Contents:
The evolution of mobile devices has certainly improved our lives, but yet, security threats are rising. Although malware can affect any mobile operating system (OS), in this article I’m going to look at Android malware specifically, since Android is the most targeted OS. Actually, you may have already read a bunch of headlines around Android malware attacks.
Curious to find out how it all started? Would you like to avoid losing your security and privacy? If the answer to these questions is yes, keep on reading, as I will try to paint a clear picture on how to defend yourself against Android malware and answer some commonly asked questions.
Can You Really Get Malware On Your Android Device?
Are Android phones and tablets safe?
Long gone are the days when cyber criminals were only targeting computers. Now, they are likely to infect any piece of tech equipment you can imagine, starting from smart home ecosystems, to self-driving cars, drones, and AR/VR devices. And of course, your Android device is no exception.
How It All Started – The Early Days of Android Malware
First of all, let’s take a quick look at the origins of Android malware.
The first Android OS was released by Google back in 2008 and ever since has grown to be the most popular choice on the market. Currently, there are over 2.5 billion active Android devices worldwide.
At first, Android smartphones were not being targeted by malware since their popularity was growing gradually and attackers were mainly focusing on other widespread mobile operating systems of the time, such as Symbian. But as soon as its user base started developing more and more, by 2010, the platform was becoming a suitable environment for malware infections. Due to its open-source model, some illegal Android app stores were beginning to rise, and illicit apps were also starting to get included in Google’s official app store.
Spotted in 2010, AndroidOS.DroidSMS.A was the first Android Trojan. This was an SMS fraud app, which would subscribe your phone to various SMS services.
Back in the days of SMS subscription services, you could opt in to receive different alerts on your phone via text messages (i.e. ringtone of the week, joke of the day, etc.). Of course, you would also have to pay for each message you received. Once your phone got infected with this type of Android Trojan, it would automatically subscribe you to the service. And it would do it silently in the background without your prior approval, so you’d only notice it later on your phone bill.
During the same year, another Trojan was discovered posing as the TapSnake game. This particular Trojan would deliver the victims’ GPS location once their phones were infected over HTTP, which would then be identified by other phones that had the GPS Spy app installed.
In March 2011, yet another kind of malware, DroidDream, was added to the “collection”. Apparently, it was named due to the fact that it was programmed to run between 11:00 PM and 08:00 AM when Android phone users were most likely to be asleep and not using their device. A dream turned into a nightmare, this was a mobile botnet type of malware, which could gain root access to Android devices and steal unique identification information. At the same time, it could download other malicious apps without the user being aware and allowed hackers to control the device.
Android Malware Toolkits Were Becoming Mainstream
Going forward, Android malware attacks were showing no signs of a slowdown and the mobile cybercrime market was thriving. This type of malware was being sold illegally on the dark web. Malware-spreading kits were becoming widely available to be used by virtually anyone willing to do harm.
For example, the MazelTov Toolkit, dubbed an “APK Download System”, was created and discovered back in 2015 to facilitate malicious actors into uploading and spreading malware to Android devices. Attackers were granted control and provided with statistics on how successful their malware campaigns were. These toolkits were being sold for the Bitcoin equivalent of $3,000 and “customers” would receive everything they needed to effectively infect mobile devices.
Perks and benefits included registered developer accounts for three reputable Android markets of your choice, two domains, templates for a landing page, Traffic Distribution System (TDS) to add bot filtering and ensure the malicious websites received unique visitors per each desired geolocations, etc.

Image source: Security Intelligence
Popular Types of Android Malware
In this article, I’ve already briefly mentioned the Android Trojan virus, yet there are many other forms of malware that can infect your device. So, below I’ll list the most frequent types of Android malware and explain how each of them works.
#1. Trojans
As you could probably already tell from the attacks I’ve already listed in the Early Days of Android Malware section above, Trojans are malware disguised as legitimate software and apps. They can be used to harvest your sensitive data, spy on your activity, delete files, gain access to your device, download other malware, and more.
