“On average, enterprises use about 45 tools to secure themselves. Medium businesses use about 15. Small businesses use five to seven, and they’d prefer using less, but regulatory compliance won’t let them.”
That’s from Andrei Hinodache, Heimdal’s cybersecurity solutions expert who’s done over 1,000 implementations in five years.
If you’re reading this, you’re probably somewhere in that spectrum: drowning in dashboards or trying to figure out if your existing security tools actually provide the endpoint security you need.
Here’s what I’ve learned from thousands of conversations with security teams. The choice between EDR and XDR isn’t really about features.
It’s about whether your security operations can actually keep pace with sophisticated threats while you sleep at night.
The Reality Behind the Acronyms
Endpoint Detection and Response does exactly what it says: it provides endpoint monitoring and threat detection for devices. EDR solutions monitor endpoints effectively, but that’s their limitation.
“EDR does a good job at monitoring and safeguarding users’ devices. But that’s as far as it gets,” Andrei explains during his security webinars.
“If somebody tries to break in and you have all of these separate layers, they will have a hard job, but not impossible.”
The problem isn’t that EDR solutions are inadequate for endpoint protection. It’s that advanced threats don’t restrict themselves to endpoint devices.
Take this example from Andrei’s live demo.
“I just double-clicked on something and seven DNS connections to very suspicious command and control domains happened in the background.
EDR would catch the file if it was known malware, but it wouldn’t see the DNS requests trying to download additional payloads.”
Your endpoint detection and response system sees the endpoint data.
It doesn’t see the network traffic, the email that delivered the payload, or the admin rights escalation happening through a different vector entirely.
This creates gaps that sophisticated threats routinely exploit.
When XDR Becomes Essential for Your Security Strategy
Extended detection and response isn’t just “EDR plus more stuff.” It’s a fundamentally different approach to analyzing data across your organization’s entire security stack.
“XDR brings under the same umbrella various security tools, no matter what layer of defense they address,” Andrei explains.
