Contents:
An exploit is a piece of software or code created to take advantage of a vulnerability. It is not malicious in essence, it is rather a method to prey on a software or hardware security flaw.
Threat actors use exploits to install malware, Trojans, worms, and viruses, or to launch denial-of-service (DoS) or other types of cyber-attacks. Both threat actors and security researchers actively look for exploits. Hackers write exploits in order to use a vulnerability for their malicious purposes, while researchers create them as a proof of concept (PoC) that will help patch the vulnerable software and thus bolster security.
Also, threat actors can buy or rent exploits or exploit kits from the Dark Web.
How Do Exploits Work?
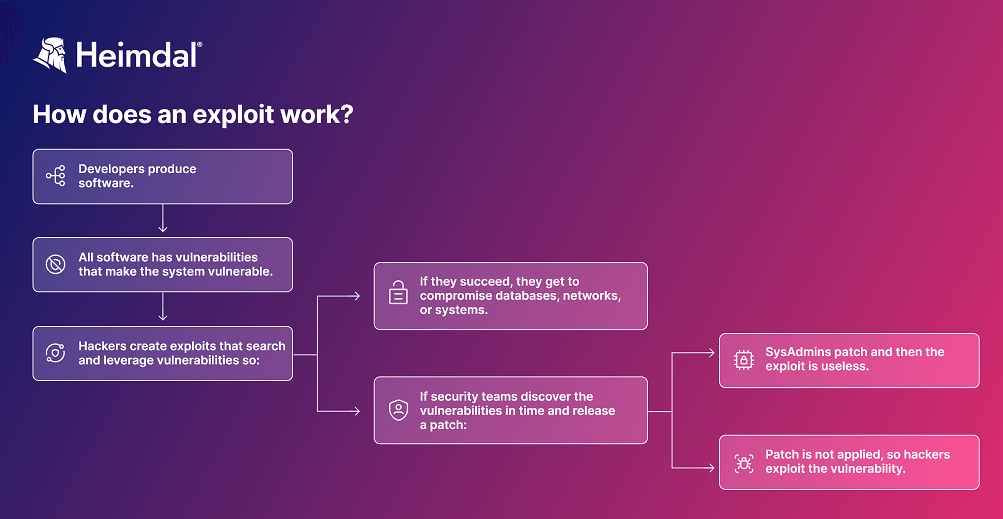
There is no such thing as flawless software. No matter how skilled the developer is, there still might be bugs in their application that might turn the system vulnerable to cyber threats.
Security specialists test software and scan for vulnerabilities so that developers become aware of them and create a patch to fix the problem.
Once the patch is released, all SysAdmins that use that software should apply the patch in the shortest time possible. While manually patching might be a reasonable thing to do in small businesses, for companies with over 100 employees the right solution is using an automated patch management tool. Using dedicated cyber security products is likely to patch more rapidly and also saves precious time for the IT team.
After the vulnerability is properly patched, the exploit becomes useless.
Zero-day Exploits vs Zero-day Vulnerabilities
There is a fair chance that threat actors find a vulnerability faster than the good guys from the research team. In this case, the hackers will create an exploit, a way of leveraging the found vulnerability to serve their goals.
If they succeed, they can start a zero-day attack on the systems that use the vulnerable application. This means they`ll be able to do some serious damage until being discovered. Zero-day attacks can impact more than one endpoint. A zero-day exploit can compromise a whole network and they are the starting point of many ransomware and DDoS attacks.
Although they are sometimes interchanged, the two terms are different. A zero-day vulnerability is a weakness known to threat actors, but unknown to the developer.
It can affect software, a network, or a whole system. The zero-day exploit is the method, the tool that hackers use in order to take advantage of the vulnerability.
Classification and Types of Exploits
Exploits are classified into different categories based on the type of vulnerability they address, the delivery method they use, or the means they use to compromise a system. Further, we will take a look at the most common ones.
Exploits that Target specific Vulnerabilities
- Buffer overflow – hackers take advantage of programs that are not properly validating input data. This allows them to overwrite adjacent memory and, in some cases, run malicious code.
- Injection attacks – this happens when the adversaries succeed in inserting malicious data or code into a system. SQL injection and code injection are two such attacks.
Delivery Method Categories
- Remote Exploits – this type refers to the fact that the exploit is run remotely, over a network.
- Local Exploits – in this case, in order to execute code, the threat actor needs to gain physical access to a targeted device.
Exploits That Can Deliver a Certain Payload
- Code Execution – these exploits are the ones that allow hackers to execute arbitrary code on a system.
