Contents:
You can encounter many online threats while browsing the Internet. It is important to know that these threats don’t hide only on malicious websites. Internet ads – which are ubiquitous – can be a source of danger, even on otherwise legitimate websites, through malvertising. But what is malvertising and why is it risky?
The answer to that lies in the very nature of internet advertising. Websites do not retain complete control over the ads displayed on their pages. If you are not careful enough, your computer can accidentally be infected with malicious software when visiting the most legitimate websites, even the ones you visit as part of your everyday Internet browsing.
How is it possible? The answer lies in the insidious nature of Malvertising.
What Is Malvertising?
Malvertising or malicious advertising, a fairly new concept, is the use of online advertising to spread malware. It usually implicates injecting malicious or malware-laden advertisements into legitimate online advertising networks and web pages.
Because advertising content can be incorporated into high-profile and respectable websites, malvertising gives malefactors the perfect occasion to push their attacks to web users who might not otherwise see the ads, due to firewalls, more safety precautions, or the like.
To understand what is malvertising, it’s important to note how hard it is to pinpoint to the exact origin of the problem. Cybercriminals use the same advertising schemes as real companies, except that malvertising will either attempt to download malware directly to visitors’ devices upon viewing or redirect visitors to websites that scatter viruses, ransomware, or other malicious programs.
Malvertising is a favorite medium for criminal behavior because it exploits consumer trust in organizations and advertising networks. It can also be easily spread across a large number of legitimate sites without directly compromising those sites.
Definition of malvertising:
The interesting thing about infections delivered through malvertising is that it does not require any user action (like clicking) to compromise the system and it does not exploit any vulnerabilities on the website or the server it is hosted from… infections delivered through malvertising silently travel through Web page advertisements.
Because both malvertising and adware (another form of malware affecting online advertisements) attacks depend on online advertising to do their harm, they are frequently confused. But there are some differences. The biggest one is that malvertising attacks come from ads on legitimate websites while adware is malicious software (that you were probably tricked into installing) that is already on your computer.
How Malvertising Works
Malvertisements are dispersed through similar techniques as typical online ads. Impostors can initiate malvertising attacks by purchasing ad space from advertising networks and then submitting infected images with malicious code.
Their expectation is that legitimate websites will run these ads and the advertiser won’t be able to distinguish between reliable ads and damaging ones, leading to contamination of devices, before the malicious ads are detected and eliminated.
Once the malicious ads get the advertiser’s approval, they are served to legitimate websites. Hackers can utilize redirects to send users to a malicious site, and victims will have no idea what it’s happening because they expect redirects when clicking on an advertisement.
During the time spent on the malicious site, code will run in the background, aiming to download malware onto the computer.
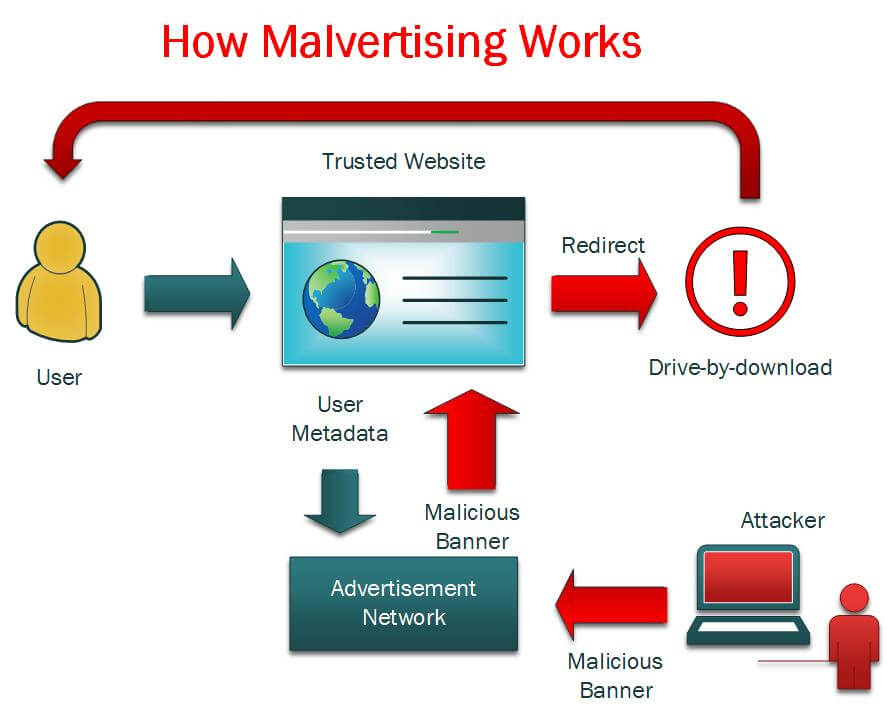
This accidental download of malware is known as drive-by download. Attackers frequently use drive-by attacks where victims don’t even need to click on the ad to activate the malicious code. They just need to load the web page hosting the advertisement. Clickers will then be sent to a landing page, which exploits all the liabilities in their browser to access their devices.