#2. Keyloggers
Keyloggers are malware designed to record your keystrokes, or when it comes to mobile devices, the information you type on your device. The fact that you can also find keylogger software openly on the surface web (and not only the dark web!) readily available to the general public and indexed in the search engines is somewhat shocking and disturbing. Sadly, these apps are usually masquerading as parental control solutions, while other developers are openly encouraging the surveillance of your friends and partners.
#3. Ransomware
Although this type of malware is more common on computers, this doesn’t mean your mobile device can’t get infected with Ransomware.
Through this kind of attack, all your files end up encrypted, and sometimes even your screen gets locked too. A message gets displayed on your device which asks you for a payment in return for decrypting your device.
In the image below, you can see an example of a ransomware attack targeting Russian users. The message displayed on the phone’s screen urges them to pay 500 Russian rubles ($8-$10) while they are also being threatened with a text message that would be sent to their contacts to let them know the victim was caught watching illegal adult content.
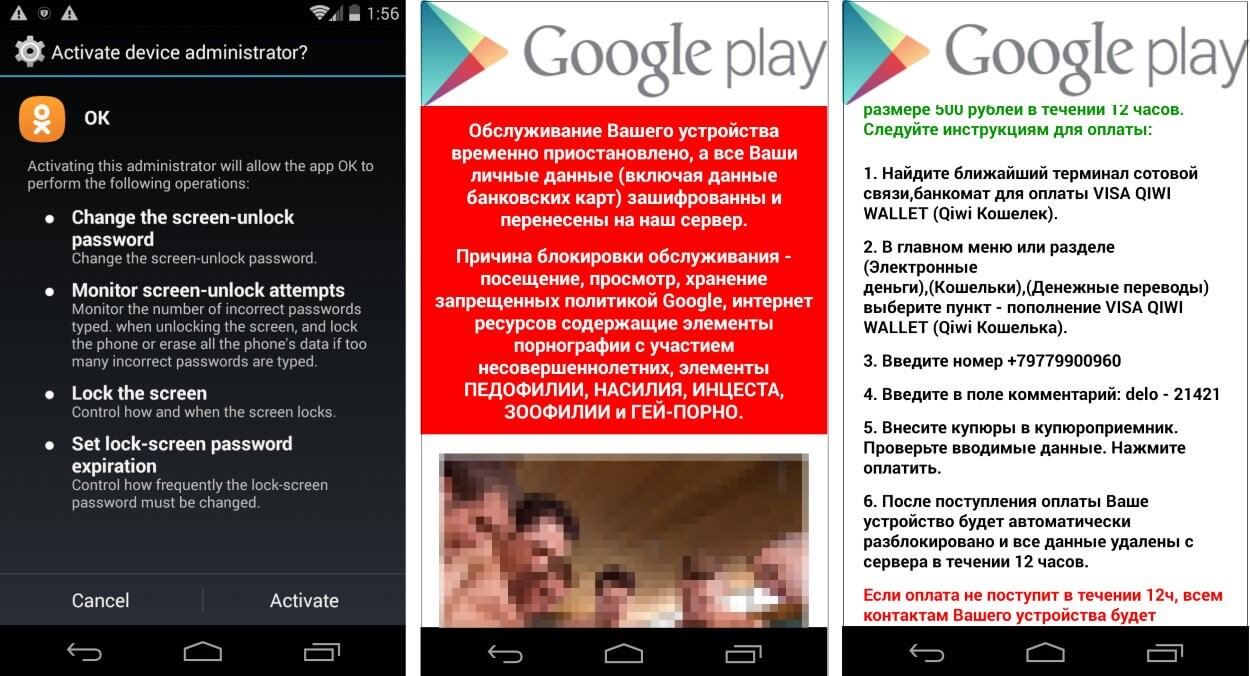
Image source: Bleeping Computer
#4. Spyware
Spyware is a highly common malware infection on mobile devices. You may have recently heard of it in the controversial WhatsApp Spyware attack when a discovered vulnerability found in the app could be exploited in order to make way for spyware on the victims’ devices.
