Contents:
Apple ID phishing scams represent genuine danger nowadays. The concept of “phishing” stands for an advanced cyberattack form that embodies social engineering tactics. It may sound familiar to you. Disguised links sharing embedded in emails is one of the tactics that may trick you into providing sensitive data to cybercriminals.
In this article, we are going to take a closer look at phishing attempts involving Apple IDs. Today there are 1.5 billion active Apple devices, which require Apple IDs to gain access to Apple services like Apple Music, App Store, iCloud, FaceTime, iMessage, and others. Why is the threat so real? Think about the fact that you don’t even require an Apple device to access Apple-related software or services, such as iTunes, or log in to Apple’s official website so the number of people becoming victims is exponential.
Why Are Scammers Trying to Steal Your Apple ID?
The reason is obvious – your Apple ID is your ticket to using anything Apple-related and stores a great deal of personal information.
- You use your Apple ID to log in to your Apple devices – think Mac, iPhone, iPad, iPod, Apple TV, and in the future you might even be using it for your Apple self-driving car, the iCar developed through project Titan, according to rumors. However, there is no specific data confirmed when the self-driving car project will be finalized.
- It includes your payment and shipping information for purchasing applications from the App Store and devices by logging in to Apple.com.
- With the Apple ID, you can access your security settings, subscriptions, and in-app purchases associated with it.
- Your Apple ID is used to access iCloud, where you can store your photos and any types of files and the theft of these can lead to blackmailing and even sextortion.
There are many forms of Apple ID phishing attempts out there. In this article, we’re going to give you some examples so you get a sense of what they can look like and be better prepared against them.
Types of Apple ID Phishing Scams with Examples
1. Apple ID Receipt Order Email
You can make purchases in App Store, iTunes Store, iBooks Store, or Apple Music.
In the subject line of this kind of e-mail, you will find included some phrases like “Receipt ID”, “Receipt Order”, or “Payment Statement”. The purpose of this scam is to trick you into thinking a payment has been made using your credit card. As a result, you may hurry into canceling the order, worried that your money has been taken. If the attached file is opened or if you click the link, most probably you will end up on a page where you will be asked to confirm your personal details, such as password, credit card details, address, etc.
However, there are other Apple ID fake receipts that may seem much more convincing, like this one: Error! Filename not specified.
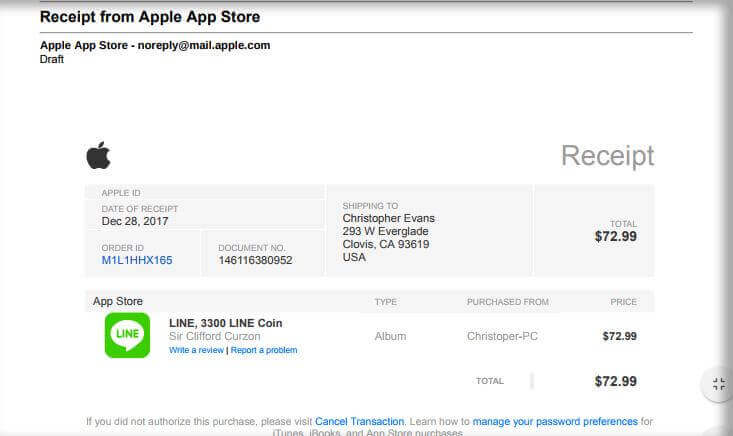
As a general rule, what makes it obvious that you can receive a fake invoice is the fact that an authentic receipt e-mail from Apple will know to precisely tell where your current billing address is. You will never find in Apple’s invoices some shady links to click on in order to make some changes to a subscription or to cancel it.
Also, pay attention to the fact that firstly, Apple purchases will never require information via e-mail and will not ask for Social Security Number, the credit card CVV, or payment info.
So, stay alert, and look for the warning signs! Moving forward, we’re going to give you a few more examples of Apple ID phishing scams so you know what type of content you should watch out for.
