Contents:
EDR (Endpoint Detection and Response) should be an essential part of any great cybersecurity strategy. Endpoint security is critical for any company since most of the successful breaches originate on the endpoints. Let’s have a look at how Microsoft EDR tools can help!
Microsoft EDR Tools
The most important Microsoft EDR tool is Microsoft 365 Defender, with its Microsoft Defender for Endpoint service. Let us have a closer look at them.
Microsoft 365 Defender
Because it combines detection, prevention, investigation, and response across endpoints, identities, email, and applications, Microsoft 365 Defender can help you both before and after a breach.
You can use it to figure out how a danger got into your environment, what was affected, and what the current impact is on the company.
Microsoft Defender for Office 365, Microsoft Defender for Identity, and Microsoft Cloud App Security are also part of the Microsoft 365 Defender suite. As they say, the set can assist you in preventing attacks, narrating the whole story of attacks, and automating response to compromise, and it can also “enable security teams to perform detailed and effective threat hunting across endpoint and Office data.”
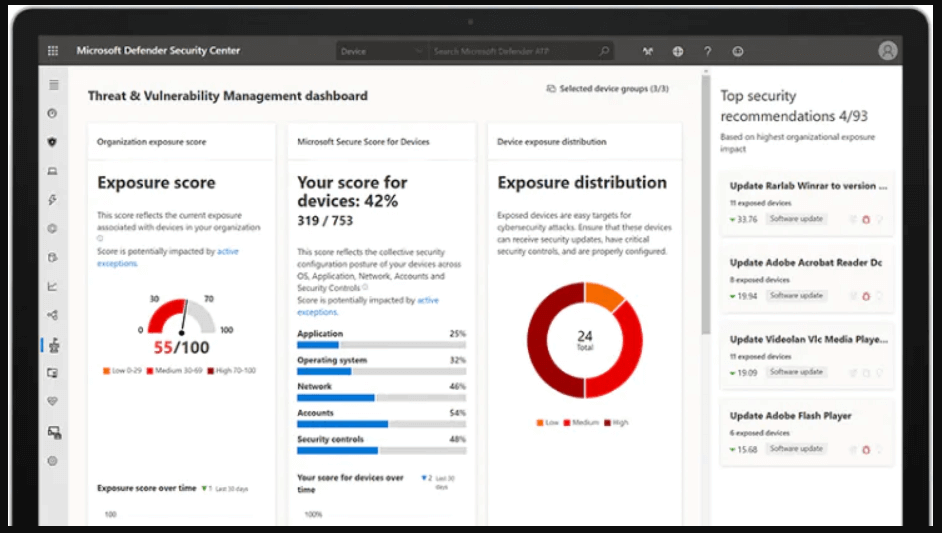
Microsoft Defender for Endpoint
Threat and vulnerability management, attack surface reduction, next-generation protection, endpoint detection and response, and auto investigation and remediation are all features of Microsoft Defender for Endpoint.
This Microsoft EDR solution can protect against both fileless and file-based threats, as well as emerging polymorphic and metamorphic malware. It can quickly move from alarm to remediation thanks to automation: after detecting vulnerabilities and misconfigurations in real-time, its algorithms determine whether a threat is active and what steps are required.
Our Recommendations
Although EDR is essential for the security of your endpoints, we recommend not forgetting about proactivity – more exactly, do not forget about EPP!
EPP stands for Endpoint Protection Platform and is represented by solutions that detect and block cybersecurity threats at the device level. It typically includes components like antivirus, anti-malware, data encryption, firewalls, intrusion prevention, data loss prevention.
In case you’re wondering if you need to choose between EDR and EPP, the answer is no. You shouldn’t choose between them, you should actually combine them:
Keeping malware off your endpoint devices is the best way to avoid threats in the first place. EPPs work to match any threats on your endpoints with known malware signatures to identify them and remove them from your device more quickly. Unfortunately, new malware pops up all the time and existing malware can be tweaked, so an EPP isn’t enough to protect your network on its own.
Once a threat has made its way onto your endpoint, you need to contain and remove it quickly to keep it from getting to your network. That’s where EDR comes in. While EPP is more of a passive tool, IT security teams actively use EDR to isolate the threat and start automated resolution plans. EDR also helps security teams with their threat investigation to determine which endpoints were affected and where the attack came from.
Our Endpoint Detection and Response software combines EPP with EDR to protect endpoints and continuously monitor and respond to mitigate cyber threats. The solution includes the Threat Prevention and Next-Gen Endpoint Antivirus modules, but also Patch and Asset Management, Privileged Access Management and Application Control, as well as Ransomware Encryption Protection. Together, they can help your IT team:
- spot processes, users, URLs and attacker origins used to infiltrate your network (Threat Prevention);
- track device-to-infrastructure communication to spot and stop attacks that firewalls cannot see, and spot hidden malware, completely autonomous of code and signatures (Threat Prevention)
- close vulnerabilities by patching Microsoft and 3rd party applications (Patch and Asset Management)
- monitor processes and process changes, and detect and identify even the most advanced threat with the help of 4 stages of scanning (Next-Gen Antivirus)
- remove permanent rights and give rights when needed, for the period that they’re necessary, rights that can be revoked any time, while all actions are logged for a full audit trail (Privileged Access Management).
- whitelist and block running applications, customize live sessions, log everything on the go, and prevent users from running malicious software (Application Control).
- protect devices against malicious encryption attempts initiated during ransomware attacks (Ransomware Encryption Protection).
Wrapping Up
Effective endpoint security is of paramount importance for any company that values its data, time, and money, and EPP and EDR protection are just a part of the equation – an essential one.
As businesses expand, so do the number of endpoints and the expense of security. The penalty of not safeguarding your network, on the other hand, can be much higher in terms of data loss, regulatory fines, and reputational harm.
However you choose to proceed, please remember that Heimdal™ Security always has your back and that our team is here to help you protect your company and your home.
Drop a line below if you have any comments, questions or suggestions regarding the topic of Microsoft EDR – we are all ears and can’t wait to hear your opinion!
P.S. If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











