Contents:
ITSM is a strategic approach to IT management, focusing on delivering value to customers, addressing customer needs, and IT services for customers. ITSM defines the roles and responsibilities of every individual and department with regard to IT services. It allows for increased productivity, lower costs, and improved end-user satisfaction.
ITSM is more inclusive than traditional IT support. It describes the processes and tools IT departments use to manage IT services and covers all information technologies inside an organization. In short, ITSM aligns the IT team’s goals with the broader objectives of the business.
Understanding ITSM Processes
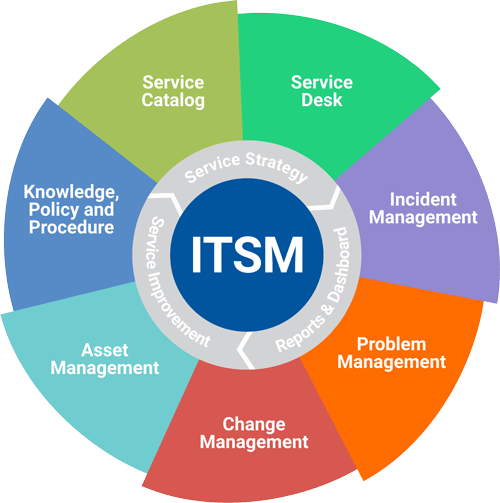
While technology may be an important part of IT processes, it should not necessarily be the main focus. ITSM on the other hand, is more comprehensive, as it includes both business and traditional IT objectives. As a consequence, ITSM improves abilities across the board in the following ways:
#1. Incident Management
To restore service to customers as quickly as possible, ITSM incident-management handles the whole incident-management process. Its ability to prioritize incidents and service requests according to business impact allows staff to focus their efforts where they can be most effective.
#2. Problem Management
Problem-management processes remove IT infrastructure flaws, eliminate recurring issues, and stabilize the environment. This way, incidents are prevented before they can cause any damage.
#3. Change and Release Management
Change management guarantees that standard processes are followed when handling all changes to IT infrastructure (deploying new services, managing hardware, resolving code issues). Change implementation is quicker and more consistent, and risks and errors are minimized.
#4. Service-Level Management
Service request management is a procedure for managing different customer and vendor service requests so management can identify weaknesses and take corrective action. It enables customers to automate certain tasks and recurring requests.
#5. Request Management
Request management makes sure important requests are always moving forward, including requests to reset passwords, install new workstations, update personal data, or access information.
#6. Configuration Management
Configuration management helps track all configuration items in your IT system. It identifies, evaluates, and maintains critical configuration information for hardware, software, staff, and documentation, providing the IT department with a reliable repository for IT component information.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Benefits of Using ITSM Software
IT teams follow ITSM processes to handle end-to-end delivery of services including designing, creating, and delivering IT solutions. Applying service management principles will give your team an advantage, which will further enhance the entire organization.
Using ITSM software can turn your organization into an efficient and productive business. With a structured ITSM strategy, you can align your IT with your business goals and streamline the delivery of services based on budgets, resources, and results. What’s more, it will reduce costs and minimize risks, thus improving the customer experience. Below you will find some of the benefits of ITSM:
#1. It Allows Cross-Department Collaboration
Using a streamlined project management approach will encourage IT and development teams to work together flawlessly. In addition, it allows employees to share their knowledge across the organization and seek constant improvement.
#2. It Increases Control and Governance.
Using ITSM to set up internal controls will empower you to generate insights regarding your employees’ actions and asset usage.
#3. It Delivers and Maximizes Asset Efficiency.
When automating business processes, resources are maximized. This improves the coordination of requests to deliver a more efficient service. You do not have to worry about losing track of requests or have to deal with service delays due to the lack of skill of individuals.
#4. It Provides Better Customer Support
ITSM ensures the facilitation of a positive customer experience with self-service applications and better processes.
#5. It Calls for Quick Action
ITSM software provides a fast response to major IT issues and prevents future incidents from happening.
#6. It Decreases Costs and Leads to Better Service
Since ITSM already provides advanced IT solutions that will add value to your business, you won’t have to buy a lot of infrastructure and hire more people. Instead of investing more time and money in fixing technological issues, you can allow them to enhance your business functions adding to their overall growth.
Wrapping It Up…
To sum things up, I believe we can agree that ITSM software ensures that the appropriate mix of people, processes, and technology is in place to provide value to the organization. It helps you achieve a better understanding of what your business really needs and why.
Drop a line below if you have any comments, questions, or suggestions regarding the topic of ITSM software – we are all ears and can’t wait to hear your opinion!


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