2. Apple ID Phone Call Scams
Apple ID scams have also gone beyond fishy emails and crossed over to the illegal business of scam phone calls. Scammers have also tried to use spoofed phone numbers, which are displayed on your phone as a real Apple number, with Apple’s logo, official website, customer support number, and actual address. This way, the masquerade looks alarmingly real.
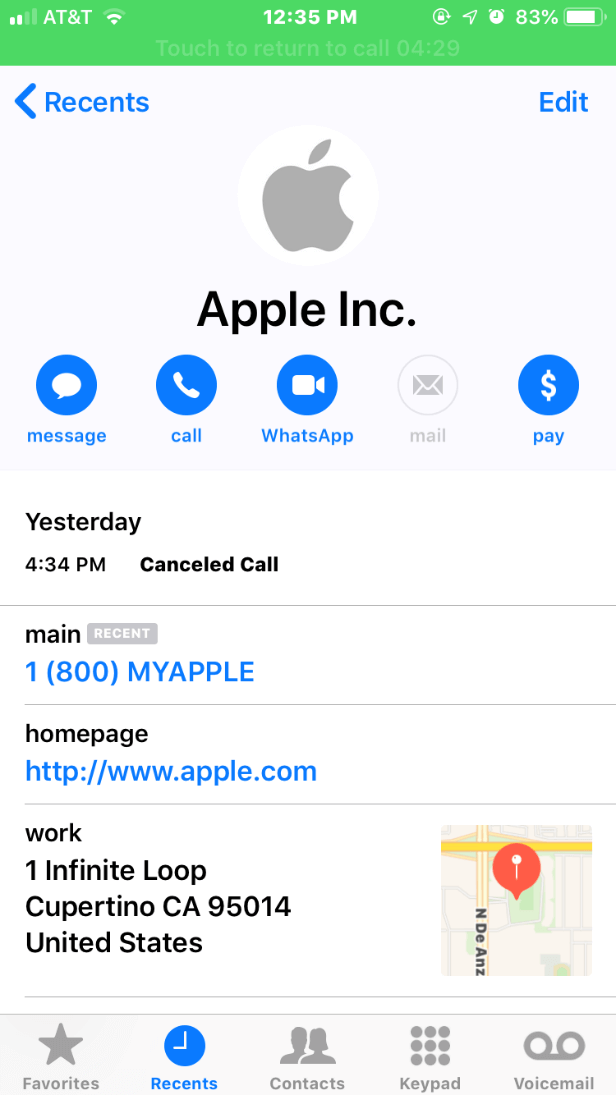
Sometimes it’s hard to tell if the one who calls you is really an Apple representative. The scam can seem so veridical. You wouldn’t think hackers try to perform an Apple ID phishing scam. The solution is to just simply hang up. Then call the real Apple to check if they genuinely called you before. Also, it is known that Apple representatives will never ask for Apple ID passwords, iCloud credentials, and other data in a phone call.