“It gathers and analyzes data from endpoints, network logs, cloud workloads, and email.”
An XDR solution integrates data from multiple security domains, providing threat visibility that circumvented traditional security measures can’t achieve.
Instead of siloed security tools generating separate alerts, you get comprehensive detection and response capabilities across your entire infrastructure.
But here’s where most XDR discussions go wrong. They focus on technical integration instead of the real problem it solves for security teams.
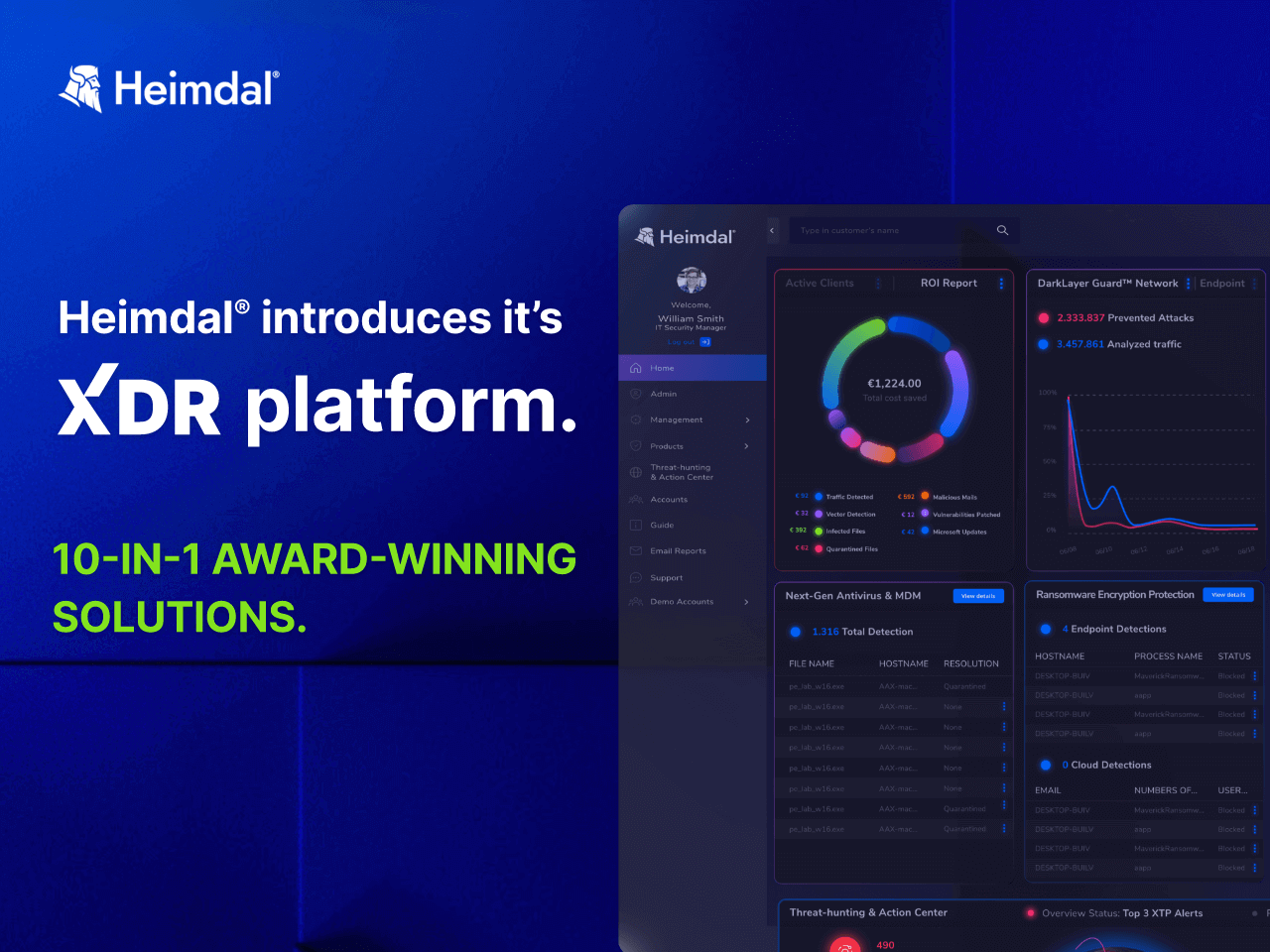
The Tool Sprawl Problem (That Nobody Talks About Honestly)
Here’s a statistic that should worry you: Gartner reports that enterprises manage an average of 45 security tools.
Even small businesses are forced into 5-7 other security tools just for regulatory compliance, creating an unwieldy mix of multiple security tools that security teams struggle to manage effectively.
“What does this mean for you?” Andrei asks his webinar audiences. “Five demos, three proofs of concept, one implementation per tool. Multiply that by the number of products you need.”
Ross Brouse, President of Continuous Networks, an MSP, put it more bluntly on our MSP Security Playbook podcast:
“My techs were spending more time jumping between security consoles than actually securing anything. We needed the single pane of glass that actually worked.”
The Hidden Costs of Fragmented Security Operations
When Andrei talks to MSPs and IT teams about their organization’s security posture, three problems come up every time:
- Alert fatigue: “If I have five different tools and they don’t talk to each other, I have data fragmented across five dashboards. Each tool might start responding differently, but if they don’t see what’s happening at the network level or email level, they might not take the best course of action.”
- Resource overhead: “Imagine 20 agents running on one computer. What does that do to the computer? It crashes it sometimes.”
- Skills gap: “You need somebody to manage this on a day-to-day basis. But cybersecurity personnel is scarce right now, and getting worse.”
The World Economic Forum reported in February 2023 that 3.4 million more skilled cybersecurity professionals are needed globally. That’s doubled since 2020, making it increasingly difficult to find security teams capable of managing multiple security layers effectively.
