Contents:
As I sit here, typing away, I can’t help but imagine all the things that are going on “behind the scenes” on my laptop.
- The files in my Google Drive account are synced every time I make a change in one of them;
- My operating system (Win 10) downloads and installs updates in the background;
- My inboxes check for new emails every few seconds;
- The plugins in my browsers connect to the web to do all sort of things, from providing access to my passwords to taking screenshots;
- My apps get updated automatically and silently (thanks to Heimdal), etc., etc.
In spite of all this activity, my laptop is quite silent. It only starts to protest when I open 20-30 tabs in my browser and the cooling fan works overtime. In the rest of the time, it’s my trusty companion, who helps me get things done, learn, keep in touch with my friends and more. I actually care a lot about it. To me, it almost has a soul and I can’t bear the thought of something happening to it.
The invisible threat
The hustle and bustle in our devices are rarely visible to the naked eye. We only notice it when our browsers get stuck or, worse when we get a malware infection. It is then when we realize how many layers make it easy for us to do our jobs and enjoy our hobbies (or just waste time online). Most Internet users only interact with the graphical, easy to use part of tech (aka the front-end). So they rarely think about what goes on in the background. And that’s where cybercriminals thrive. Cyber attackers know how to manipulate the data that flows through your Internet connection to serve their malicious objectives. They can redirect your Internet traffic or infiltrate it to infect your PC with malware. The process is mostly automated and, frankly, 99% of Internet users wouldn’t be able to spot it with their naked eye. Heck, sometimes even antivirus can’t spot certain malware infections, such as ransomware! So understanding how your computer connects to the Internet is a key step to setting up a layer of proactive security for your data. No more waiting for something bad to happen so you can react to it. And I’ll tell you exactly how you can do it.
How your computer connects to the Internet
As humans, we’ve evolved to spot threats and protect ourselves and our loved ones from danger. It’s coded in our DNA. It’s part of our survival instinct. But we’ve only had a short, few years to train ourselves to detect online threats. And most of them aren’t even visible, as I’ve said before. So what can we do to become better at spotting and blocking cyber threats? Let’s start with listing a few things happening on your computer right now that are all using your Internet connection. First, you have all the ways in which your PC communicates with websites, servers, and apps using the Internet. This includes your cloud storage accounts, your email, your apps, your browsers, your software updates, your operating system and more. They all connect to the web to send and receive data and make sure that your PC runs smoothly and does what you want it to do. [Tweet “Ever thought about all the ways in which your PC connects to the web? Here they are:”] While pondering on this, I realized that I can’t even remember the last time I used my laptop offline. That’s one more reason to care about my next point. Second, you have your personal data that flows back and forth, to and from your computer. A quick, top-of-mind list would look like this:
Outgoing data:
- Credit card information
- Passwords
- Emails (work-related and personal)
- Personal documents (diplomas, IDs, contracts, etc.)
- Home address
- Phone number
- Google searches
- Browsing habits (collected through browser cookies)
- Information about your computer (the type of device, model, etc.)
- Location, etc.
Incoming data:
- Plane tickets
- Personal conversations via instant messaging apps
- Hotel bookings
- Confidential documents and contracts
- Bills
- Medical records, etc.
And it all looks something along these lines if we are to keep it really, really simple: 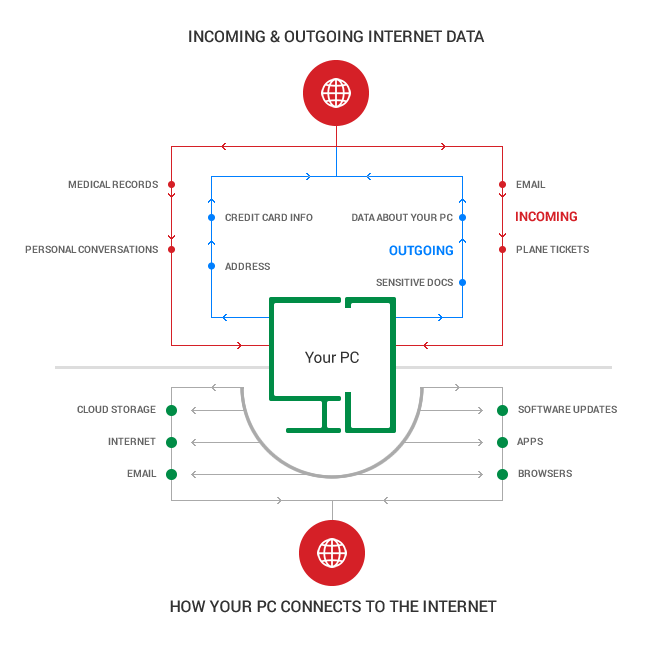 When a cyber attack hits your computer, cybercriminals will want to find a security hole in one of your apps so they can get to the good part: your data, either incoming or outgoing. And, as you’ve already inferred from the lists above, there is a lot about you that cybercriminals can learn and use. No one wants certain details made public or sold on the Dark Web.
