Contents:
Several Endpoint Detection and Response (EDR) and Antivirus (AV) products showed high-severity security vulnerabilities.
These flaws can be used to weaponize the products and turn them into a data wiper that will delete your files and even make the computer unable to boot.
How Security Tools Turn Bad
This wiper runs with the permissions of an unprivileged user yet has the ability to wipe almost any file on a system, including system files, and make a computer completely unbootable. It does all that without implementing code that touches the target files, making it fully undetectable.
Endpoint Detection and Response (EDR) and Antivirus (AV) tools are created to continually scan an endpoint in order to find any suspicious files, and delete or quarantine them if such files are found. Using these zero-day vulnerabilities, the software can be tricked by specially crafted paths to delete legitimate files and folders, making a computer inoperable.
What allows this to happen is a junction point or a soft link: where one directory serves as a substitute for another on the machine.
Put differently, between the window the EDR software identifies a file as malicious and attempts to delete the file from the system, the attacker uses a junction to point the software towards a different path, like C:\ drive.
Creating the Wiper
Initially, the EDR solutions stopped access to a malicious file and the deleting process was aborted when the user erased the rogue file.
However, using Aikido, a wiper tool, a malicious file is placed under a fake directory without any access. This triggers the privileged deletion, leading the EDRs to postpone the deletion until the next reboot.
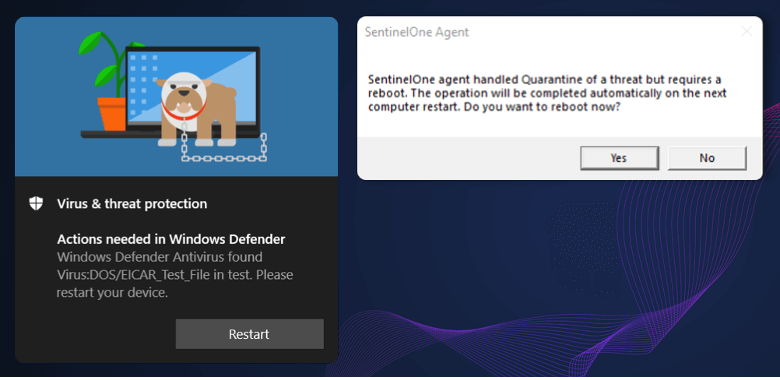
Taking advantage of this new attack interval, a threat actor can delete the rogue file’s directory, build a junction pointing to the target directory to be erased, and reboot the machine.
Successfully transforming EDR and AV solutions into data wipers can lead to the deletion of all the files from the admin directories, and of system files like drivers, making the operating incapable to boot.
The researchers tested 11 security products, and 6 of them were vulnerable to the zero-day wiper exploit.
We responsibly reported these vulnerabilities to the affected vendors between July and August of 2022. We then worked closely with them over the next four months on the creation of a fix prior to this publication. The following CVEs have been issued by three of the vendors:
Microsoft: CVE-2022-37971
TrendMicro: CVE-2022-45797
Avast & AVG: CVE-2022-4173
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