So, what is mobile Spyware? It’s malware that enables attackers to access all the information on your phone, including contacts, calls, texts, and other sensitive information, and also hijacks your microphone and camera. Next, you can watch a short documentary created by a student who installed spyware on his phone, which got stolen. He shows how easy it is to spy on people and learn different things about them.
#5. Adware
If annoying advertisements are randomly being displayed on your device (full screen), even when you’re not browsing the Internet or using apps that have ads enabled, this means your mobile device is infected with Adware.
Here is what an Android mobile adware infection looks like:
Notorious Android Malware Campaigns Spotted in 2019
The pieces of malware below have been discovered this year alone, so notice how frequently these attacks can happen.
#1. Android/Filecoder.C
Targeting devices running Android 5.1 and higher, the FileCoder ransomware spreads via text messages that contain a malicious link. These messages try to trick you into installing an app that promises to use your own photos to create sex simulation imagery. But what this app actually does is encrypt all of your local files in exchange for a ransom ranging between $94 and $188.
For the full picture, here you can read the Security Alert around the FileCoder ransomware strain that we’ve recently released.
#2. SimBad
This malware campaign discovered in March 2019 impacted almost 150 million users. It was an adware strain found in 210 Android apps available on the official Google Play store. It was masquerading as the advertising kit named RXDrioder, which allowed attackers to control what ads were being displayed to users. The majority of the corrupted apps were shooter or racing games. RXDrioder was able to conceal the apps’ icons so users would find it more difficult to uninstall them.
In this adware campaign, attackers were abusing the legitimate advertising kit for their own profit to display the ads they desired. What’s more, they could make users’ browsers open at a particular URL to show even more ads. Or worse, open the Google Play and 9Apps stores to certain apps, so users could choose to engage in pay-per-install app monetization schemes.
But the malicious features of SimBad didn’t end here. The adware’s code could also display custom notifications and install additional apps from a server without the users’ consent.
#3. Agent Smith
This year in July, another malware campaign that infected over 25 million devices, dubbed “Agent Smith” due to its ability to bypass detection, was brought to light. This malware hacked apps and made them display more ads or took credit for the ads that were already displayed. Also, this piece of malware could identify well-known apps, such as WhatsApp, and replaced parts of their code, and impeded app updates.
The malware was hiding in certain apps, which after were downloaded, the malware would pose as a Google app under a name like “Google Updater”, and then the process of replacing code would begin.
It was found in the 9Apps third-party store and the malware’s developer was also trying to spread it into the official Google Play Store too, where 11 apps included code similar to a simpler version of the malware. However, the malware stayed dormant in this case.
#4. BianLian
BianLian had been previously known as the dropper that enabled Anubis, a banking Trojan spotted last year, to get installed on devices while being disguised as apps that were in high demand (think currency calculators, discounter apps, device cleaners, etc.). This malware strain would ask for permission to alter the device’s accessibility services and acted as a keylogger to steal banking login credentials. What’s even more frightening in this particular case is that the apps were actually working just fine, just like legitimate applications would, and they even had high ratings in the official Google Play Store.
Fast forward to July 2019, a brand new version of BianLian was discovered, which transitioned to a complex malware that brings new attack tactics. Now, it would actually record the devices’ screens so that users’ credentials could be stolen, allowing attackers to gain access to usernames, passwords, card details, and account numbers.
#5. Monokle
Android spyware known as Monokle and allegedly designed by one of the Russian government’s surveillance providers has been discovered this month as well. It has supposedly been out in the wild since 2016, and it’s been hiding in fake apps that look identical to highly popular Android applications, such as Pornhub, Evernote, Skype, or Signal. This spyware retrieves passwords and converts smartphones into listening devices. The tool is also able to record home screens when devices are locked to steal passwords, look at predictive-text dictionaries to understand the victim’s interests, record calls, and listen through the phone’s microphone.
#6. MobonoGram (Android.Fakeyouwon)
MobonoGram is a malicious app that used the open-source code of the original Telegram app. Its code was injected with malware and afterward published on the Google Play Store.
