvious.
- Open-source and freeware tools should not be deployed nor used in sensitive areas.
- Google Docs and similar apps can and will be weaponized if used without restrictions and governance.
- Cost vs. benefit vs. risk of using potentially unsafe applications, thus feeding unauthorized ops such as Shadow IT.
Covering all bases being vital to business continuity (and integrity), I’m going to show you a way how an innocuous thing like a G-doc could run your business into the ground.
Brief(est) History of Google Workspace Vulnerabilities
If your team is using Google Workspace tools to log sensitive information, your next move should be to do some research on the topic. Let me save you the trouble of searching for this info. Here are a couple of incidents you should consider.
DeleFriend vs. Google Workspace
The DeleFriend exploit of Google Workspace exposed a major security vulnerability, allowing unauthorized access to sensitive data. This breach was significant due to the extensive use of Google Workspace in professional and educational environments.
The incident highlighted the risks associated with third-party integrations in major platforms. In response, DeleFriend and Google rapidly worked to rectify the security flaw, emphasizing the need for stringent security measures in digital ecosystems.
Lateral Movement with Google SSO
The lateral movement vulnerability in Google Workspace, leveraging Google’s Single Sign-On (SSO), posed a critical security threat.
It enabled attackers with initial access to one Google account to traverse multiple services and applications. This exploit risked exposing sensitive personal and organizational data.
Free Cloud Identity Data
The Google Workspace exploit utilized a flaw in the Free Cloud Identity’s token validation process, allowing attackers to bypass SSO authentication.
This technical oversight permitted unauthorized API access, potentially exposing sensitive data across multiple Workspace applications.
Google’s remediation involved patching the token validation mechanism and reinforcing API access controls to prevent such sophisticated exploits in the future.
G-Suite Super Admin
The G-Suite Super Admin exploit involved a sophisticated manipulation of permission escalation within the admin console. Attackers exploited a vulnerability in the role assignment process, gaining unauthorized Super Admin privileges.
This breach allowed wide-ranging access to all G-Suite applications and user data, prompting Google to implement stringent controls and audit mechanisms to secure the admin console against such vulnerabilities.
GhostToken
The GhostToken exploit in Google Workspace involved a complex vulnerability in the OAuth 2.0 token handling mechanism.
Attackers manipulated token validation processes to gain unauthorized access to user accounts and data across various Workspace applications. Google’s response involved a comprehensive overhaul of the OAuth system, enhancing token security and auditing procedures to prevent such advanced token-based exploits.
Google Workspace Compromise – Proof-of-Concept
Now that I’ve added a bit of context to this experiment, let me go through the setup and, of course, the purpose of this exercise.
The goal is twofold:
- Gain access to a G-doc document and obtain sensitive product development data (e.g., new features, unsolved bugs, bulk-imported code from GitHub or similar repositories, flawed code, ways to bypass controls etc.)
- Infiltrating further into the network (i.e., lateral movement).
Now for the setup; for this job, I’ve used two Windows-running machines (i.e., attack and victim machine), both with the latest builds.
The first task is to collect as much intel as possible. This is a vital step because the info will allow you to identify weak links, improperly secured areas, misconfigurations, missing protocols or even a backdoor that can facilitate the entire process.
One way to go about it would be to leverage clear web resources (e.g., social media to identify key players, G-Business for company info and/or industry).
You can also try other techniques such as:
- Sending bogus surveys to phish or spear phish the victim;
- Networking scanning;
- Stealing user credentials from third-party websites (i.e., LinkedIn);
- Brute-forcing;
- Searching dark web credentials repositories;
- Drive-by downloads;
- Keylogging.
Let’s assume that the threat actor has all the intel he needs to attempt infiltration. For this exercise, I will focus on a less-known vulnerability inherent to Google Docs called an X-Frame-Options header deficit – which is another fancy way of saying that the HTTP reply header a browser should be receiving doesn’t instruct the browser if it should be accepting or not to render a page in the form of an <object>, <embed>, <iframe> or a plain <frame>.
By default, the X-Frame, can accept two types of directives – DENY or SAMEORIGIN. Syntax is important in this case because, if you want to enact a cross-origin attack, the X-Frame directive should always be SAMEORIGIN and not DENY (i.e., if set to DENY, the webpage will not be rendered in a frame).
The next step is to tap into Google Doc which is no easy feat; Google’s word processor may be free to use, but not unsecured.
As the direct approach of interacting, on any level, with the backend code doesn’t work, the alternative is to set up a rogue domain and trick the application to redirect requests to our freshly-hatched C2.
The setup is now complete. Now to the next phase.
For the attack to have effect, we use Google Docs’ ‘Send feedback’ feature. The feedback section is very useful in submitting error reports, but it also has a hidden flaw that can be used to stage an attack.
The ‘send feedback’ window allows you to send various attachments including pictures or screenshots. Whenever the user submits feedback, it’s automatically transmitted to Google’s main website.
In the case of feedbacks that contain screenshots, the form also sends the RGB values of the picture.
Here’s a quick demo of how this works.
Using Python, I’ve written two sets of code. You can find them below. – The first one reads the pixels of my choice picture and outputs its RGB values, while the second ingests RGB values and converts them into an image.

A very simple example of what happens on the backend side of things during the transmission – conversion of RGB values.

