Contents:
A notorious hacker, previously involved in high-profile data breaches of InfraGard and Twitter, has now leaked a substantial LinkedIn database on a clear web hacking forum.
The scraped LinkedIn database was leaked in two parts: one containing 5 million user records and the other 35 million records.
Troy Hunt, a cybersecurity expert, examined the recent LinkedIn data leak and discovered a mix of legitimate data from user profiles and fabricated email addresses.
This data is a combination of information sourced from public LinkedIn profiles, fabricated emails address and in part (anecdotally based on simply eyeballing the data this is a small part), the other sources in the column headings above.
But the people are real, the companies are real, the domains are real and in many cases, the email addresses themselves are real.
Troy Hunt’s Blog (Source)
The analysis is now included in the Have I Been Pwned (HIBP) database for public awareness.
What type of data was leaked?
User ‘USDoD’ has freely supplied the CSV database, which contains recent (2023) data for LinkedIn Premium users, containing, among other things, the following information:
- Full names
- Email addresses
- LinkedIn profile IDs and URLs
- Job titles
- Employer names
- Education history
- Skills
- Languages spoken
- Brief professional summaries
Most of the information that was leaked is already public on LinkedIn, but the addition of email addresses makes it much easier to use for illegal activities.
Cybercriminals could use this information to compare email addresses from this breach to those from other breaches in order to find widely used passwords, improve their password-cracking techniques, or run phishing schemes.
Putting this kind of information into a searchable file also makes it easier for malicious actors to use it in identity theft or targeted fraud schemes, explains Restore Privacy.
The user that shared this information, USDoD, says that the public database includes data about renowned individuals like government officials, staff from NGOs, academic institutions, and financial organizations, and more.
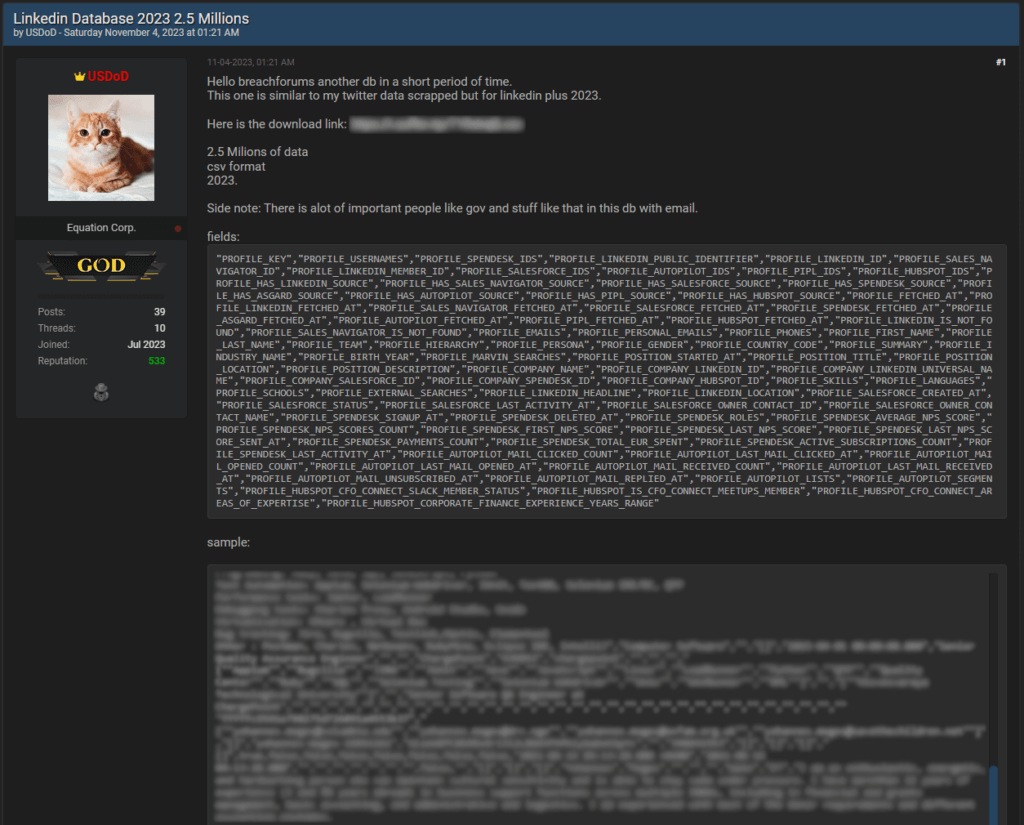
Forum Post (Source)
It’s worth noting that USDoD is the same hacker who last year broke into the FBI’s security platform InfraGard and leaked the personal information of 87,000 users.
What is Data Scraping?
Scraping is the process of extracting huge volumes of data from websites using automated tools, often crawlers and bots that can bypass anti-scraping measures by mimicking human-like user behavior.
International response to scraping practices
The UK’s Information Commissioner’s Office (ICO) and eleven other data security authorities from Canada, China, Australia, Switzerland, Norway, Argentina, and New Zealand put out a statement in August 2023 asking social media sites to strengthen their defenses against automated scraping.
The message reminded the websites that collecting information about users without their permission could be against data security laws, like the GDPR in Europe.
This happened before
This isn’t the first time that LinkedIn’s information has been leaked online. Threat actors were selling two scraped LinkedIn databases in April 2021. One had 500 million records and the other had 827 million records. A hacker sold a scrapped LinkedIn database in June 2021 that had information on 700 million users.
If you liked this piece, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








