Contents:
Apple has recently released security updates for several of its products, including a patch for its macOS desktop operating system. The patch includes a zero-day vulnerability fix that has been abused in the wild by the XCSSET malware gang for almost a year.
Tracked as CVE-2021-30713, the exploited macOS flaw was found in Apple’s Transparency, Consent and Control (TCC) framework, which manages user consent for permissions across local apps. The tech giant refused to share the exploit mechanism or the effects of successful exploitation. The company fixed the bug with improved validation.
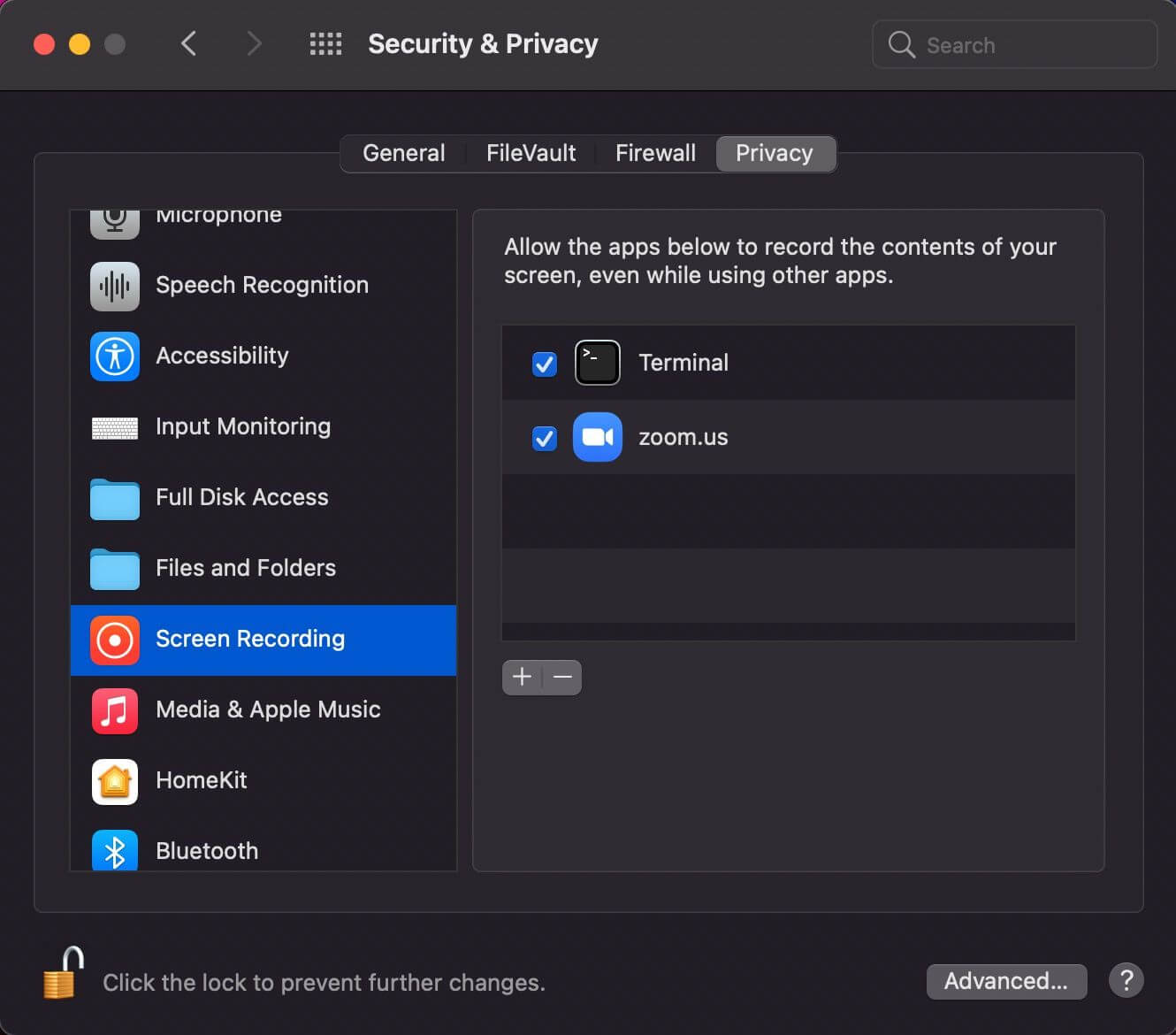
Image Source: Jamf
In one of their articles, security firm Jamf noted that the vulnerability has been exploited by the XCSSET malware operators.
We, the members of the Jamf Protect detection team, discovered this bypass being actively exploited during additional analysis of the XCSSET malware, after noting a significant uptick of detected variants observed in the wild. The detection team noted that once installed on the victim’s system, XCSSET was using this bypass specifically for the purpose of taking screenshots of the user’s desktop without requiring additional permissions.