When a cyber attack hits your computer, cybercriminals will want to find a security hole in one of your apps so they can get to the good part: your data, either incoming or outgoing. And, as you’ve already inferred from the lists above, there is a lot about you that cybercriminals can learn and use. No one wants certain details made public or sold on the Dark Web.
Your browser, the attackers’ favorite target
Let’s focus on one of the most used pieces of software on any computer (no, not Facebook): the browser. You may not know or realize this, but cybercriminals use browsers as their main way into your PC. Here’s how they do it:
- First, they infect websites that redirect you to malicious domains hosting exploit kits such as Angler;
- Next, they use those exploit kits to scan your browser for vulnerabilities (if it’s out of date and has a flaw they can exploit, if your plugins are outdated and can be compromised, etc.);
- Once they find a way in, they can gain administrator rights, which gives them the chance to both download and extract data from your PC.
Here’s an example of a ransomware infection chain, which can start with clicking a malicious link in an email or ending up on the wrong website (or being redirected to an infected website). 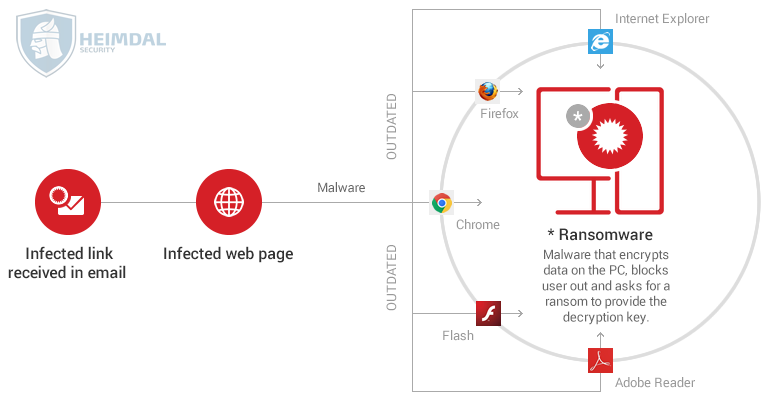 And browsers do have vulnerabilities, and don’t even get me started on browser plugins (oh, Flash, not you again!). Here’s a quick table that shows how many vulnerabilities the top 3 browsers had in 2015 and what the current situation is in terms of versions used by people all over the world:
And browsers do have vulnerabilities, and don’t even get me started on browser plugins (oh, Flash, not you again!). Here’s a quick table that shows how many vulnerabilities the top 3 browsers had in 2015 and what the current situation is in terms of versions used by people all over the world: 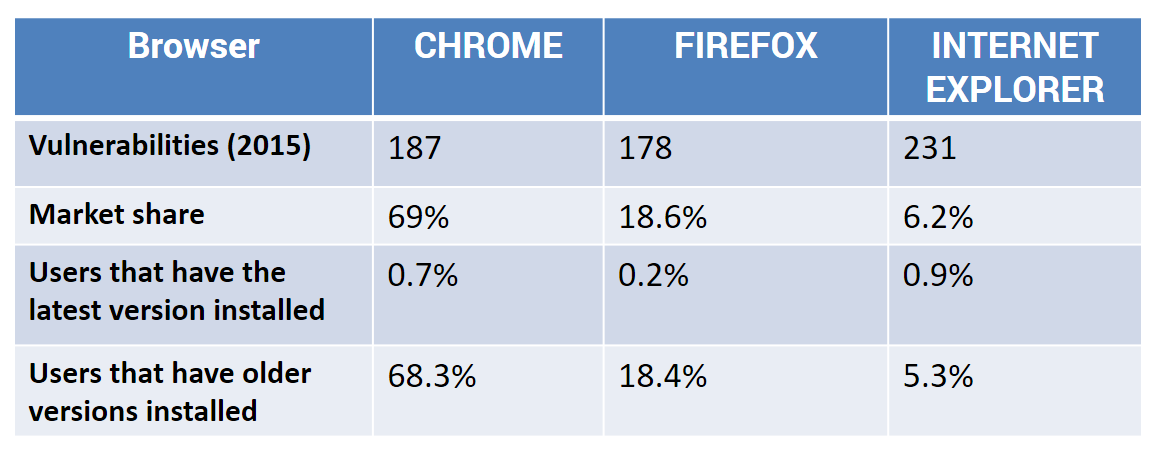 Sources: CVE Details and w3schools The problem here is that most users still run old versions of software, especially browsers, as you can see in the numbers above. These older versions are more insecure and most of their vulnerabilities are public. Which means that cybercriminals exploit them freely and constantly. Cisco’s Annual Security Report highlights the importance of browser security for both home users and companies:
Sources: CVE Details and w3schools The problem here is that most users still run old versions of software, especially browsers, as you can see in the numbers above. These older versions are more insecure and most of their vulnerabilities are public. Which means that cybercriminals exploit them freely and constantly. Cisco’s Annual Security Report highlights the importance of browser security for both home users and companies:
Because infected browsers are often considered a relatively minor threat, they can go undetected or unresolved for days or even longer—giving adversaries more time and opportunity to carry out their campaigns.