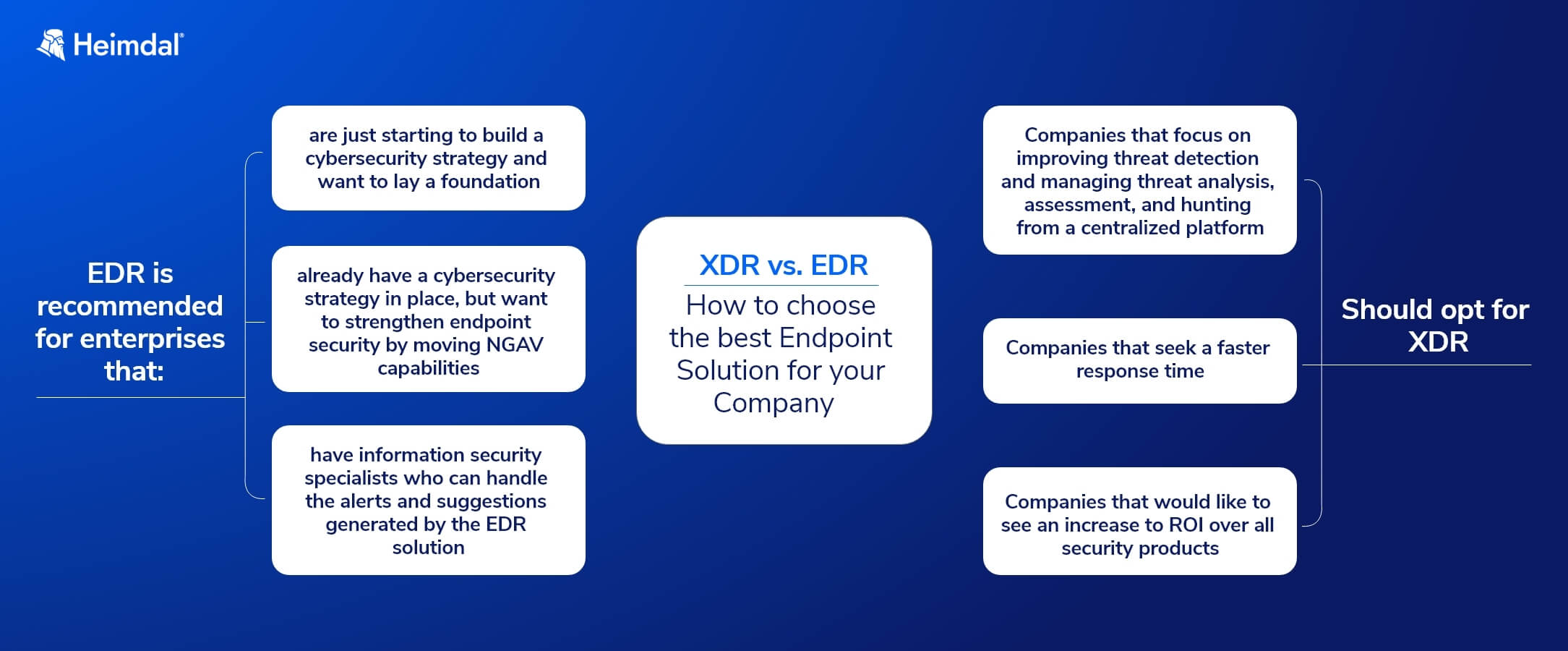
When EDR Makes Sense (And When It Doesn't)
Choose EDR if:
- You’re just starting to build a cybersecurity strategy
- Your primary concern is endpoint protection
- You have skilled security staff who can handle alert correlation manually
- Budget constraints force a phased approach
Choose XDR if:
- You’re tired of playing security whack-a-mole across multiple consoles
- You need to see attack progression across your entire environment
- Your team is already overwhelmed with alerts
- You want to reduce vendor sprawl
But here’s what the vendor guides won’t tell you: the choice often isn’t about what you want. It’s about what you can actually manage.
Real-World XDR vs. EDR: A Technical Breakdown
Let me show you the difference with a concrete example from Andrei’s live demonstrations that illustrates how each approach handles incident response.
The Attack Scenario
A user receives a phishing email and clicks a malicious link. Here’s how each approach’s detection and response capabilities handle the threat:
EDR Response:
- Detects malicious file execution on the endpoint through behavioral analysis
- Quarantines the file based on signature or heuristic detection
- Generates security alerts for manual investigation
- Waits for incident response team action
XDR Solution Response with Heimdal:
- DNS security blocks the initial connection attempt using threat intelligence
- If something gets through, endpoint protection catches behavioral anomalies using machine learning
- Email security would have flagged the original phishing attempt
- All three layers feed telemetry data to the unified threat hunting console
- Automated response based on the full attack context, accelerating security operations
“This is exactly what Heimdal does,” Andrei explains.
