Contents:
In a corporate context, an asset is part and parcel of a company’s financial worth. Assets hold economic value and future benefits, as they have the ability to generate cash flow. For this reason, IT asset management, or ITAM for short, is quintessential in today’s tech landscape.
Technology is indispensable for the contemporary enterprise, and therefore IT asset management is as well. But what is IT asset management? What does its implementation mean, and more importantly what does it look like? Let’s find out.
What Is IT Asset Management?
Before understanding what IT asset management can do for your organization, you need to first understand what ITAM is. The International Association of Information Technology Asset Managers (IAITAM) defines IT asset management as:
a set of business practices that incorporates IT assets across the business units within the organization. It joins the financial, inventory, contractual and risk management responsibilities to manage the overall life cycle of these assets including tactical and strategic decision making.
IT assets are important because they help to maintain the CIA triad. CIA comes from confidentiality, integrity and availability: “At the core of information security is information assurance, the act of maintaining the confidentiality, integrity and availability (CIA) of information, ensuring that information is not compromised in any way when critical issues arise. These issues include but are not limited to natural disasters, computer/server malfunction, and physical theft.”
IT asset management is an essential security practice for the modern workplace. The standard office environment nowadays is heavily reliant on technology, primarily in the form of laptops or desktop computers with various iterations of software running on them. Add smart devices such as mobile phones and tablets to the list, then consider IoT devices such as servers or printers. These are the components that fuel your enterprise.
Your company’s network IT asset management department is there to ensure that the technology the business operates on is not taken for granted, but administrated correctly. Also known as IT inventory management, ITAM involves keeping a detailed record of the software and hardware of an enterprise. This list is then used to make decisions about existing assets, as well as future purchases.
Types of IT Asset Management
IT asset management deals with five subtypes of IT assets, as explained below:
- Hardware, in the form of desktop computers, laptops, keyboards, printers, Wi-Fi routers, and any other physical devices used in a company’s IT infrastructure. This type of IT asset is relatively easy to catalog and keep track of.
- Software, which is represented by all the files and applications that are executed within a corporate network to fulfill work-related purposes. It is perhaps the most confusing and hard to define area of IT asset management, due to licensing requirements and compliance issues, among other matters.
- Digital, a subtype of IT asset consisting of videos, photos, and other forms of digital data such as scanned documents. While these are relatively simple to record, they are highly sought after by malicious actors due to the high confidential information potential that they hold.
- Mobile, which is another complicated area to handle. With mobile devices becoming increasingly popular in the contemporary office, the risks of them becoming a hub for malicious shadow IT are higher as well.
- Cloud, the most elusive type of IT asset out there. But despite its intangible nature, cloud IT asset management can replace the need for hardware components or licenses, thus making the task of your network admins more straightforward.
IT Asset Management Processes
A particularly important aspect of an IT asset management process is IT asset discovery – the operation of cataloging the IT assets that are used by a certain company and also the process of monitoring them on a daily basis.
Usually, IT asset discovery is done through an application that is installed on a laptop or a company-wide server, which will regularly scan for updated hardware and software information. This will guarantee that the devices are up-to-date and that will lead to fewer anomalies or vulnerabilities in the assets or network.
How Can IT Asset Discovery Help?
IT Asset Discovery automates the process of cataloging all your IT assets
Once installed, an IT asset discovery application communicates with the network’s devices in order to gather hardware and software-related information, which can then be used by the IT support team. Redundant software will be periodically flagged and removed, as well as the assets of previous employees who had privileged access to your network.
IT Asset Discovery allows you to make data-driven decisions
With an IT asset discovery tool, you will not rely only on your memory anymore to know what assets can be found in your company and where they are exactly. An IT asset discovery solution will offer you the visibility necessary for making informed decisions for your organization.
IT Asset Discovery helps you avoid unnecessary technology purchases
By scanning in your assets you will know exactly how many devices you have in use, how many are available and how many need to be replaced and budgeted for.
IT Asset Discovery helps you achieve software license compliance
Another great advantage of an IT asset discovery solution is the fact that it provides you with the ability to manage software licenses from one place and to keep track of all registered / unregistered software that may be used in your company.
Using unlicensed software on computers can bring penalties of hundreds or even thousands of dollars if an audit finds that your organization is non-compliant – this is not something to be put at the back of your mind.
IT Asset Discovery allows better reporting and analysis
As you can probably tell, the data provided by an IT asset discovery tool can also be very useful when there is an audit or when you’re thinking about making an update to your IT infrastructure.