And there’s yet another threat to consider: malicious browser add-ons. So it’s not enough that you may be using an outdated browser or insecure plugins. You can also be plagued by insidious browser extensions that monitor your online behavior and send data about them (and your PC). The researchers behind Cisco’s Annual Security Report also emphasize this important aspect:
Malicious browser extensions can steal information, and they can be a major source of data leakage. Every time a user opens a new webpage with a compromised browser, malicious browser extensions collect data. They are exfiltrating more than the basic details about every internal or external webpage that the user visits. They are also gathering highly sensitive information embedded in the URL. This information can include user credentials, customer data, and details about an organization’s internal APIs and infrastructure. Multipurpose malicious browser extensions are delivered by software bundles or adware. They are designed to pull in revenue by exploiting users in a number of ways. In an infected browser, they can lead users to click on malvertising such as display ads or pop-ups. They can also distribute malware by enticing users to click a compromised link or to download an infected file encountered in malvertising. And they can hijack users’ browser requests and then inject malicious webpages into search engine results pages.
We’ve all had unwanted toolbars and add-ons installed, which later brought our browser to a halt or triggered strange pop-ups. But that’s a slippery slope towards a much more dangerous malware infection, aimed at your money and confidential data. It can be financial malware, such as Dridex, or unbreakable ransomware, such as TeslaCrypt 4.0. So now that you know the problem, it’s time to figure out the solution.
Tools to help you filter your Internet traffic and improve your online security
“Enjoy the web responsibly and safely” would be my advice for anyone going online for the first time. But it’s also true for anyone who’s already using it. So let me share a list of 6 tools that can help you filter your Internet traffic and eliminate some of the threats you can’t block by yourself.
Use a VPN
A VPN is a Virtual Private Network, used to anonymize Internet traffic and secure it through encrypted connections and communication. Basically, a VPN created a virtual point-to-point connection by employing dedicated connections, virtual tunneling protocols, and traffic encryption. By using a VPN, you can greatly reduce your exposure to attacks looking to “sniff” and exfiltrate the confidential data you send and receive over the Internet.
Set up a proxy
A proxy is a dedicated computer or software that runs on a computer that acts as a middleman between your computer and your Internet connectivity requests. Here’s how it works:
- You type CNN.com in your browser;
- The request goes to the proxy, which verifies it (you can upload blacklists of infected websites that the proxy can use to verify if the website is safe or not);
- If the website which you want to visit is safe, the proxy will show it to you;
- If the website you want to access is malicious, it’ll be blocked.