The fake app was targeting users in countries such as Iran, Russia, the UAE, and the US, where the official app is banned. The app could launch itself each time the devices were booted, or right after an app was updated or installed. Moreover, when the app was running, it was gaining access to a set of C&C servers to obtain malicious URLs, a browser user agent to hide the requests’ source, and some JavaScript codes. These JavaScript codes were created to engage in click fraud and profit from fake ad revenues.
Also, some URLs caused an infinite loop of requests to a malicious website. Such activity can drain the device’s battery as well as also possibly making it crash.
Between January and May 2019, researchers detected and blocked 1,235 infections belonging to the Android.Fakeyouwon malware family. The MobonoGram was downloaded over 100,000 times, and its developer (RamKal Developers) released at least five updates before it was eventually removed by Google from the Play store. Another malicious app named “Whatsgram” was published by the same developer.
How to check for malware on Android
So, what are the warning signs that could be telling you your Android device is infected with malware?
If your Android smartphone or tablet starts acting in a weird way and there are no obvious signs of why this is happening, this behavior may be due to malware.
Here are some common signs of Android malware:
Your battery is draining faster than usual.
If you’ve been using your Android device for roughly the same amount of time each day, yet you notice your battery is suddenly draining without an explicable cause, this may be due to a malware infection. Sometimes, malicious apps are using a lot of power resources. You should go to Settings, open the Battery section on your phone and see exactly which apps are using the most power. Try to identify if the apps that are showing up in there are genuine.
Your device heats up and performs poorly.
If you’re certain you’re not overusing the device and it heats up quickly and becomes really slow or your screen often freezes, we may be talking about malware. You should check the data usage to see which apps are using a lot of data. Access Settings, go to Data, and look at all the apps. Uninstall anything that looks fishy immediately.
Pop-ups and ads have started to appear randomly.
This is a clear sign of a malware infection, namely adware. No ads should be showing up on your screen for no particular reason. Remember: DO NOT click on any of these ads, no matter what they promise. You should identify which apps you’ve recently installed and remove all the suspicious ones ASAP.
You’ve noticed weird phone calls and texts.
If you see any unexplained messages or calls, they may be due to a malware infection, as this is a common way for it to replicate. For instance, if you receive strange text messages from friends, trying to lure you into clicking on suspicious links, their phones may be infected with malware that is trying to pass over on your device as well. Here you can see a clear example of a Ransomware attack (dubbed FileCoder), which spreads via text messages on Android. Whatever you do, DO NOT click on any fishy URLs or answer unknown calls.
Unknown apps have suddenly appeared on your phone.
Needless to say, if you notice any apps that you haven’t installed yourself, remove them promptly! And remember the “Google Updater” app I previously mentioned in this article? Some malicious apps will try to sound genuine or mimic other apps, so be extra careful.
Check for any hidden apps.
Some apps may not be visible on your Android device unless you know where to look for them. I know, this may sound scary, but here’s what you need to do. Just go to Settings – Applications, and look for any unwanted names on the list. From this menu, uninstall any suspicious apps right away!
Tips to Avoid Malware on Your Android Device
Here is how you can prevent your Android device from being attacked by cybercriminals.
#1. Set up a PIN/password/pattern or biometric authentication.
This should be the first security measure you apply on your Android device. Always make sure your phone can’t be accessed by someone who could, for instance, install spyware so they can monitor your activity.
#2. Turn your screen’s sleep timer to no more than 15-30 seconds.
Just in case you forget your device unsupervised, make sure any potential malicious actors have as little time as possible to gain access to it.
#3. Do not root your Android device.
Rooting is the Android equivalent of jailbreaking Apple’s iOS, which means you can unlock the operating system to customize it, install unofficial apps, apply OS updates by yourself, and so on.
However, keep in mind this practice involves serious security risks, so don’t do it, unless you are an expert or simply want to experiment and aren’t concerned with security.
#4. Never sideload apps.
In other words, do not install apps from third-party sources other than the official Google Play Store. Basically, when you do it, you bypass the security protocols from the Play Store. But it’s your choice if you want to take the risk.
