Contents:
Researchers spotted a new ransomware operation in March 2023. It is called Akira and targets businesses worldwide, breaching corporate networks, stealing and encrypting data.
Threat actors claim to already have sixteen companies in their portfolio of victims from areas like finance, manufacturing, real estate, education, and consultancy. The ransomware demands can reach millions of dollars in some cases.
Another Akira operation emerged in 2017, but these two do not seem to be linked.
How Akira Ransomware Works
Upon execution, the malware deletes Windows Shadow Volume Copies from the machine. It achieves this by a PowerShell command: powershell.exe -Command “Get-WmiObject Win32_Shadowcopy | Remove-WmiObject”
After that, the ransomware will start encrypting files with the following file extensions: .accdb, .accde, .accdc, .accdt, .accdr, .adb, .accft, .adf, .ade, .arc, .adp, .alf, .ora, .btr, .ask, .cat, .bdf, .ckp, .cdb, .cpd, .cma, .dad, .dacpac, .daschema, .dadiagrams, .db-shm, .db-wal, .dbf, .dbc, .dbt, .dbs, .dbx, .dbv, .dct, .dcb, .ddl, .dcx, .dlis, .dsk, .dqy, .dtsx, .dsn, .eco, .dxl, .edb, .ecx, .exb, .epim, .fdb, .fcd, .fmp, .fic, .fmpsl, .fmp12, .fol, .fpt, .gdb, .frm, .gwi, .grdb, .his, .hdb, .idb, .itdb, .ihx, .jet, .itw, .kdb, .jtx, .kexic, .kexi, .lgc, .kexis, .maf, .lwx, .mar, .maq, .mav, .mas, .mdf, .mdb, .mrg, .mpd, .mwb, .mud, .ndf, .myd, .nrmlib, .nnt, .nsf, .nyf, .nwdb, .oqy, .odb, .owc, .orx, .pdb, .pan, .pnz, .pdm, .qvd, .qry, .rctd, .rbf, .rodx, .rod, .rsd, .rpd, .sbf, .sas7bdat, .sdb, .scx, .sdf, .sdc, .spq, .sis, .sqlite, .sql, .sqlitedb, .sqlite3, .temx, .tps, .tmd, .trm, .trc, .udl, .udb, .usr, .vpd, .vis, .wdb, .vvv, .wrk, .wmdb, .xld, .xdb, .abcddb, .xmlff, .abx, .abs, .adn, .accdw, .icg, .hjt, .kdb, .icr, .maw, .lut, .mdt, .mdn, .vhd, .vdi, .pvm, .vmdk, .vmsn, .vmem, .nvram, .vmsd, .raw, .vmx, .subvol, .qcow2, .vsv, .bin, .vmrs, .avhd, .avdx, .vhdx, .iso, .vmcx
The encryption process will bypass files from Recycle Bin, System Volume Information, Boot, ProgramData, and Windows folders. The same rule applies to Windows system files with extensions like .exe, .lnk, .dll, .msi, and .sys.
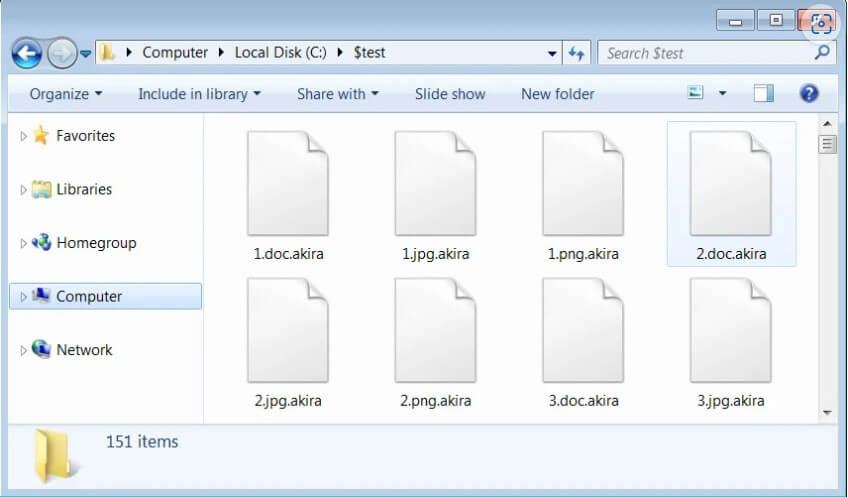
The encrypted files will have the .akira extension added to the file’s name. For example, the “named 1.doc” file will become “1.doc.akira” after encryption.
Akira also employs the Windows Restart Manager API to terminate any processes or services that might keep a file open and prevent encryption.
The Ransom Negotiation
Once into a network, Akira will move laterally, and spread to other devices. The goal is to gain Windows domain admin credentials so it can deploy the ransomware and infect the network.
Every encrypted folder will include the ransomware note called “named akira_readme.txt“. The note offers information about what happened to the files and links to the data leak site and negotiation site.
Each target receives a customized password for the negotiation site. Certainly, it is quite unique that this negotiation site consists only of a chat system used by victims to communicate with the threat actors. The leak site is also noticeable through its vintage look that enables visitors to navigate by typing in commands.
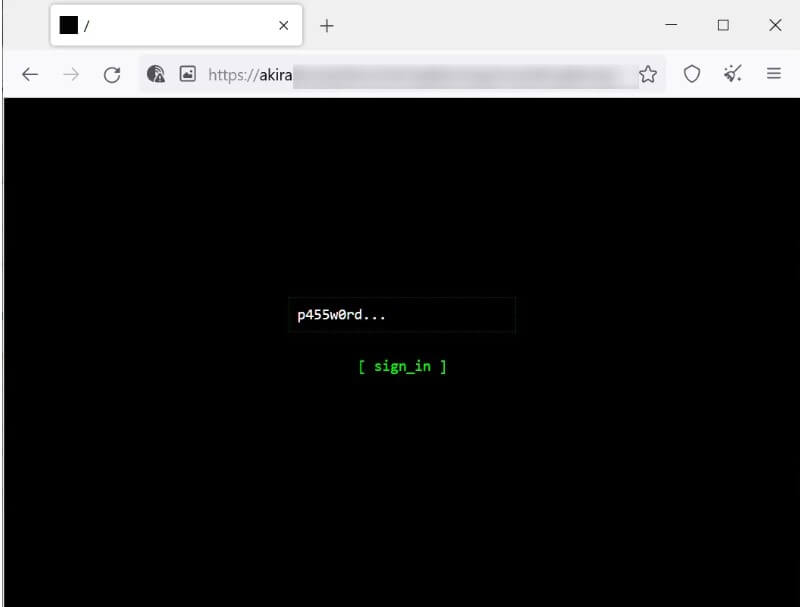
Keep in mind that Akira will not only encrypt your data, but it will also steal important corporate information to use in the extortion. If the victims refuse to pay the ransom, their data will be made public.
“As for your data, if we fail to agree, we will try to sell personal information/trade secrets/databases/source codes – generally speaking, everything that has a value on the dark market – to multiple threat actors at once. Then all of this will be published in our blog,” threatens the Akira ransom note.
Until now, hackers have published the data from four companies. That means data leaks between 5.9 GB and 259 GB. And the ransom demanded varied from $200,000 to millions of dollars. They negotiate the ransom with companies who want to stop data leaking, without the decryption key.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security