- Data Theft – in this case, the exploit leads to gaining unauthorized access to sensitive data.
- Privilege Escalation – this kind of exploit creates unauthorized access to high levels of system privileges.
Platform or Software-Specific Categories
- Web Application – the exploit targets a flaw in a web application or website.
- Operating System – the hacker aims to leverage vulnerabilities in certain operating systems, like Windows, Mac OS, etc.
- Hardware – these exploits target vulnerabilities in the hardware of the devices the hacker aims to compromise.
EternalBlue – A Famous Exploit Example
EternalBlue is a famous and dangerous exploit. Hackers leveraged it to infect endpoints worldwide with the WannaCry ransomware worm. Microsoft dubbed it MS17-010. The exploit gave the US National Security Agency (NSA) backend access to Windows OS devices.
Before NSA decided to announce Microsoft of the vulnerability and exploit, hackers leaked it to the public.
So, the WannaCry ransomware used the EternalBlue exploit to spread on networks worldwide. WannaCry impacted a huge number of machines worldwide and even disrupted the activity of healthcare institutions and government agencies. After launch on May 12th, 2017, threat actors managed to infect 230,000 Windows OS devices in 24 hours.
Although Microsoft did release a patch after finding out about the flaw, not everyone succeeded in applying it in time. FedEx, Deutsche Bahn, and NHS were among those infected.
How to Prevent Exploits
Endpoint security best practices and tools can help prevent hackers from exploiting vulnerabilities in a company`s digital perimeter. Using them is like ensuring you lock all the doors and windows of a house against potential thieves. To protect your privacy, valuable objects, and overall house integrity, you might also use a series of additional protection measures. Point a video camera at the front door, set an alarm system, make a habit of double-checking if the door is locked before you go to sleep, etc. Now, let`s see how security admins can protect the company`s assets from a cyber thief that wants to take advantage of a software vulnerability:
Never miss a patch
Make sure all software, on all devices is up to date. Don`t leave this responsibility to the employees, as they will tend to postpone updates as long as possible, to focus on their daily tasks. Use an automated patch management solution to stay one step ahead of threat actors.
Strong passwords save the day
Enforce a strong password policy. Using complex passwords will discourage hackers from brute-force attacking your devices.
Use legitimate, trustworthy software
Train the employees to spot phishing emails and instruct them not to click on suspicious links, download random apps from random places, or download potentially harmful mail attachments.
Use a traffic filtering solution
In addition to the educational program regarding phishing, you should also create some kind of safety net. Even after taking part in a training, for various reasons, your colleagues still might be tricked into clicking on a malicious link. In this case, a DNS filtering engine can detect and block any malicious communication from and to a command-and-control server.
Encryption is the key
Use end-to-end encryption to safeguard data. If you do this, even if threat actors manage to eavesdrop on your communication using an insecure channel, they won`t be able to read your data.
Keep on guard about newly found exploits
Use exploit databases to keep up to date with newfound ways of exploiting a vulnerability. Check out what are the latest public exploits, and what software is vulnerable. Use this intelligence for penetration testing and find out in time if your system is at risk. One of the most popular free exploit databases is called just like that: Exploit Database. It centralizes exploits from both public and private sources, while also offering filters so you can easily find an exploit of a certain type, affecting a specific platform or port.

Heimdal® Patch & Asset Management Software
- Schedule updates at your convenience;
- See any software assets in inventory;
- Global deployment and LAN P2P;
- And much more than we can fit in here...
How to Stay Safe with the Heimdal Solution
Leaving an exposed vulnerability unpatched is like inviting threat actors to breach your system. Of course, there will always be zero days and other unpredictable events that could threaten your assets. However, according to Gartner, 99% of the vulnerabilities threat actors exploit are flaws that the security professionals know about. So, having a proper patch management policy in place that makes sure known vulnerabilities are patched in time, can prevent most of that type of attacks.
Heimdal®’s Patch & Asset Management solution offers full automation of the patching process, which saves a lot of time for security teams and ensures no endpoint is forgotten because of human errors. Additionally, its real-time patching feature helps to significantly reduce the risk of exploitation. Your system will never again be exposed to known vulnerabilities for an extended period of time.
The product also offers complete control over the patching process. This is an important feature, as every company has its custom software ecosystem, with specific challenges and needs. The high degree of customization the Heimdal solution presents enables your team to adjust the patching process to fit the requirements and software inventory.
You can use the Heimdal Patch & Asset Management solution to deploy and patch any Linux, Microsoft, or 3rd party software remotely, at your own schedule, with complete visibility and granular control.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