XCSSET was first discovered in August 2020 by Trend Micro’s Mac Threat Response and Mobile Research teams. The researchers revealed that the vulnerability can be exploited to provide malicious apps with permissions including full disk access and access to screen recording. This means that threat actors can take screenshots of infected machines.
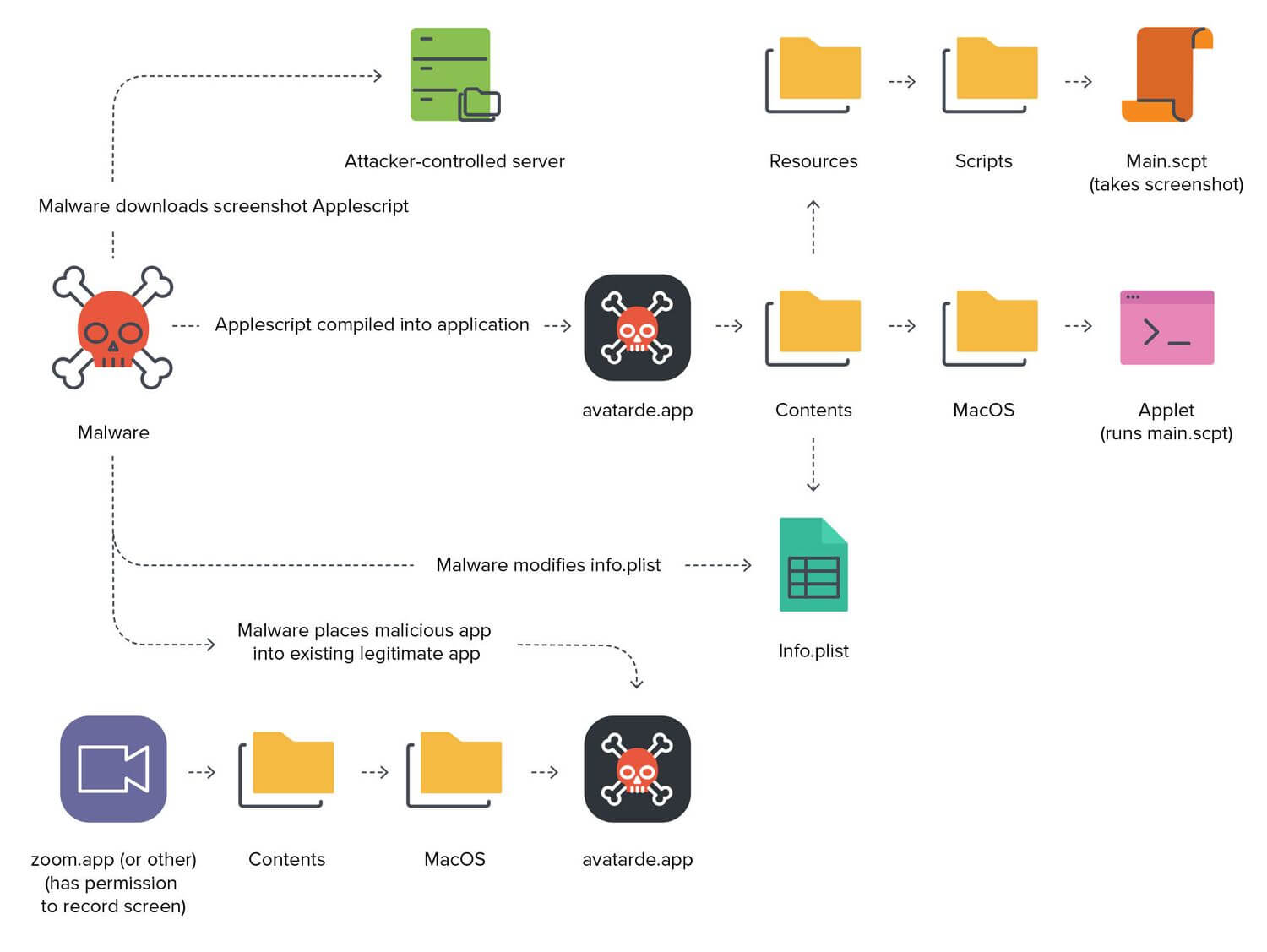
Image Source: Jamf
This threat primarily spreads via Xcode projects and maliciously modified applications created from the malware. It is not yet clear how the threat initially enters these systems. Presumably, these systems would be primarily used by developers. These Xcode projects have been modified such that upon building, these projects would run a malicious code. This eventually leads to the main XCSSET malware being dropped and run on the affected system. Infected users are also vulnerable to having their credentials, accounts, and other vital data stolen.
Trend Micro analysts discovered a new XCSSET version just last month, which was updated to work on the newly-released Apple-designed ARM Macs.
The news of the CVE-2021-30713 vulnerability comes shortly after Craig Federighi, Apple’s head of software, said that macOS suffers from an “unacceptable” level of malware, which he blamed on the diversity in the sources of software.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