How Can You Make Sure that You Enjoy the Benefits of IT Asset Discovery?
By identifying the assets that will be discovered and the right tools
You should keep it simple and start with laptops, desktops and software and let the solution evolve in time. Gartner recommends: “[…] IT asset managers should proactively work within the IT strategic planning process to identify what will be acquired, why it will be used, its anticipated useful life, and how it will be secured, monitored and maintained”.
By defining a discovery process
You should have an inventory management database to keep track of the purchased assets and their lifecycle changes. You should also document the IT assets acquired outside of the normal procurement process.
By normalizing the data
Accuracy is important for IT asset discovery. Inconsistent naming can hinder building IT reports – for example, a Microsoft application can report its vendor as MS, Microsoft or Microsoft Inc. Make sure you get consistency by implementing asset normalization processes.
IT Asset Lifecycle Management
When it comes to creating an efficient IT asset lifecycle management process, you should have in mind three principles:
A clear management strategy
The executive level and the IT department should be sharing a common vision. To make sure they’re on the same page, you should discuss business requirements in such a manner that all teams can fully understand. In the end, the main goal is to reach an agreement regarding your business objectives and strategy implementation.
It should be a strategic plea to how business is conducted, how decisions and processes are made and used, and you pass on this information. Developing a strategic IT asset management plan will help your organization provide services more efficiently and get the highest amount of worth from its assets.
At the same time, creating a strategic IT asset management plan will allow you to understand how and how much of your assets are being used. With this information, you can define the lifecycle value of an asset and plan it accordingly. What’s more, unnecessary assets can be disposed of, and you can generate extra funding from their sale.
Defining organizational design
For your plan to succeed, each role and responsibility in your organization should be clearly defined. Qualified resources must be available to achieve the ITAM objectives.
As soon as you’ve figured out the people and processes, you should:
- Collect assets information
- Decide what assets to focus on
- Develop a strategy for every asset
A long-term asset plan
ITAM planning should go a good way off from short-term thinking. With long-term asset management, on the other hand, you’ll be capable of predicting infrastructure investments, a crucial move for a business’ product quality and performance reliability. To be able to decide how to invest limited capital you first need to understand both the current and future condition and capacity of your company’s infrastructure. Finally, you need to understand the associated costs and risks of implementing or postponing system improvements or developments.
Stages of IT Asset Lifecycle Management
As soon as you establish these principles and have figured out which assets you need to prioritize, you can begin developing your ITALM plan. This will allow you to benefit from their value and avoid potential risks for your organization.
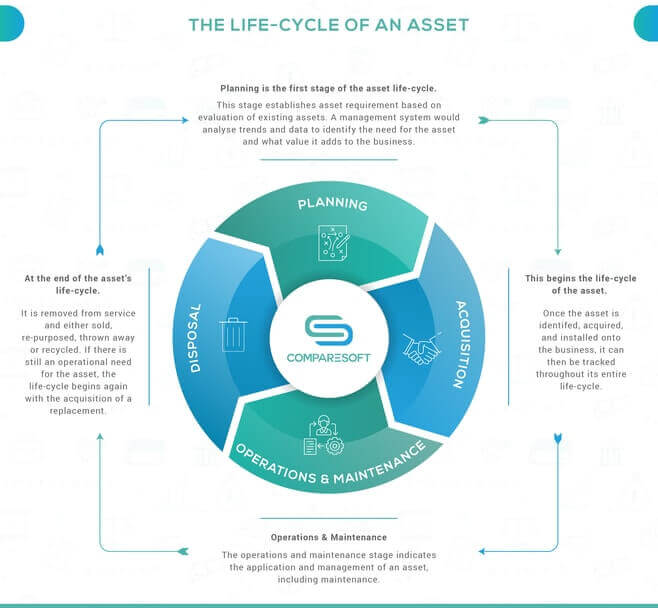
According to ITAM experts, a basic strategic IT asset lifecycle management plan should include four stages:
Planning
Before procuring an asset, it first needs to be identified in this initial stage, planning. You need to make a business case by pointing out what it will be used for, its estimated costs, etc. Next, the asset is evaluated based on your necessary criteria.
Acquisition
The second stage of ITALM is the acquisition or procurement of the asset and the associated activities. Before purchasing it, various options need to be researched, pricing compared, trials, or demos tried. Afterward, the asset is installed, built, and delivered.
