Contents:
In this article, we’ll go over what penetration testing as a service is and how it works. You’ll also learn about the different types of services and the difference between penetration testing and vulnerability assessment, and much more!
So let’s jump right into it!
Penetration Testing as a Service (PTaaS) is an innovative service for IT professionals. It provides easy access to all the resources they need to conduct and act upon point-in-time and continuous penetration tests.
PTaaS is designed to help businesses build successful vulnerability management programs to find, prioritize, and fix security threats quickly and efficiently.
In IT security, it is common for businesses to hire reputable and ethical hackers–known as white-hat testers–to proactively attack and scan their networks, servers, or applications for potential hacking vulnerabilities.
While this may sound counter-intuitive, inviting outside entities to try and breach a company is one of the best ways to identify and fix difficult-to-spot security weaknesses. And that is specifically why penetration testing is an important, widely-recognized security best practice.
For example, in the summer of 2021, the White House released a memo encouraging business leaders to take urgent action against ransomware threats. One of their guidelines addressed the importance of penetration testing.
From the memo:
“Use third-party pen testers and perform a full audit of your systems to ensure they are secure and your ability to prepare against sophisticated attacks. Many ransomware criminals are aggressive and skilled, so you have to be careful.”
How Penetration Testing as a Service (PTaaS) Works
In the past, all pen-testing information would be delivered in a written report after completing the testing process. This often made it difficult for in-house teams to decide which issues needed to be fixed first.
While this information was helpful, its delayed nature often made it hard for security teams to fix and prioritize test results.
Today, automated penetration tests provide a way to solve this problem by allowing customers to view their data in real-time through an executive dashboard.
This dashboard displays all relevant data before, during, and after the test is performed. Pen testing services have also been improved- vendors of PTaaS offer resources for parsing vulnerabilities and verifying the effectiveness of remediation.
Typically, PTaaS vendors provide their customers with a knowledge base to help in-house security teams fix vulnerabilities. They also offer optional support from the vulnerability researchers who found the weaknesses.
No matter what your organization’s size, you can benefit from PTaaS. The best platforms offer a wide range of features, including advanced testing programs designed for large organizations or reporting features tailored to small businesses with many regulatory requirements.
But let’s discuss the benefits of Penetration Testing as a Service in more detail.
Perks and Benefits of Penetration Testing as a Service (PTaaS)
Undoubtedly, one of the most significant benefits of managed product solutions is that it gives customers control over their product. In addition, companies without experience in security will have a partner and platform to provide them with everything they need to set up a successful MRM program.
PTaaS cloud platforms do a lot of the administrative work for customers so they can concentrate on progress and status. In addition, the platforms make it easy for customers to request and scope new engagements.
Other significant benefits include:
- Flexible purchasing options: You can choose between automated, manual, and hybrid pen test services that can be budgeted for during a monthly or yearly subscription or on an as-needed basis.
- Continued access to real-time data: You will have instant access to the latest and up-to-date data related to any vulnerabilities or exploits. They change over time, and the presented information is updated to reflect the newest version of the exposure or exploit.
- Flexible reporting options: Reporting is one of the most challenging things to do in your PTaaS platform. Luckily, our reporting options are flexible and will meet the needs of multiple stakeholders.
- Automation: Automation makes vulnerability scanning for external networks and unauthenticated web applications easier to conduct.
Types of Penetration Testing Services
With PTaaS, you can use it for various reasons, such as finding vulnerabilities across your company’s infrastructures, including web applications, networks, APIs, and mobile applications.
Network Penetration Testing
A PTaaS solution will allow you to grant access to your network, enabling it to perform network security testing using methods such as port scanning, configuration benchmarking, traffic fuzzing, virus scanning, and fingerprinting. This can allow investigation of vulnerabilities like:
- Weaknesses in security tools like firewalls and intrusion detection/prevention systems.
- Weaknesses in network hardware, such as switches and routers.
- The vulnerabilities commonly exist in servers, workstations, and other devices deployed on the network.
Network-based PTaaS can offer network protection against a variety of attacks, such as attacks exploiting vulnerabilities or misconfigured security tools. With a reliance on networks, your business can have the protection it needs and prevent DNS and man-in-the-middle (MiTM) attacks.