3. Apple ID Fake Text Message
Here is the second example of an Apple ID scam you may receive on your phone, this time in the form of a text message. It would read something like “Your Apple account is now locked” and will lure you into accessing a link that supposedly unlocks your account.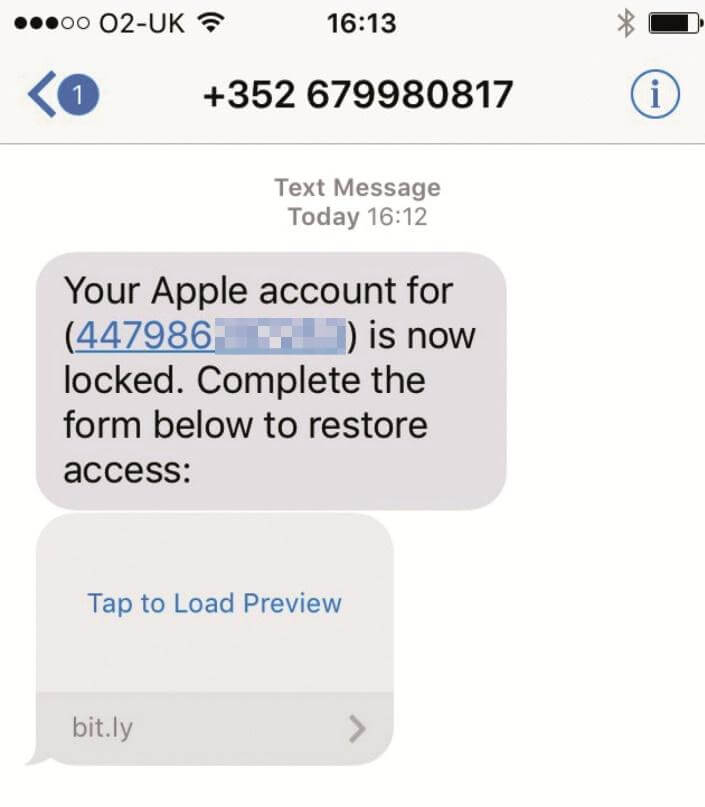
Here is another similar example, which aims to trick you into thinking your iCloud ID has been deactivated and that you now need to complete the activation process.
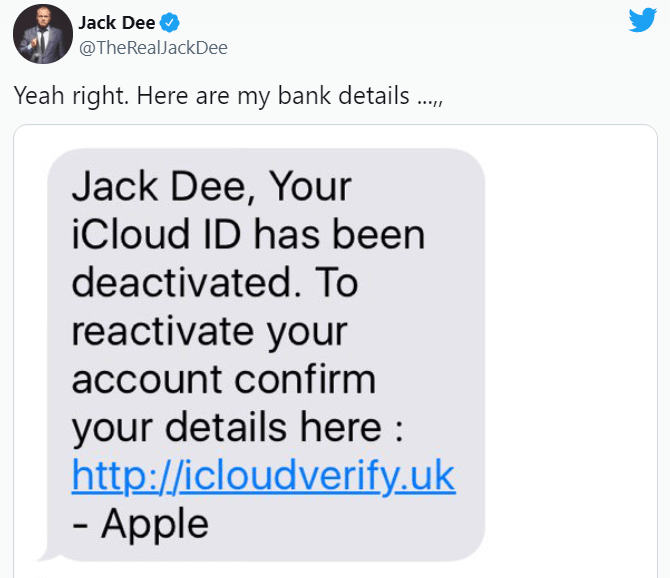
Another example of a fake text message would be to announce through an SMS that your iCloud account shows signs of malicious activity. They will text you and provide a phone number where you have to call to solve your issue. If you call, you’ll be welcomed by that typical automatic message that says to wait a certain amount of time till an agent will talk to you. Then, when you get in touch with the supposed agent finally, they will ask for credentials, payment info, or access to remotely assist you. This way hackers phish scam your Apple ID.