Operation and Maintenance
At this moment, the asset is being put to use, providing the purposed service to your organization. Proper maintenance and upgrades should be provided regularly across its lifecycle so that you’ll be allowed to make the most of your investment and benefit a long time from your asset.
Disposal or Replacement
As you can imagine, this final stage of the IT asset lifecycle takes place when the asset is no longer profitable for the business, the costs for operational/maintenance become sky-high, or the asset is at the end of its operative and efficient life. Therefore, the asset should be deactivated and disposed of properly, or replaced with a new one, focusing on financial and environmental sustainability, and, above all, security.
How to Implement IT Asset Management
Create a Comprehensive Inventory Record
The first step in integrating IT asset management for your company consists of creating a comprehensive inventory record. This should contain both hardware and software IT assets, as well as digital, mobile, and cloud components.
To make sure you don’t miss out on anything, I recommend first of all performing a Windows domain scan. That needs to be followed by a network scan to detect routers, switches, printers, VMHost machines, and other adjacent components. If your company does not operate on Windows, the latter will suffice.
Closely Monitor the Life Cycle of Your IT Assets
Technology does not live forever. Sooner or later, your IT assets become outdated and require patching, or they reach their end of life. Closely monitoring your inventory for this is thus essential for the cybersecurity of your company. Obsolete applications create vulnerabilities that malicious actors can easily exploit. Fortunately, Heimdal™ Security can help you mitigate this risk.
Heimdal™ Patch & Asset Management is an automatic software updater that keeps an archive of the applications running on your endpoints, installing updates based on preconfigured policies as soon as they are deployed by developers. Patches are deployed to the devices in your corporate network as soon as third-party vendors release them into the wild, so you won’t have to worry about improper IT asset management.
Keep Meticulous Track of Software Licenses
Software licenses are another aspect you should keep track of meticulously. Also known as a certificate, it is a contract that you, the buyer, close with an application’s developer, or the seller. Essential concepts such as installation rights, warranties, and liabilities are stipulated within it. Its purpose is to protect the intellectual property of the vendor, as well as to assure you of its authenticity and functionality.
Handling software licenses should thus be a priority for your IT asset management strategy. As mentioned in the previous section, nothing is worse than an outdated application…maybe only an inoperative one. You should always be aware of when certificates reach their expiration date and either renew or cancel them accordingly.
Integrate ITAM with the Larger Infrastructure
IT asset management is just one piece of the cybersecurity puzzle. For this strategy to succeed in the ways that you desire it to, it must be integrated into your enterprise’s larger information technology infrastructure. This is where the concept of the Information Technology Infrastructure Library (ITIL) comes into play.
ITIL refers to a set of practices that align a company’s IT services with its business needs. It creates a baseline upon which organizations can plan, implement, and measure their procedures, which is highly relevant for ITAM.
Continuously Audit and Improve Your Practices
Finally, you must consider that IT asset management is not a one-and-done type of deal. It is a continuous process that involves auditing and improving practices whenever necessary. In a constantly changing digital landscape, your company must stay up to date to survive. For this reason, my suggestion is to perform regular network inspections and adapt their findings to your strategy.
What about IT Asset Management Tools?
According to ITAM experts, there are three types of tools that are essential for successful asset management:
Discovery tools
These tools are meant to provide visibility into your assets. These tools crawl your IT environment and pick up many or most of your assets. Newer versions of ITAM discovery tools are cloud-native, and some even offer dependency mapping across hardware, software, and multi-cloud.
ITAM database
Your organization may have an independent ITAM database, or it may correspond with your Configuration Management Database (CMDB) or CMS tools. If you find yourself in the first scenario, make sure you establish a process and policy for sharing out this data.
Automation and orchestration
Tools that are backed up by strong automation can provide ITAM managers with all the necessary data to answer the WHATs, WHENs, and HOWs of hardware and software management.
How to Choose the Right ITAM Software
Implementing a new approach to asset management will help your organization further clarify which software will best support your needs.
Conducting an asset inventory is the first step in getting a better understanding of what you have and, of course, your costs. After getting this information, it’s possible to map asset lifecycles and allow your financial department to evaluate costs.
Advanced IT asset management goes ahead of this stage and automates everyday ITAM tasks. For example, employees can request a license to a common software subscription using a self-service portal. That particular request can be approved with a link sent to provide access to the subscription for the ones who demand it. This automation process allows IT teams to focus on more important work, than expending effort on support tasks.