#5. Delete any unnecessary apps.
Time for spring cleaning on your phone! If you’re not actually using an app, don’t just let it sit there and gather dust. It may someday be a security hole on your device.
#6. Be careful what apps you download (even from the official Google Play store).
As we’ve witnessed so many rogue apps evading malware detection and being introduced in the Google Play store, this means you can’t fully trust the tech giant’s official platform either. And imagine how many malicious apps could be hiding in third-party stores, so always make sure you download from reputable sources. Also, make sure you check the number of downloads and reviews.
#7. Pay close attention to the permissions requested by an app
For instance, an app may ask you to give it permission to identify your location, access your list of contacts, see your photos, etc. Here, Google explains how you can keep track of the permission rights requested by apps and how to enable and disable them.
#8. Update your system software and apps.
I can’t stress this enough – apply the latest updates as soon as possible. This is truly mandatory. Do not postpone the process. Here you can read a piece on the importance of software and apps patching.
#9. Encrypt your device.
An easy and obvious way to keep your data away from unwanted eyes is through encryption. How can you do this? Open Settings on your Android device. Under Security, you’ll see the encrypt device option. This encryption process can take up an hour or even more. Keep in mind this will drain your battery and begin the process with a fully charged and plugged-in device.
#10. Back up your device.
Always have a copy of your files handy in case you lose the ones stored directly on your gadget. You can either manually transfer files to your PC on your hard drive (or save them on external storage devices), or you can choose to back up your data in the Cloud. Of course, the latter is more convenient and saves you time, but it’s your choice to make. Some Android phones allow you to back up your app data, call history, contacts, photos, videos, settings, and text messages directly on Google Drive. But on other devices, you will have to use third-party backup options.
#11. Stay informed about the latest threats.
Continuous education is your safest bet when it comes to cybersecurity. You should be able to spot malicious cyber behavior and know how to defend yourself. If you’re a cyber-security newbie or if you’d simply like to learn more and stay on top of things, we recommend you subscribe to our newsletter and to our Cyber Security for Beginners course.
#12. Use an anti-malware security solution on your Android device.
For instance, Thor Mobile Security blocks any mobile threat before it gets the chance to infect your gadget. It makes sure all the URLs you end up on are safe (which means no phishing links, no ransomware, no credential-stealing or identity theft), and if they’re unsafe, they instantly get blocked.
How to Remove Malware from Your Android Device (A Quick and Easy Guide)
Well, you did your best to avoid malware on Android, but you’ve still ended up with a compromised device. Or you simply weren’t aware of the dangers lurking out there so you weren’t careful enough.
You may have clicked on a malicious link you received via text message or installed a rogue app. Now, your device has been acting weirdly and it’s clearly infected with a virus.
What can you do about it?
Obviously, if you don’t mind losing all your data, you can always perform a factory reset, which will bring your device to its initial state. But there are other steps you can take for a quick remedy.
Step #1. Restart your phone in safe mode.
Go to the Power Off options by pressing the power button on your phone. The power menu will appear. Tap and hold Power Off until the Reboot to Safe Mode option appears and choose OK.
Step #2. Uninstall any suspicious apps and the ones you don’t use.
You’re already aware of the importance of uninstalling apps that should not have been on your device in the first place or old ones that bring you no benefits whatsoever.
Step #3. Install a reputable anti-malware solution.
Don’t rely solely on Google Play Protect. This is the built-in antivirus protection on Android, which in July 2019, scored a protection rate of only 83.2% and 28 false positives in a test released by AV Comparatives. We recommend you install Thor Mobile Security for continuous protection against advanced malware, phishing, ransomware, identity theft, and so much more.
Bottom Line
Most of these Android malware attacks are successful because they’re based on false promises which sound appealing. But keep in mind, the threats are real. Always stay alert, keep your apps and system software updated, and never download anything on your mobile device from dubious places.
Has your Android device ever been infected with malware? Share your stories in the comments section below.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