Some backlists (both free and paid) you can use to set up your proxy are: http://urlblacklist.com/?sec=download http://www.squidguard.org/blacklists.html http://www.squidblacklist.org/
Turn your firewall on
The Wikipedia definition of a firewall is quite simple and easy to understand:
In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules.
Another way to understand firewalls is provided by Leo Noteboom:
Firewalls block what’s coming into your machine unannounced or un-requested.
Windows has its own firewall you can use for free and we encourage you to keep it on. Some antivirus products include a firewall in their suite, next to their antivirus engine. This may disable Windows Firewall, so make sure to check your settings to ensure that you’re using a firewall from a trusted source. [Tweet “I found this list of tools to filter Internet traffic & block threats to be very useful:”]
Install a reliable antivirus
While antivirus products are highly focused on reactive security, you can still rely on good AV to help you with filtering your web traffic. The best antivirus products often include blacklists of infected domains and websites. This is useful, because your AV may block these websites and domains that are known to be infected, keeping a malware infection at bay. However, keep in mind that cybercriminals move extremely fast. They can create thousands of infected domains that are only online for a few hours and then taken down so they can stay below the radar and continue their illegal activities. So these lists employed by antivirus products, while useful, are not enough to ensure your proactive protection. If you’re looking for a guide to choose a reliable antivirus, I have just the thing for you.
Try Heimdal™ Threat Prevention
There’s also another way you can filter your Internet traffic that’s focused on proactive cyber security. Because we believe that you shouldn’t wait for something bad to happen to improve your online safety. This is our specialty, so let me share how we do it. We built Heimdal™ Threat Prevention to focus on constantly changing threats. So behind it, there’s a massive amount of intelligence about cybercriminal infrastructure:
- The servers they use;
- The domains they generate;
- The websites they use to spread malware.
This infrastructure is costly to build and maintain and it’s their best asset that helps them grow their reach. So attackers do their best to grow it and keep it away from law enforcement and cyber security companies. What we do is gather this data about malicious web locations and filter your every web request through it (it = our secure DNS – Domain Name System). If the website you’re asking for or something on it (such as a banner) connects to malicious servers/domains/websites, we’ll block it. Heimdal™ Threat Prevention can detect and stop cyberattacks in various stages, to keep your data safe from harm:
- It will block incoming data transfers that carry malware or exploit kits;
- It will stop the payload or encryption key from reaching your PC by blocking communication between your PC and cybercriminal infrastructure;
- It will protect your data (credit card info, PC info, email addresses, etc.) from being harvested and sent to the servers controlled by the attackers.
It may sound simple, but there’s a lot happening in the background. And our intelligence database just grows by the day, as cybercriminals move to close some domains/servers and put up others. You should really check out our Heimdal™ Threat Prevention page for more specific details. You may be surprised you’ve been missing such an important element of your cyber protection.
Encrypt your data
While data encryption doesn’t fit into this category about traffic filtering, it’s become crucial. As we wrote in our guide on data encryption:
Encryption is a process that transforms accessible data or information into an unintelligible code that cannot be read or understood by normal means.
So, if your data is encrypted, cybercriminals can go ahead and steal it, because it will be unusable. That’s not to say that data encryption is a fix for all your security worries. Not in the least. But it can be a great asset! We highly recommend you encrypt your most sensitive data, especially before doing a backup (either in the cloud or on an external drive). The guide I mentioned before may come in quite handy.
Conclusion
Traffic filtering may sound like an exotic term destined for cybersecurity specialists, but I hope I managed to make it a bit simpler today. My goal is to help cyber security climb a bit higher in your list of competing priorities. Not because I work in this field, but because I truly believe that each of us needs it more than we realize. Until we evolve to fully adapt to how the Internet is changing our lives, we’ll need some good security solutions to rely on. And even when we get there, I still believe that security software will make our lives (at least) a bit safer, because technology will never stop evolving. And neither should we.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