Another important aspect of efficient asset management is collaboration. Rather than purchasing assets “in the shadows”, making requests through a collaborative tool would be easier for employees, especially for procurement teams who will be able to monitor and approve acquisitions. Additionally, connecting your asset management tool to other services such as communication platforms will make it even better. Employees would be able to make requests in a few taps on their keyboard, thus improving the intake process for asset requirements.
Benefits of Using ITAM Software
What are the benefits that IT asset management can bring to your company? It should be pretty clear by now:
Visibility
By using IT asset management best practices, you will have an in-depth view of your IT environment. You will know exactly what systems and software your company uses, where components reside and how they are used, their current lifecycle phase, how they impact the business services.
Compliance
IT asset management best practices help you stay compliant, prepare for audits and reduce legal security risks. You will be able to monitor the hardware and software components of your network computers and check if unapproved or dangerous software or hardware is installed.
Costs optimization
IT asset management will help you optimize asset usage and control IT asset purchases. The data it provides will be particularly useful for storage utilization analysis and budget planning, allowing you to maximize existing asset utilization and eliminate unnecessary expenditure.
ITIL support
ITIL comes from Information Technology Infrastructure Library and represents:
a set of detailed practices for IT service management (ITSM) that focuses on aligning IT services with the needs of the business. ITIL describes processes, procedures, tasks, and checklists which are neither organization-specific nor technology-specific but can be applied by an organization toward strategy, delivering value, and maintaining a minimum level of competency. It allows the organization to establish a baseline from which it can plan, implement, and measure. It is used to demonstrate compliance and to measure improvement.
IT asset management supports it by providing accurate information about assets, by identifying the impact of incidents and by undertaking a root cause analysis.
IT Asset Management Best Practises
Define an IT Asset Lifecycle
The first step of IT asset management should be the making of an inventory management process that documents each IT asset’s lifecycle status. Your IT administrators should know if an asset is in use, in storage, checked out, available or retired.
Decide whether IT Assets Should Be Managed or Unmanaged
According to the risks that are associated with them, IT assets should be classified as managed or unmanaged. The first category should include laptops, desktop, mobile devices, servers. These ones should be checked-in on a daily basis. The unmanaged category should include IT assets that do not contain sensitive data – hubs, monitors, printers.
Compose an Asset Mapping Strategy
Your inventory data should include relevant information like owners, contracts, departments, projects, locations, compliance details. This information will make IT asset reports more relevant, offering real insights into security risks and IT asset operational costs.
Automate IT Asset Management Processes
An automated IT asset management process means increased productivity and reduced risk of human error. You should consider replacing human technicians with automation tools for repetitive, redundant tasks.
Speaking of automation, you can even try our very own Heimdal™ Patch & Asset Management, which allows you to deploy software, close vulnerabilities, achieve compliance and see all software assets, thus mitigating breaches, data leaks, environment compromise, exploits, and compliance fines.
Heimdal® Patch & Asset Management Software
The solution is fully customizable but works as a set-and-forget for hyper automated deployment of software and updates, and offers a full audit trail for increased compliance.
Keep Track of the Process
Last but not least, you should remember that IT asset management is an ongoing process. For improved (cyber)security, you should keep setting up processes and be consistent in implementing them.
ISO Standards for ITAM
The International Organization for Standardization (ISO) established a family of standards for ITAM known as ISO 19770. It consists of six parts that were updated as recently as 2017. I have provided a one-line summary, as well as the appropriate links for each one below as comprised by the ITAM Standards Committee:
- ISO/IEC 19770-1, which outlines the best ITAM practices in an organization.
- ISO/IEC 19770-2, which handles software identification tags.
- ISO/IEC 19770-3, which details the rights on a piece of software.
- ISO/IEC 19770-4, which measures resource utilization reporting.
- ISO/IEC 19770-5, which provides an overview of ITAM standards and terms as defined by ISO.
- ISO/IEC 19770-8, which touches upon document mapping guidelines.
I recommend checking out the individual documents linked above for more information on IT asset management standards for your enterprise.
Final Thoughts on IT Asset Management
IT asset management deals with multiple facets of a company’s inventory. With hardware and software at its foundation, its success or lack thereof can make or break an organization in the long run. For this reason, my recommendation is to not take your resources for granted. With the proper strategy and corresponding tools on your side, your business will thrive.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