New forms of malvertisements can even install malware on visitors’ devices right from the legitimate website that is showing the ad and without any visitor’s activity.
What Is Malvertising’s Main Risk?
When it comes to malicious ads and malvertising campaigns risks here’s what you should know:
Attackers can get your financial information. Some malvertising is created to mislead you into giving up personal information such as financial information. If attackers obtain access to your bank account numbers or banking passwords, they could steal money from you before you even observe.
Impostors might be able to hoard your credit card debt. If hackers succeed in stealing your credit card information, they might use your cards to buy stuff for themselves. If you are one of those people who doesn’t usually check their credit card bills, you might end up paying for other people’s purchases.
Your devices can get infected. Malvertising is also able to install all sorts of viruses and malicious code on your device. You might not even know about their existence, but they can be used by hackers to steal your passwords, follow your keystrokes or acquire full control of your computer.
How to Identify Malvertisements?
Can we tell which advertisements are authentic and which might be dangerous for us?
As hackers’ techniques are more and more advanced, we can’t immediately notice if an ad is legitimate or not. If you understand what is malvertising by now, you can probably tell how much a malicious ad can look like a legitimate one. Nevertheless, there are a few things we can do that will minimize the risk derived from a malvertising attack.
- Don’t click on ads promising things that are hard to believe such as miraculous cures. The rule says if it sounds too good to be real, most likely it is;
- Ads must look like they were created by a professional graphic designer. If they don’t, don’t click on it;
- Don’t click on ads that have spelling errors;
- Don’t click on ads that don’t correspond to your recent/typical search history.
Even if hackers mainly attack Windows users, a malvertising campaign focused on a browser or plug-in can definitely infect a Mac, Chromebook, Android phone, or iPhone.
Mobile devices can be even more affected by a malvertising campaign since the majority of people aren’t as cautious or have the same protection that they normally have on their computers.
What makes a mobile device a prime target for malvertising is the fact we are always using it for shopping, guidance, messaging, and so on.
How to Protect Yourself against Malvertising
- Turn on click-to-play for your browsers;
- Use adblockers to block all ads;
- Use all-round antivirus software to prevent auto-download of malware;
- Try not to use Flash and Java (Since there are many Java vulnerabilities and Flash vulnerabilities used as entry points for malvertisement attacks;
- Update browsers and plugins to avert malvertising attacks
- Identify ads that seem illegitimate
- Search for a company without clicking on an ad;
- Resist clicking on ads, even if they appear to be from well-respected companies;
- Stay informed about the latest malvertising scandals.
Wrapping Up
Malvertising will not disappear any time soon, therefore companies and individual users need to know how to recognize it and prevent it. If you manage a team, make sure everyone on it understands what is malvertising and how to steer clear of it. As always, education and cautiousness are vital and can significantly mitigate the risks and keep your data safe.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