API Penetration Testing
Another great use of PTaaS is testing APIs. Unfortunately, with many IT systems exposing APIs and providing public documentation, they’re a prime target for attackers.
API documentation is one of the most important aspects of a successful API. PTaaS will learn API structure and commands by using a standard like OpenAPI or importing a list of rules. PTaaS solutions can identify issues like:
- Poor API authentication;
- Code injection vulnerabilities;
- Lack of resource rate limiting;
- Sensitive data leaks.
Mobile Application Penetration Testing
Most organizations provide mobile applications for their employees, partners, and customers. Frequently, these apps are used on personal devices, making them more vulnerable to attacks.
You’re missing out if you have an on-demand mobile application and aren’t using PTaaS. PTaaS can scan for and identify various issues to make your app more user-friendly, such as:
- Weaknesses with WiFi networks;
- Phishing messages sent to user devices;
- Malware in a mobile application or device;
Complementing Penetration Testing with Dynamic Application Security Testing (DAST)
Part of the purpose of penetration testing is to ensure your applications and network are secure, but manual penetration testing can be time-consuming, expensive, and not scalable. Penetration Testing as a Service (PTaaS) handles this by managing pentests more often and with less cost while being highly effective.
With more and more companies adopting DevOps and Continuous Integration & Continuous Delivery (CICD), there is an increasing need for security testing automation. Automation helps remove bottlenecks caused by security-related tasks and provides developers with a direct line of communication.
What About External vs. Internal Penetration Testing?
Penetration testing can be done internally, or by using a third-party consulting company (externally).
External Penetration Testing
External penetration testing evaluates whether enterprise-level resources are prepared for malicious attacks against the public Internet.
During an external penetration test, the assessor tries to gain entry into the network’s internal assets by exploiting vulnerabilities in the external infrastructure.
Alternatively, the tester may attempt to access privileged data through external facing assets like email, passwords, websites, and file shares.
The attacker finds publicly-available information about the in-scope assets, including open ports, vulnerabilities, and general information about the organization’s users.
Once they can successfully breach the perimeter (i.e., get inside), their objective of the external penetration test is met, and they move on to the internal penetration test.
Internal Penetration Testing
As part of a penetration testing assessment, internal penetration tests can help identify how far an attacker can move once they’ve breached your network externally.
Internal penetration tests can either leverage an exploited asset from an external penetration test or use a testing machine or laptop on the inside of the network to assess security risks.
Running tools through an exploited external asset is often unstable, so the preferred method is to test with a testing machine or laptop.
This method exploits less-important systems and then finds intelligence on these systems to attack more important ones in the network.
Once the attacker has gained access to your domain admin or your organization’s most sensitive information, the test is usually complete.
What Should You Expect from a PTaaS Platform?
The PTaaS security testing model is an add-on to the standard penetration testing service and has some limitations compared to one-time testing.
For example, personalizing solutions or working in complex environments is more challenging. However, the benefits outweigh the burdens.
Here is what you should expect from a PTaaS platform:
- Constant monitoring of your network for malicious activity;
- On-demand access to Penetesters and Security Engineers;
- A vulnerability assessment finds if the software is at risk of attack.
- SDLC (Software Development Lifecycle) integration;
- Real-time alerts to report vulnerabilities.
Challenges in Using Penetration Testing as a Service
The PTaaS model may only work for some customers. A dedicated consultant will be the best option if your environment is complex and specific technologies are out of scope.
Another challenge with the PTaaS model is that it can’t be customized to meet specific user needs. Furthermore, PTaaS models may need to be revised for organizations testing industrial control systems.
When companies automate vulnerability orchestration and configuration management, they can manage their budgets more efficiently, allowing them to run more tests. They may not be able to take on additional testing cycles, but they will in the future.
Some security programs cannot remedy the vulnerabilities, especially when they’re newer and underfunded. This can cause a big problem for many organizations that don’t have much money for extra tests and remediation efforts.