4. Temporarily Disabled Apple ID Email
Similar to the “Your Apple ID Has been locked” text message we mentioned; you may also receive the email version of this phishing scam. 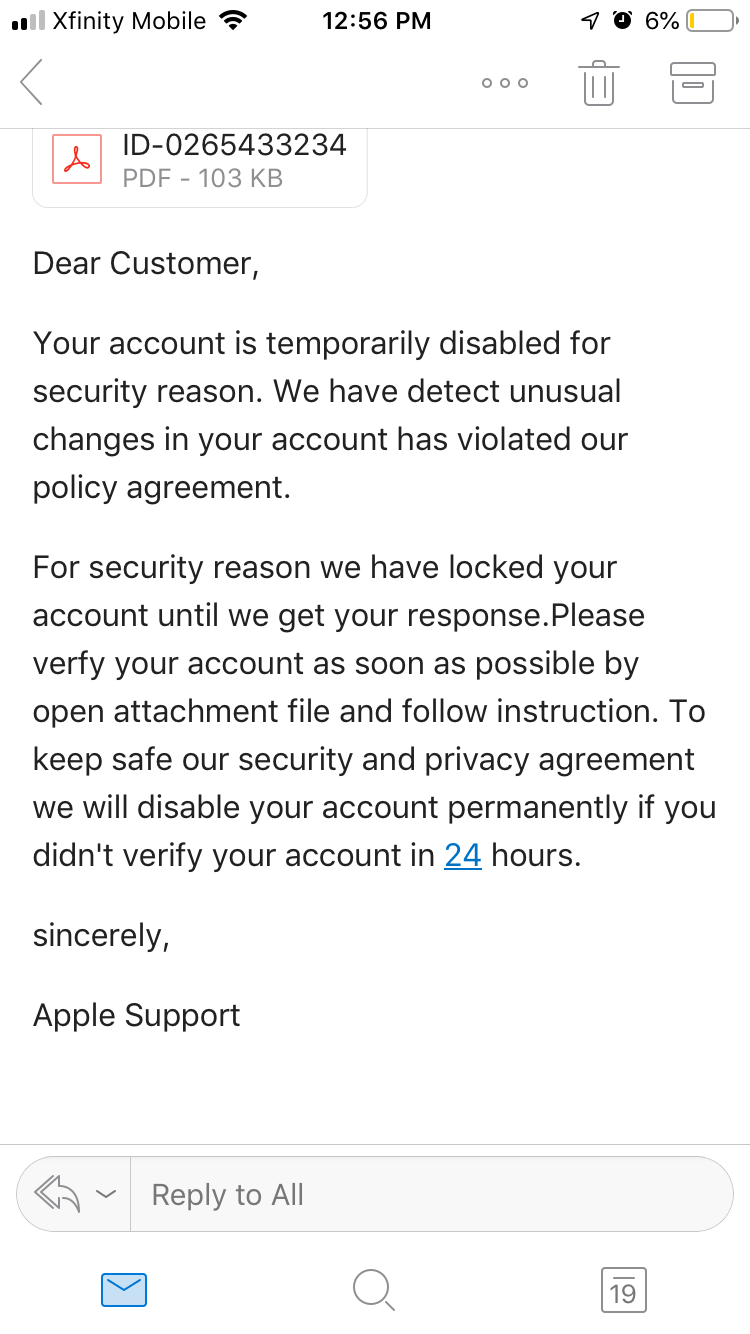
The scammers will try to trick you into clicking the link to verify your account, which will lead to malicious websites trying to steal your data. According to the source, the link sends you to a webpage almost identical to Apple’s official site, but there are some misspelled words and you are not able to click on any of the icons on the top. The person who raised a flag on Apple’s Discussion page correctly identified this as a phishing attempt, noticing all the signs.
5. App Store Pop-up Trying to Steal Your Password
We are going to show you examples of Apple ID phishing scams through a simulation – the good news is that it hasn’t been spotted in real life as far as we’re aware. Yet, it proves how easy it would be for a fraudster to create a fake pop-up that looks identical to the one in the App Store.
