Contents:
Researchers discovered that the Tap Busters: Bounty Hunters app had left their database open to the public for at least five months, exposing users’ private conversations.
Additionally, sensitive data was hardcoded into the client side of the app, making it vulnerable to further leaks.
With over one million downloads on Google Play Store and more than 45,000 reviews, Tap Busters: Bounty Hunters has an idle RPG rating of 4.5 stars.
In the game, players take on the role of bounty hunters trying to become masters of the galaxy. While traveling through different alien realms, players defeat villains and collect loot. Using idle game mechanics, players can move forward without constant input.
There were 349MB of unprotected data, including user IDs, usernames, timestamps, and private messages. If the data leaked had not been backed up and a malicious actor had chosen to delete it, it is possible that the user’s private messages would be permanently lost without a chance of recovery.
The developers left sensitive information hardcoded in the application’s client side, commonly known as secrets, along with an open Firebase instance.
Keys found were: fir ebase_database_url, gcm_defaultSenderId, default_web_client_id, google_api_key, google_app_id, google_crash_reporting_api_key, google_storage_bucket.
In most cases, reverse engineering can access sensitive data if it is hardcoded into the client side of an Android app.
No Response Was Given
Tilting Point, the company behind several other popular games with a large player base, created the game. Some of these games have received more than five million downloads. The app developer was notified of the data leak, but he did not disable public access to the database.
The app developers did not respond to questions from cybersecurity researchers about the duration of the instance’s public accessibility or the possibility that malicious actors could exploit hardcoded secrets, resulting in sensitive data breaches.
However, at the time of writing, the app’s firebase instance had so much data that threat actors were unable to acquire it all in a single run due to Google’s data transferring policies, effectively rendering the example as having a too large payload to be acted upon.
Android Apps That Aren’t Secure
Tap Busters: Bounty Hunters is one of the thousands of apps on the Google Play Store that data leaks could compromise.
Researchers examined over 33,000 Android apps earlier this year and discovered that the most sensitive types of hard coded secrets left exposed were API keys used to authorize projects, links to open Firebase datasets, and Google Storage buckets.
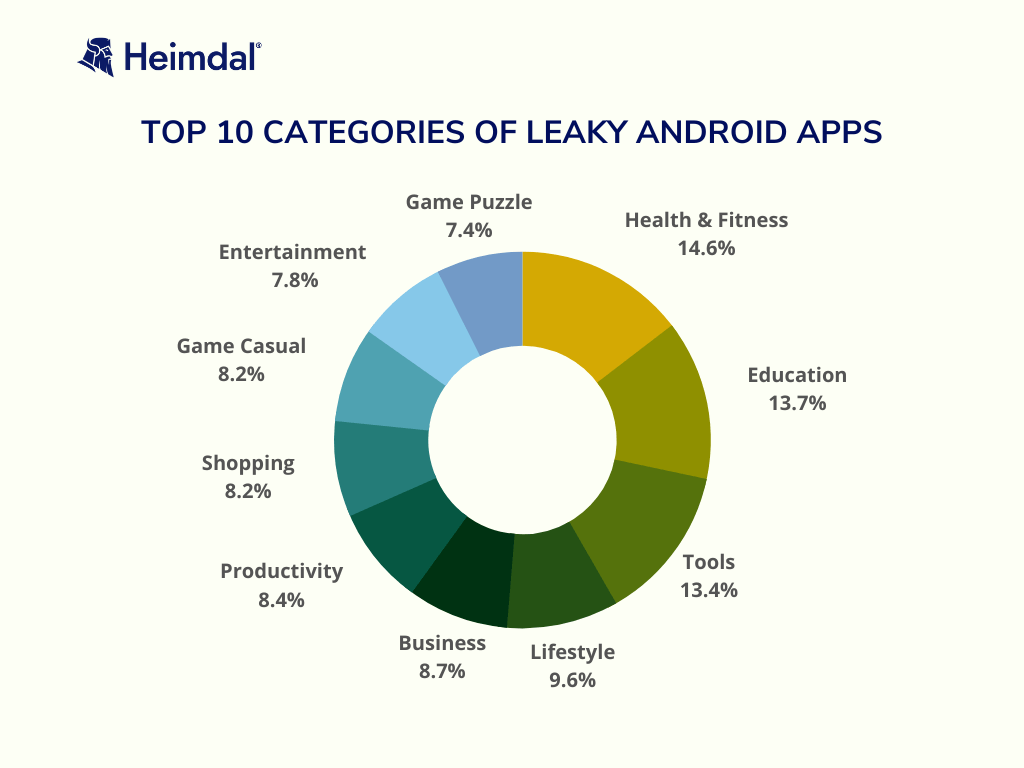
Over 14,000 apps had Firebase URLs on their front end, according to research conducted by Cybernews.
Six hundred of these were links to active Firebase instances. As a result, a malicious actor could access an app’s open database and potentially user data by examining its public information.
Health and fitness, education, tools, lifestyle, and business were the five app categories with the most hardcoded secrets.
How to Get Rid of Malware on Your Android Device
You may have clicked on a malicious link in a text message or installed a malicious app. Your device is now behaving strangely and is infected with a virus.
What are your options now?
You can always perform a factory reset, but remember that you will lose all your data. However, there are other steps you can take for a quick fix.
Step 1: Restart your phone in safe mode.
You can access the Power Off options by pressing the power button on your phone. The power menu will be displayed. Hold the power Off button until the Reboot to Safe Mode option appears, then select OK.
Step 2: Uninstall any suspicious apps as well as those you no longer use.
You’re already aware of the importance of uninstalling apps that should never have been on your device in the first place, as well as old ones that provide no benefit.

Heimdal® Network DNS Security
- No need to deploy it on your endpoints;
- Protects any entry point into the organization, including BYODs;
- Stops even hidden threats using AI and your network traffic log;
- Complete DNS, HTTP and HTTPs protection, HIPS and HIDS;
Step 3: Install a reliable anti-malware program.
It would be best if you did not rely solely on Google Play Protect. The Heimdal ® Threat Prevention Network operates at the DNS layer to prevent advanced and yet unknown threats from infiltrating your organization. You can detect advanced malware in your network, block malicious web content, protect against ransomware, phishing, identity theft, and other threats.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