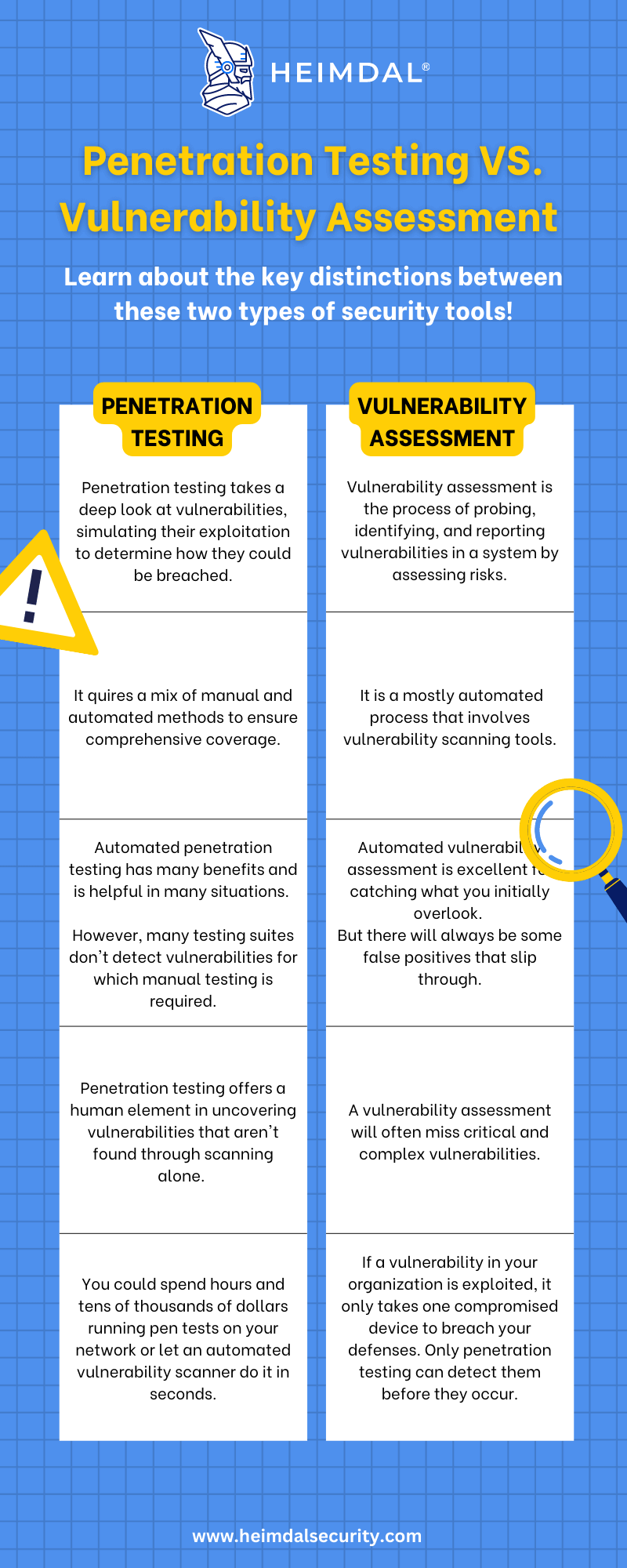
What’s the Difference Between Penetration Testing And Vulnerability Assessment?
Vulnerability assessment is the process of analyzing vulnerabilities in a system. Penetration testing refers to actively exploiting those vulnerabilities to determine their severity, authenticity, the potential for causing damage, and other insights.
The goal of both vulnerability assessment and penetration testing is to assess the security strength of your systems. While there are many similarities, there are also notable differences between these types of tests that we’ll highlight in the piece.
Below is a little comparison table for you to get the bigger picture:
Wrapping Up
An agile development process comes with some risks, but Penetration Testing as a Service is a way to address those risks. It’s more affordable, suitable for an agile environment, and faster than traditional penetration testing—a good solution for people who want relief from costly and endless security complaints.
Heimdal® Threat Prevention is a pioneering DNS security solution, and it might be just what you’re looking for. It offers a full suite of cybercrime intelligence, Machine Learning, and AI-based prevention that helps protect your employees with the latest technology and the best protection possible.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








