Contents:
Drones, which are part of the UAV (unnamed aerial vehicles) group, have certainly seen an increase in popularity in the past few years. The global drone market is expected to grow from $14 billion in 2018 to over $43 billion in 2024. Long gone are the days when drones were only used for military purposes – today they can basically be purchased and flown by anyone. They can be affordable, come in all sizes, and can get as sophisticated as you can imagine.
Drones are now used for a multitude of purposes, ranging from recreational use, photography and filmmaking, agriculture, to surveillance and so many other uses. This technology will soon even be utilized by Amazon to deliver small packages, has already been employed by Domino’s to bring pizza, and UPS has used it to ship medical samples in the US.
But technology like this can equally be used for good and bad purposes and could easily turn into a sci-fi nightmare. And one of the biggest concerns here is that drones can be hadacked, or other drones can be used to hack electronic devices and gather data without one’s consent.
The malicious uses of drones
Drones can become a threat to your privacy since they can be used as spying devices.
Numerous cases have been reported so far. To name a few, a couple flew a drone to watch their neighbors and ended up being arrested, and burglars are now reportedly using drones to scout houses they intend to rob.
Privacy-related incidents may be so common since many countries don’t have any drone laws in place, or drone users are simply unaware of them. But there are some countries that did release regulations. For example, the UK is currently in the process of updating their Drones Bill, most probably as a response to the famous Gatwick Airport incident, when drone sightings stopped 1,000 flights from December 19-21, 2018 and affected the travel plans of around 140,000 people. The United States has also released regulations for drone users, and you can go through them here if you are flying your drones in the US.
Some drones can even see through walls by employing Wi-Fi and 3D imaging, and could easily create 3D plans of building that could facilitate criminals’ access inside them.
Not only that, other prominent issues are related to cyber-attacks, which may have seemed impossible to happen in the past but could now be carried out using drone technology. Drones can now be used to hack servers, spy on networks, extract data, and block communications.
Corporate networks can be heavily affected by the malicious use of drones, so companies need to have solid security measures in place to prevent unwanted access and protect themselves from cyber warfare attacks.
How hackers steal data with drones
Attackers can attach a small computer (such as Raspberry Pi) to a drone, fly it over places where they wouldn’t normally be able or allowed to enter, and then exploit Wi-Fi, Bluetooth, or RFID (Radio-frequency identification) vulnerabilities.
A cybersecurity company proved that a drone could basically be connected to any devices, like smartphones or laptops, during the 2014 Black Hat security conference in Singapore. They used a drone to intercept data from the attendees’ phones with a software dubbed Snoopy that ran on the minicomputer attached to the drone. It could mimic Wi-Fi networks that victims were connected to in the past and then they were able to steal any information that was used on the device, including bank details and passwords.
Also, other sources have shown that drones equipped with a radio transceiver could be used to hijack Bluetooth mice. This means that any other Bluetooth-connected devices could be accessed, such as keyboards, from which attackers could obtain keystrokes and figure out users’ login credentials.
Your own drone could be hacked easily
Imagine you are flying your drone, planning to take breathtaking shots of the spectacular location you are exploring and all of a sudden, the drone crashes and hits the ground. Or worse, it starts flying into random people and injures them.
One way this could happen is through GPS spoofing. This practice involves tricking a GPS receiver by transmitting a fake GPS signal. As a result, the drone will use the wrong location.
How malicious drones can be stopped
The market size of the anti-drone market is expected to reach $1.85 billion by 2024, which proves the fact that significant efforts are being made to fight hostile drones.
For instance, researchers funded by the EU are trying to find ways to detect and disable malicious drones through the KNOX project. Additionally, a recent study conducted by Fujitsu System Integration Laboratories and the Ben-Gurion University of the Negev addresses the same issue and analyzes methods to detect drones. What’s more, companies AT&T and Dedrone (a drone detection technology start-up) are collaborating to develop IoT solutions against malicious drones.
Below I’ve included a few methods used to detect rogue drones:
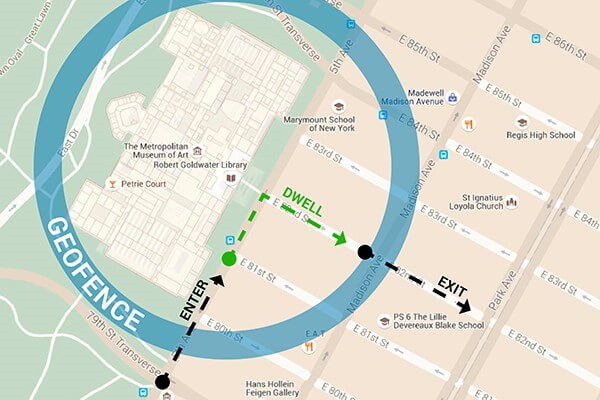
1. Geofencing
Geofences are virtual boundaries set up within physical locations where drones can be detected when they reach certain delimited areas.
How does geofencing work?
This is a location-based service and can be set up using GPS, Wi-Fi, Bluetooth, cellular data or RFID. In order to use geofencing, a developer or admin must create a virtual border around a specified location in GPS or RFID-enabled software. It’s quite a simple operation and can be represented, for example, by a circle drawn around a location on Google Maps. Technically, the geofence should generate a response the moment an unauthorized drone enters the defined area.
However, this technology may not always be so efficient.
Regular drones have built-in geofencing software, so you can’t unknowingly fly them over restricted areas, but malicious actors could build their own devices without this software or even hack the standard ones. Apparently, there is a website (on the open internet, not on the dark web) that sells hacks for drones manufactured by DJI, the market leader in unmanned aerial vehicles. The hackers’ solutions remove geofencing, altitude, and speed limitations.
2. Radar
Radar is already the standard go-to mechanism for aerial vehicles detection, so drones can also be detected using radar detection systems.
Drone radars use a combination of noise detection, thermal detection, radio signal detection, and signal identification. However, this method is not fully accurate, as it can easily mistake birds for drones.
Additionally, some drone radars also use microphones to recognize noise patterns, but this has proved to be ineffective in noisy urban areas.
3. Acoustic sensors
These sensors are able to detect drones that sometimes can’t be seen by radars.
Acoustic sensors recognize the unique sounds generated by different drone types and run them against a sound signatures database. If there’s a match, the system triggers an alert.
4. RF Scanners
Radio-frequency scanners examine the electromagnetic spectrum and find the specific transmissions from drones.
However, RF scanners will work when radio signals are present. Some drones operate without any RF signals and only rely on GPS, so this method will, in some cases, be inefficient.

5. Thermal imaging
Thermal drones use vision imaging cameras that work by detecting heat emitted by almost all objects and materials.
So, drone thermal cameras could prove to be powerful tools to detect unwanted UAVs.
Of course, there are many other methods out there (including hybrids) that are meant to stop malicious drones, which I haven’t mentioned in this article. Here are some more resources I recommend you check out if you want to become an anti-drone expert:
- 5 tips for choosing a Drone Detection Solution
- 8 Ways to Prevent Drones Infringing on Your Privacy
- Top 5 Drone Intercepting Methods You Should Know About
To Sum Up
Drones are certainly impacting our daily lives and will, without doubt, make up an important part of the IoT network used in our future smart cities. But sadly, they can be easily misused for malicious purposes. So, a lot of effort should be put into their cybersecurity and using the proper ways to detect and take down the ones which are threatening us.
What is your opinion on the issues related to drones and cybersecurity? Share your thoughts in the comments section below.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










