Contents:
Admin by Request is a Privileged Access Management (PAM) solution designed to help organizations manage local admin rights. Users appreciate its ease of use and cloud-based approach. Yet, according to user reviews, Admin by Request needs to improve its MacOS version.
We had to move to only using admin sessions due to the basic admin requests when attempting to install an app were a hit or a miss (It would work sometimes, but most of the time not). Also, if the app is profile based, it does not require admin permissions to install, this was a bit of a bummer to find out after the fact.
User review on Gartner.com
While Admin by Request is a critical piece of the PAM puzzle at a reasonable price, it doesn’t cover all bases on its own. To achieve complete privileged access security, you need to pair it with other PAM solutions to cover all aspects of access control.
If any of that sounds familiar, you might want to check this list of Admin by Request alternatives.
Key takeaways:
- Heimdal – A robust, all-in-one PAM solution with just-in-time access, secure remote access, and seamless security integration.
- Microsoft Entra ID – Microsoft’s identity platform with strong cloud-native PAM and conditional access controls.
- JumpCloud – A cross-platform directory service combining identity, device, and access management.
- BeyondTrust – Enterprise-level PAM with advanced session monitoring and zero-trust enforcement.
- LastPass – A credential management tool you can use to secure access, with built-in PAM features for safe password handling.
- Tenable – Specializes in detecting privilege-related risks through identity exposure and vulnerability insights.
- Netwrix – Offers real-time privilege tracking and compliance automation with least privilege enforcement.
- ManageEngine ADManager Plus – Simplifies active directory privilege delegation and user lifecycle management to secure sensitive data.
1. Heimdal – The best Admin by Request alternative
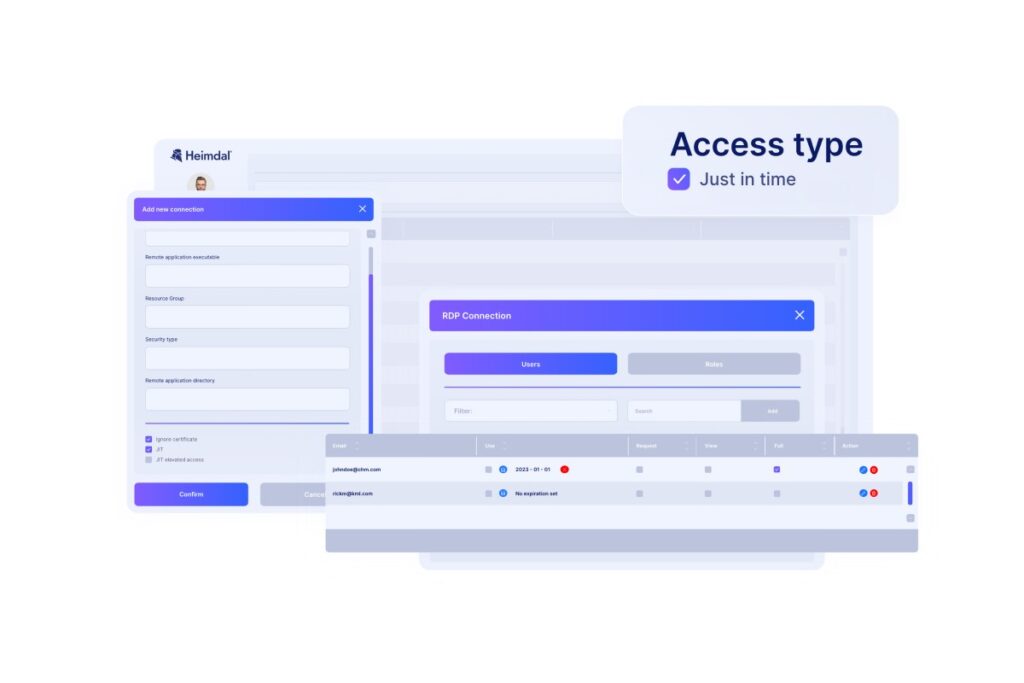
Heimdal’s PAM suite is a powerful Admin by Request alternative because it covers various aspects of offering secure access. Its robust feature set streamlines privilege management, enforces strict access control and session recording, and supports continuous compliance. Here’s why Heimdal stands out as an Admin by Request alternative:
- Ease of use: Approve or deny privilege requests directly from an intuitive dashboard or mobile device.
- Just-in-time access: Implement escalation periods for temporary privilege elevation. The user will only have high privilege access for the time they need it to perform a task.
- Real-time monitoring: Track privileged sessions and generate compliance-ready reports.
- Enhanced security: Integrates with Heimdal’s Endpoint and DNS solutions to prevent lateral movement.
- Compliance support: Ensures adherence to Cyber Essentials, GDPR, NIST, and more.
What do Heimdal’s customers say?
Stable product, the site is easy to manage and navigate. Its layout and short cuts are self explanatory. Secure and precise. (…) We have been using the product for some years and still can’t find any cons. It just works as we would like it to.
Main capabilities
- Total privilege management – Role-based access controls, real-time session tracking, privileged accounts auditing, and admin rights revocation.
- Just-in-time privilege elevation – Temporary access to reduce security risks and protect sensitive information
- Seamless integration – Works with Heimdal’s security ecosystem and third-party tools like ServiceNow.
- Advanced reporting & compliance – Detailed audit trails and compliance reports.
Pricing
Heimdal offers customized pricing that fits various business requirements and usage patterns. To see how Heimdal can ensure secure remote access and other services for your organization watch the video below and book a custom demo.
2. Microsoft Entra ID
Microsoft Entra ID is the former Azure Active Directory. It is a cloud-based identity and access management (IAM) service that integrates seamlessly with Microsoft 365 and other Azure services. Microsoft Entra ID enables secure identity management and conditional access policies.