“We take all of these scattered layers and put them together.
It’s like trying to tear 500 pieces of paper with your bare hands: individually possible, but nearly impossible as a unified stack.”
This demonstrates the key differences between traditional security measures and modern threat detection approaches.
The MXDR Factor Comes When You Need Human Expertise
Here’s where the conversation gets interesting.
Both EDR and XDR are just technologies. They don’t automatically improve your organization’s security posture.
Dragos Rosioru, who led Heimdal’s Managed Detection and Response team, explains the reality:
“We don’t only do alert monitoring, we also do prevention. Is there something that the client should resolve? Is there any vulnerability that has not been exploited but could be exploited in the future?”
This managed service approach combines technology with human expertise for proactive threat hunting, going beyond what automated security tools can achieve alone.
What Good MXDR Actually Looks Like
Based on thousands of security incidents Dragos’s team has handled, here’s how comprehensive managed detection and response works:
For Low-Risk Alerts (Adware, PUPs):
- Initial investigation and classification of cyber threats
- User education about risky software and security threats
- Proactive recommendations to strengthen security posture
For Critical Threats (Ransomware, Zero-Days):
- Immediate endpoint isolation to contain advanced threats
- Emergency activation of additional security modules (even if not purchased)
- Daily client calls with timeline of security incidents
- Complete post-incident analysis and threat intelligence sharing
“Even if a customer does not have all Heimdal modules and we need some of those to contain or investigate, we enable them at no charge,” Dragos explains.
“Security is above money.”
The Hidden Economics On Why XDR ROI Isn't What You Think
Most security professionals focus on licensing costs when comparing EDR vs. XDR. That’s missing the bigger picture.
Andrei breaks down the real cost of multiple security tools:
“What does this mean for you? Five demos, three proofs of concept and one implementation. Now multiply this by the number of products you need.”
The math gets ugly fast.
If you need five security tools, that’s 25 vendor demos, 15 proof-of-concept projects, and five separate implementations – before you even consider ongoing management costs.
The Real Cost Breakdown
Based on Andrei’s many implementations, here’s what organizations actually spend:
Traditional Multi-Vendor EDR Approach:
- Initial evaluation: 3-6 months for 5+ vendor assessments
- Implementation: 2-4 weeks per tool (10+ weeks total)
- Training: 40+ hours per tool for IT staff
- Ongoing management: 2-3 FTEs just for tool administration
- Integration costs: $50,000-200,000 depending on complexity
Unified XDR Approach:
- Evaluation: 4-6 weeks total
- Implementation: 1-2 weeks maximum
- Training: Centralized, typically 20 hours total
- Ongoing management: 0.5-1 FTE
- Integration: Built-in, minimal additional cost
“In maximum one week you’re up and running with everything installed, configured, training done, day-to-day operations done, internal communications done,” Andrei explains about Heimdal’s XDR implementation.
But the real savings come from incident response efficiency.
Michael Warrer, Group CIO at NRGi, puts it simply: “Our team’s efficiency was considerably enhanced since we started using Heimdal.”
Matching XDR vs EDR to Your Industry Needs
Not all organizations need the same approach.
Here’s what Andrei has learned across different sectors:
Financial Services and Healthcare
These heavily regulated industries need comprehensive audit trails and compliance reporting.
“By regulation you need to have somebody responsible of cyber security,” Andrei notes. “Then you also have the situation with missing patches, antivirus, internet security, vulnerability scanning, and a SIM by law.”
XDR makes sense here because:
- Unified compliance reporting across all security layers
- Reduced audit complexity
- Better incident forensics for regulatory requirements
Manufacturing and Critical Infrastructure
Imagine this: I would have not had the DNS security to stop my WannaCry attempt,” Andrei demonstrates during his live attack simulations.
For industrial environments where a single ransomware incident can shut down production lines, prevention beats detection every time.
Small to Medium Businesses
“We have Partners here, we have MSPs here,” Andrei acknowledges. For smaller organizations, the choice often comes down to resource constraints.
