Contents:
A new strain of ransomware emerged on Android mobile devices. It targets those who are running the operating system Android 5.1 and higher. This Android ransomware strain has been dubbed by security researchers FileCoder (Android/Filecoder.c) and it spreads via text messages containing a malicious link.
How Does the Android Ransomware FileCoder Spread?
The SMS messages which are spreading Filecoder contain an invitation to download and install a sex simulator game app. Here is an example of how such an SMS can look like.
Usually, the message will be clickbait-y and will mean to entice the recipient into installing the app at least out of curiosity. Part of the bait is the promise that the app will use the victim’s own photos in creating sex simulation imagery.
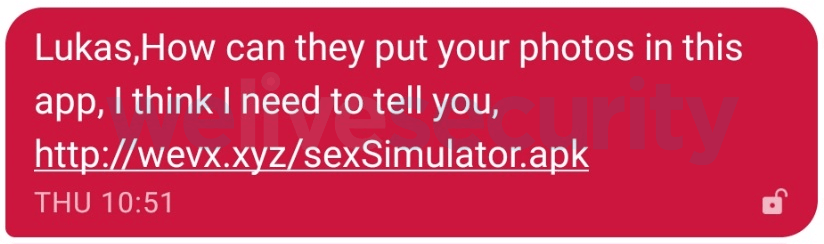
Message screenshot via WeLiveSecurity
Furthermore, security researchers have detected 42 languages in which the malicious text messages were coming in. The reach and potential user pool of the infected app were thus pretty big.
If the recipient has doubts about the harmlessness of the app, they may then research it online. Unfortunately, some websites and forums (including Reddit) were advertising the app (the posts were malicious themselves). If this helped relax the user into trusting the invitation, they would then install the app and proceed to use it as advertised.
It seems that the sex simulator game promised will indeed work, as not to alert the user. Still, after a short time, the Android ransomware will send out these messages to the user’s entire list of phone contacts.
After sending out the malicious SMS messages, FileCoder will encrypt the user’s local files (photos, notes, login data, messages and so on), displaying a typical ransomware message.
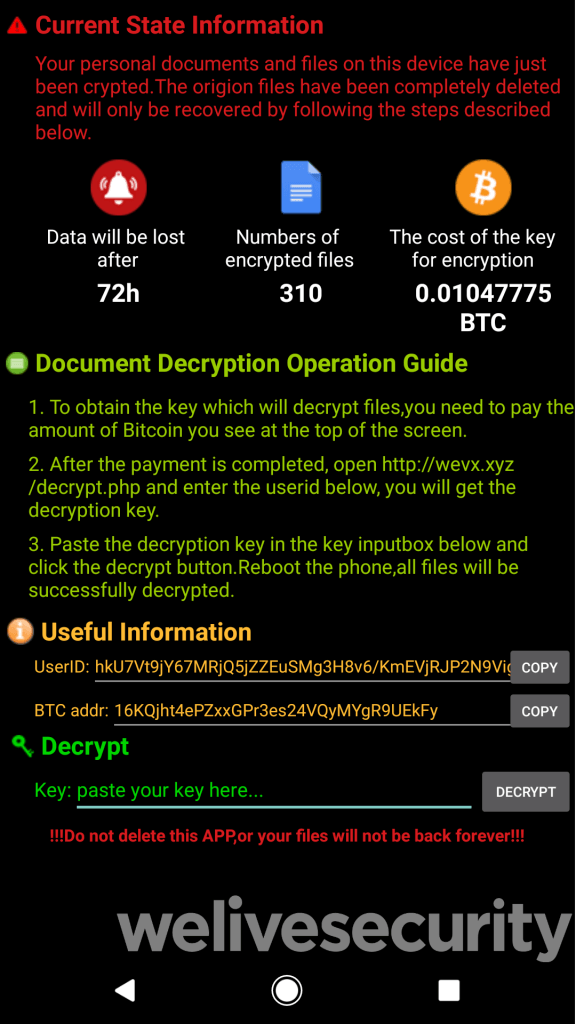
Ransom note screenshot
In the ransom note screen, the FileCoder creators threaten that the data will be permanently gone after 72 hours. However, security researchers have uncovered that the ransomware strain does not have the ability to delete the files.