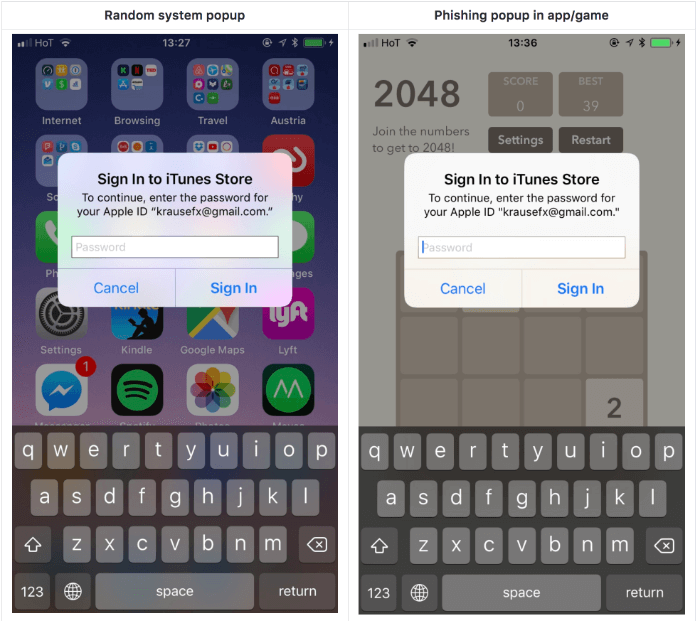
Since users got used to entering their passwords every time they are asked to when interacting with an Apple app, they would do this by default whenever needed, without questioning if the pop-up is genuine or not. Who would suspect something like this, anyway? Especially when the screen looks identical to Apple’s. So, you may be asking how you can protect yourself from spoofing emails. Felix Krause, the author of this proof of concept phishing attempt, advises us to press the home button to see if the app closes. If it does, this was clearly a phishing attack. If it doesn’t, this is a real system dialog and the explanation is that the system dialog runs on a different process and not as part of an app.
6. Fake Calendar Invitation
You might receive an invitation in Calendar or Mail that can make you raise eyebrows. Do not accept it! Report it as Junk immediately. Another situation mentioned on the Apple website would be that maybe you mistakenly subscribed to a SPAM Calendar. The good news here is that you can delete it.
7. Your iPhone Gets Locked
Well, if you’ve come to this, you might already have fallen victim to the Apple ID phishing scams. So, we are in the scenario where hackers already have your Apple ID. This means that they can access your iCloud account that gives them control over everything. What they can do is to set your phone as lost and activate the “Find My iPhone” capability. Now, this is a good example of a ransomware attack, because they will keep your phone locked until you pay them to recover your data.
How to Spot an Apple ID Phishing Scam
We know that some phishing scams may be much more difficult to identify than others, but the signs will (almost) always be there. Below we’ve included a few warning signs that will help you spot phishing and be a step ahead:
The well-known spelling and grammar mistakes
Apple is a reputable company. It will never send e-mails that have typos and grammar mistakes within. Look at the fourth example we gave in this article: “We have detect” instead of “We have detected”, “Please verfy” instead of “Please verify”. In addition, Apple will always use American English and if the writing style is awkward is clearly not from Apple. You can look for an old real e-mail from them and just compare the writing style. Sounds similar?
Unprofessional e-mail or website design
First of all, Apple does not require the Apple ID via message or e-mails. If you click on a phishing link it might get you to some dubious website pages. Sometimes the design it’s obviously unprofessional, sometimes it gets an accurate resemblance to the genuine Apple website that might fool you.
Check also the e-mail sender, it should be appleid@id.apple.com, not another one. If you hover over the fake one with your mouse, you might observe that it can be just a series of numbers with no logic so it’s obviously part of an Apple ID phishing scams’ series. If the sender’s e-mail does not match the company he supposedly represents, it’s a scam. In addition, the CC list might contain numerous suspicious e-mail addresses.
Being asked to verify personal details via email or phone/text
As I already mentioned above, it’s a known fact the Apple’s representatives will never ask for such details through e-mails or text messages.
Dubious links or shortened URLs
If you land on that fake website though, check the URL. If it contains suspicious characters besides myapple id, it surely does not belong to the real Apple page. You can hover over the URL also before opening it. This way you can preview the destination URL.
What’s more, Apple will never use shortening services to make their URLs smaller. Be vigilant!
Shady email attachments
You can spot a dubious e-mail attachment by looking at file extensions that are troubling like EXE, JAR, MSI, or CMD. If these include files that are encrypted so that you might need a password to see what’s inside or the file name is something strange or does not sound very natural or trustworthy you might deal with a scam.
Urgent action
The way the message or e-mail is written makes you feel like you have to do it. You have to click that link now, otherwise, your account will be deleted or any other consequences will take place. The feeling of urgency is a good psychological tactic. It puts pressure on you.