EDR might work if you have dedicated security staff.
But if you’re like most SMBs where “you are the unsung heroes that need to do more with less while attackers have very few limitations,”
XDR’s automation becomes essential.
The Three-Phase Approach to Security Tool Migration
The biggest fear IT teams have about consolidation is creating security gaps during transition.
Andrei’s approach addresses this:
Phase 1: Assessment and Baseline (Week 1-2)
- Map existing security tools and their coverage
- Identify critical gaps in current architecture
- Document current alert volume and response times
Phase 2: Pilot Implementation (Week 3-4)
- Deploy XDR alongside existing tools (don’t rip and replace immediately)
- Configure integration with critical existing systems
- Establish baseline performance metrics
Phase 3: Gradual Migration (Week 5-8)
- Begin replacing redundant tools one layer at a time
- Migrate historical data where necessary
- Train staff on unified console
“We also have support customer success that would help you with that,” Andrei notes about the implementation process.
What 1000+ Security Implementations Actually Taught Us
After working with everyone from 50-person companies to enterprise organizations, here’s what Andrei has learned:
“The only way we can stay as safe as possible is using that multi-layered approach. But if you have them scattered, it complicates your teams. If you unify these and put them together, attackers have a much harder job.”
The Five Critical Questions
- Alert Volume: Can your team actually process all the alerts you’re getting? (Industry average: teams only process 40% of security alerts)
- Context Visibility: When an alert fires, can you see what happened before and after across your entire environment?
- Response Time: How long does it take you to understand and respond to a security incident?
- Skills Availability: Do you have the expertise to correlate events across multiple security tools?
- Vendor Management: Can you realistically manage relationships, training, and integration with 5-15 different security vendors?
Common Implementation Pitfalls (And How to Avoid Them)
Based on hundreds of implementations, these mistakes happen repeatedly:
Mistake #1: Choosing Based on Features, Not Workflow “Do not let the industry tell you what is the best,” Andrei warns. “You identify what you need and then you find the best for you, not what the industry tells you is best.”
Mistake #2: Underestimating Training Requirements Even with unified platforms, your team needs to understand how layers interact. Budget 20-40 hours for proper training.
Mistake #3: Ignoring Integration Requirements “All of them connect to one portal and can leverage each other’s intelligence to give you more value than you would get with individual tools,” Andrei explains. Make sure your chosen solution actually delivers on this promise.
Mistake #4: Focusing Only on Technology Remember Andrei’s three-legged stool: “People, processes, and products. Cyber security is not just made by products.”
How to See Through Security Vendor Marketing Claims
When evaluating XDR solutions, Andrei recommends focusing on these practical criteria:
Technical Integration Depth
Can the solution actually correlate events across layers, or does it just display data from different tools in one dashboard? Ask for specific examples of cross-layer detection scenarios.
Implementation Timeline
“In maximum one week you’re up and running with everything,” should be the standard. Be suspicious of solutions requiring months of professional services.
Support Model
Does the vendor provide actual security expertise, or just technical support? Dragos’s MXDR team example shows the difference: “We don’t only do alert monitoring, we also do prevention.”
Total Cost of Ownership
Look beyond licensing. Factor in implementation, training, and ongoing management costs over three years.
The Bottom Line For XDR vs EDR
When comparing EDR vs XDR solutions, the decision isn’t automatically in favor of either approach. It depends on what your security strategy can actually execute.
If you have a small, skilled security team that can effectively manage and correlate security related data from multiple security tools, a best-of-breed EDR approach might work for your endpoint protection needs.
But if you’re like most organizations (understaffed, over-alerted, and trying to do more with less), an XDR solution’s unified approach isn’t just convenient. It’s necessary for survival in today’s threat landscape.
As Morten Kjaersgaard, Heimdal’s Founder, puts it:
“The goal is actionability and proactive threat mitigation rather than reactive threat mitigation. Predictability enables security teams to respond faster to security incidents.”
The choice isn’t really about choosing between EDR or XDR solution features. It’s about fragmented reactive security versus a comprehensive cybersecurity strategy that can detect threats before they become major security incidents.
Which approach helps your security operations sleep better at night?










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