Main capabilities
- Single sign-on (SSO) and multi-factor authentication (MFA)
- Privileged Identity Management (PIM) for just-in-time access
- Conditional access based on risk-based policies
- Integration with Microsoft security tools
Cons
- Complex setup and configuration for non-Microsoft environments
- Some advanced security features need higher-tier licenses
Pricing
Pricing is not publicly available for all features but follows a tiered model. Businesses typically need Microsoft 365 E5 or Azure AD Premium P2 for advanced PAM capabilities.
3. JumpCloud

JumpCloud is a cloud-based directory platform that unifies identity, access, and device management. It enables IT teams to manage user identities, secure endpoints and other critical assets, and enforce authentication policies across Windows, macOS, and Linux.
With a zero-trust security model, JumpCloud helps businesses control access to resources through single sign-on (SSO), multi-factor authentication (MFA), and conditional access policies.
Main capabilities
- Cross-platform identity and access management
- Remote user and device management
- Directory-as-a-Service (DaaS) with LDAP and RADIUS support
JumpCloud Cons
- Limited on-premises support
- Advanced security features only for premium plans
JumpCloud Pricing
Offers a free tier with paid plans starting at $10/user/month.
4. BeyondTrust
BeyondTrust offers a comprehensive PAM suite to prevent credential abuse, enforce least privilege policies, and secure remote access.
Its endpoint privilege management feature enables teams to control admin rights without hindering productivity. This Admin by Request alternative also offers session monitoring and auditing tools to track privileged activity and ensure compliance.
The platform can integrate with other solutions.
BeyondTrust Main Capabilities
- Zero-trust security
- Cross-domain visibility of identities
- Session monitoring and auditing
- Secure remote access
BeyondTrust Cons
- High cost compared to other solutions
- The UI is not intuitive
I have been helped multiple times and this is what I like about BeyondTrust Remote Support. It has a uniquely easy UI to go through with ease of integration. The cost is a little way too high and I would love it if it is lower in cost.
BeyondTrust Pricing
Custom pricing based on business needs.
5. LastPass
LastPass offers a robust password and privileged access management solution. This tool focuses on allowing businesses to securely store, share, and manage credentials. It offers a centralized vault for password management and multi-factor authentication.
LastPass includes privileged access controls, so only authorized users can access privileged accounts.
Main capabilities
- Secure password vault with sharing capabilities
- Password generator
- Multi-factor authentication
- Can create groups to organize users
Cons
- Past security breaches have raised concerns
- For advanced admin features you need to buy the enterprise plans
Pricing
Starts at $3/user/month for teams, with enterprise pricing available. You can test the solution for free for 14 to 30 days, depending on the package you choose.
6. Tenable
Tenable specializes in vulnerability management, providing continuous risk assessment and attack surface reduction. The Tenable Identity Exposure module offers privileged access solutions. This Admin by Request alternative integrates with various security tools.
Main capabilities
- Detects and mitigates identity-based security risks in privileged accounts
- Tracks identity changes
- Detects and fixes privilege creep and privilege misconfigurations
- Manages user permissions and enforces least privilege policies
- Integrates with security tools for continuous privileged access monitoring
Tenable Cons
- Primarily focused on vulnerability management rather than PAM.
Tenable Pricing
Custom pricing based on enterprise needs.
7. Netwrix
Netwrix offers visibility into user activity, secure access, password management, and sensitive data interactions. Its real-time alerts and detailed audit trails enable organizations to respond fast to suspicious behavior. By monitoring privilege escalations and tracking access patterns, Netwrix enforces least privilege policies.
Main capabilities
- Implements Role-Based Access Control
- Enforces the principle of least privilege
- Real-time alerts on privilege escalations
- Secures vendor and third-party access through MFA, just-in-time access, and privileged session logging
- Automates compliance reporting
- Secure remote access without VPN
Cons
- Limited integrations with third-party security tools.
Pricing
Custom pricing available upon request.
8. ManageEngine ADManager Plus
ManageEngine ADManager Plus is a comprehensive Active Directory (AD) management and PAM solution. Its focus is on streamlining identity and access control. It automates user provisioning, delegation, and reporting while ensuring compliance with regulatory standards.
ManageEngine ADManager Plus supports granular privilege delegation, enabling organizations to enforce least privilege policies.
Main capabilities
- AD user and group management
- Privilege delegation and reporting
- Automated user provisioning and deprovisioning
Cons
- Upgrade process is manual
- Failed updates may require restoration
Pricing
Pricing varies by features and enterprise needs.
The upgrade process is still very manual. I have had a couple of occasions where there has been an error during the upgrade and I’ve had to restore the entire service from backups due to an inability to complete the upgrade. Other ManageEngine products now feature a fully automated update process and I would like to see that in ADManager Plus.
Frequently Asked Questions (FAQ)
Why Should You Remove Local Admin Rights?
Removing local admin rights helps prevent unauthorized software installations. Doing this reduces malware deployment risks. Also, this measure limits potential security breaches caused by privilege abuse.
What Is the Principle of Least Privilege?
The Principle of Least Privilege (PoLP) ensures users and applications only have the permissions they need to perform their tasks. Applying PoLP is one of the PAM best practices that reduce security risks.
How Do You Implement Just-in-Time Access?
Just-in-time (JIT) privilege access limits the time for which privileged users get privileged rights. For example, an employee in the IT team will only get admin rights for the period they need to perform a task. You can enforce JIT with ease by using the Heimdal’s PAM suite, Microsoft PIM, or BeyondTrust.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security