General greeting
A trustworthy company will not send you an e-mail starting with “Dear” or “Dear customer”. You are in their database, so they know your name, hence they will address you by your name and make it more personal: “Dear John”, “Dear Mr. Smith”, etc.
The user’s e-mail address is not correct
If your e-mail address or phone number are mentioned in the message, just check if they are the correct ones or the one with which you registered.
Check your purchase history
A good method to detect if a receipt is genuine is to simply go to the purchase history by logging into your Apple account. If you don’t find it there, well, you know the answer: it’s a scam. And of course, Apple invoices do not contain hyperlinks.
How to Protect Against Apple ID Scams
Here are some actionable tips for you to keep in mind, which can apply both to your Apple ID and online security in general.
- Stay informed. Here are some resources you can subscribe to Cyber Security for Beginners and the Daily Security Tip.
- Use browsers with built-in protection against phishing, such as Chrome. Also, consider using extensions that will increase your online safety.
- Hover your mouse over links before clicking on them. If the URL looks suspicious, just DO NOT click on it.
- Don’t open attachments from unknown senders.
- Always keep your software up to date. Updates are very important as companies provide regular patches that might help you prevent and not treat the consequences of a cyberattack.
- Protect every account that you can (including your Apple ID) with two-factor authentication.
- Use proactive anti-malware protection, which filters and blocks malicious links.
- Pay attention to suspicious phone calls. If they ask for private information, check twice before providing it.
- A secured website starts with HTTPS. Verify the URL to make sure it is HTTPS.
- Password protection: you should use strong, complex, unique passwords to log in to your applications and change them often. And do not store them in plain sight.
- Use a password manager.
- If you suspect something’s wrong with your account, go and log in manually. Whatever genuine message will be displayed there too. You can use Settings > [your name] > iTunes & App Store on iOS or Account > View My Account in iTunes to make changes if necessary as Apple recommends to avoid Apple ID phishing scams or through http://appleid.apple.com/
- You can spot unknown senders on your iPhone by simply activating the Filter Unknown Messages capability: Settings -> Messages -> Filter Unknown Senders. If the sender is not in your contact list and you’ve never spoken to him, the system will detect it.
- Filter your Apple’s messages: Flag an e-mail as SPAM.
- Data backup: this should stand for a general rule and be natural for you to store your private information on another system not connected to your network.
- A common-sense measure would be to never tell anyone your Apple ID password or any related sensitive info in order to avoid Apple ID phishing scams. If you suspect something, modify your password.
Out of all, the best solution to protect against Apple ID phishing scams might be a threat prevention one to spot attacks before they can reach you. If you want to find more, check it out:

Reporting Phishing Scams to Apple
Where can you report your issue?
Any e-mail that seems suspicious should be redirected to reportphishing@apple.com
If the malicious behavior is related to some iMessage or Calendar invitation go to the Report Junk option.
You can immediately announce the local police or the Federal Trade Commission if someone tries to trick you with a fake phone call.
An e-mail that came into me.com, mac.com, or iCloud.com should be forwarded to abuse@icloud.com
Other official Apple resources that can help
Below we’ve also listed some official resources from Apple that you should go through if you’re using an Apple ID. It doesn’t matter if your account has been compromised or not, you should always stay on top of your online security.
- What to do if you think your Apple ID has been compromised.
- Information around phishing and other suspicious emails.
- How to avoid Apple ID scams in general.
- How to identify legitimate emails from Apple.
- Details on your Apple ID security.
- Also, watch this video for a summary on how to identify, avoid, and report phishing:
And don’t forget to check out our in-depth anti-phishing guide!
Have you ever been targeted by scammers who tried to harvest your Apple ID information? Let us know what happened in the comments section below.
This article was initially written by Bianca Soare in 2019 and rewritten by Andra Andrioaie in 2021.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