Still, it will ask for a certain amount of money to be paid in Bitcoin before the user gets the decryption key. The equivalent in dollars for the Bitcoin money asked for ranges from $94 to $188.
Security researchers confirm that the FileCoder Android ransomware strain is not extremely dangerous. First of all, it doesn’t actually delete the locked data if the ransom is not paid within 72 hours.
Second of all, the value used for encrypting the key is hardcoded into the malware code, so with a bit of tech-savviness, the victims could decrypt the files themselves, without waiting for key.
Thirdly, unlike other strains of Android ransomware, the FileCoder infection doesn’t lock the screen of the phone. If your phone gets infected, you can still use it normally, it’s just the previously saved files that get locked.
The only thing which was coded into the malware in a more complex way was the Bitcoin address for payments. That one is dynamic, allowing the attackers to change it at any time and still get their money. This was probably a precaution, in case researchers or the police would get closer to uncovering the hackers’ identities.
Still, for most users, FileCoder poses a significant threat. If you receive a message inviting you to try a sex simulator app, don’t click it. Even if it comes from a friend you trust.
How to Stay Safe from FileCoder and Similar Threats
#1. Say no to steamy online proposals
First of all, learn to spot malicious proposals from the get-go. Sextortion is such a common tactic for scammers and hackers, that any invitation containing the promise of sexual images and content should raise the alarm.
Very few legitimate adult apps or websites are aggressive enough to invite you to use them directly. Most will simply rely on the fact that those who are interested will seek them out.
#2. Be Mindful of Messages from Friends: Not All Are Legit
Second of all, notice how devious the FileCoder strategy is: by sending you messages which are seemingly coming from friends, they make the message seem more trustworthy than if it came from a random spam address. Especially since the messages were targeting so many different languages.
Lots of other malware infections have a similar strategy, of sending malicious links to your list of online friends in order to infect them too. Stay on guard and don’t assume that all your messages from friends and contacts were really sent by them.
Tell-tale signs that a message from a friend might actually be malicious:
- Besides sharing an invite to a link, the message doesn’t say much
- The wording doesn’t necessarily sound like something your friend would use (just common words such as ‘cool’, ‘check this out’ etc.)
- The link is shortened or doesn’t lead to any legitimate domain you already know (like YouTube or Facebook)
- The message contains an attachment
These signs are just as suspicious whether it’s about a text message on your phone or an email and so on.
If you’re not sure whether a message is legit or not, just reach out to that friend and ask. You might alert them that their device is infected. Also, bear in mind that the same etiquette from real life should apply as netiquette, too: don’t open links from people you don’t really know.
#3. Keep Your Device Secure with a Mobile Security Product
With a good security suite for mobile devices, it’s much harder to become the victim of ransomware or any type of malware. Even if you do click on malicious links or make any other security mistakes, an intelligent cybersecurity product should still keep your Android safe.
Just like in the case of PCs and laptops, Antivirus is not enough, even if it’s next-gen. You also need a threat prevention solution, like our Heimdal™ Threat Prevention Home (which can be installed on up to three devices, including Android mobile devices), or the stand-alone product, Thor Mobile Security.
If your Android phone and other devices aren’t already protected by some other solution, here’s a month on the house for Heimdal™ Threat Prevention Home.

#4. Stay Up to Speed with the Latest Threats
We at Heimdal Security and we in the cybersecurity world, broadly speaking, have stressed time and time again how important education is. Cybersecurity training and a bit of self-learning are the best strategies for staying safe in the long run.
No cybersecurity software is infallible if the user behaves recklessly or doesn’t practice the most basic online security hygiene. For example (an oversimplified example), you can have the best-protected computer in the world, but a hacker will still be able to get into it if your password is ‘password123’.
By reading about the latest threats and how they work, you will soon discover that you’ve built a solid knowledge base. Armed with it, you should be able to tell if something is fishy as soon as you encounter a new threat.
Of course, I can wholeheartedly recommend our own educational resources to start with, but don’t stop there. Stay in the loop regardless of where you get your info and you’ll become less and less vulnerable to scams and malware.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