Back to our case; the packed feedback (i.e., RGB values corresponding to the snapshot enclosed in the feedback form) gets sent to www.google.com and then redirected to a subdomain called feedback.googleusercontent.com.
The subdomain ingests the data-URI of the enclosed snapshot and, at the same time, sends back the data-URI to the corresponding parent iframe.
Now to intercept the HTTP request carrying the RGB values of a screenshot. Deploy a tool like mitmproxy, HTTP toolkit, or Burp Proxy to snatch the request. You can even use over-the-counter APIs or write-your-own.
Once you capture the request, you can then redirect it to a C2 server and, boom! You can now see the contents of the Google Docs document.
Remember that this feat can be achieved only if the X-Frame header is set on SAMEORIGIN.
A simple and effective method to eavesdrop on your adversary.
From here, you’re free to perform additional actions. For instance, at this point, you could use the intel and the tools to change the default save folder in Google Drive or turn yourself into a collaborator and view changes to G-Docs in real time.
I would advise you not to underestimate the value of jailbreaking Google Drive and Google Workspace integration
Don’t forget that over 1 million businesses use Google Workspace which means that a successful attack can grant a threat actor access to virtually every application from the suite and, as we know, not all sensitive, private, and sensitive documents, are being processed by a dedicated and secure application.
How to Protect Yourself Against Google Workspace Exploits
Here are a couple of things you can try out.
- Invest in dedicated dev-documentation tools to prevent security breaches.
- Ensure that your team is using the tool and not keeping scrap notes on other tools.
- Periodic vulnerability scanning to ensure that your network is clean.
- Always remember that the most inconspicuous attack vectors have the gravest impact.
- Deploy a Managed Extended Detection and Response (MXDR) solution to cover all attack vectors.
Why Use Heimdal® MXDR?
Heimdal®’s MXDR service is powered by the renowned Heimdal® XDR – Unified Security Platform that brings together 10+ cybersecurity solutions that cover complex attack surfaces.
MXDR Adapt is especially valuable for organizations with a large and complex IT infrastructure, such as multinational corporations, financial institutions, healthcare providers, government agencies, and other organizations that handle sensitive data.
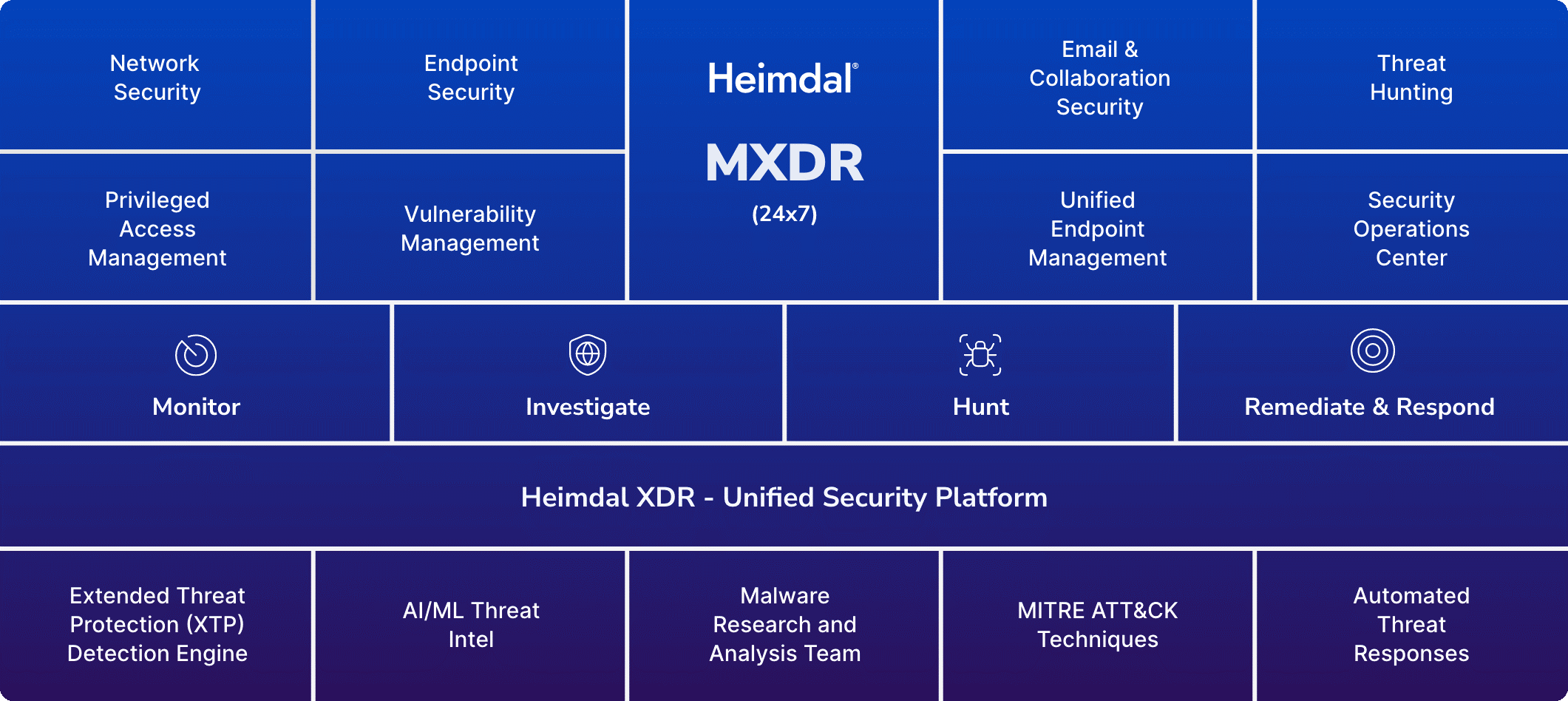
Heimdal® is also an excellent choice for SMBs because they often lack the budget to maintain an in-house cybersecurity team or invest in multiple security tools. However, with MXDR Adapt, they can gain access to a variety of advanced security features at an affordable cost.

- End-to-end consolidated cybersecurity;
- Powered by the Heimdal XDR, Unified Security Platform
- Comprehensive enterprise security without any additional integrations
- 24x7 monitoring & prompt response delivered by our security experts
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









