Contents:
The focus in this article will be on the challenges faced by midsize companies, defined here as organizations with 100-1000 employees, and how adopting a Zero Trust approach might help solve those problems.
Why medium-sized businesses? Because mid-sized businesses are equally likely as large organizations to be impacted by a data breach or other security incident.
Threat actors will indeed target any type of business, no matter how large or small, if they believe they can make money off and get away with it.
Whereas larger organizations typically have the necessary security teams, in-house knowledge, and skills, or expensive and sophisticated security equipment needed to protect themselves against cyberattacks, the same isn’t always the case for smaller companies. As a result, mid-sized businesses remain vulnerable and unable to properly defend the organization.
A Forbes research from 2022 shows that small and medium-sized businesses (SMBs) are “three times more likely to be targeted by cybercriminals than larger companies.”
Another factor contributing to the rise in cyberattacks against medium-sized companies is that these frequently do not see themselves as prospective targets, so they don’t even consider taking the appropriate security measures. It’s true that most people think cybercriminals prefer targeting systems of large corporations in order to gain more in a single strike. The reality, though, is different.
Also, the cybersecurity industry frequently overlooks mid-market businesses in favor of enterprises for whom they develop expensive and complex solutions.
As medium-sized businesses have some of the same data, customer information, and digital infrastructure that attract intruders to larger corporations, attacks against them are very prevalent. For instance, most small and medium-sized companies keep a considerable amount of customer personal and payment details, so if a threat actor manages to get into their system, they may take advantage of the significant payload and either use it for themselves or sell it to other cybercriminals.
In many cases, attackers employ some of the same techniques they use to target enterprises, such as:
- supply chain attacks,
- sophisticated social engineering attacks,
- advanced persistent threats (APTs).
This is mainly due to the fact that rather than employing different tactics for different types of organizations, threat actors may launch the same attack on multiple businesses by simply copying and pasting malicious code.
As mid-sized businesses usually lack advanced technology (because it might be too costly or they don’t know what their problems are or what security solutions to look for), these smaller organizations often find themselves overwhelmed by a barrage of sophisticated cyberattacks they are unable to avoid or stop.
Zero Trust for Mid-Sized Companies
The idea that large enterprises are the only businesses that need to be concerned about security is a myth. As highlighted in the introduction, cybercrime trends follow similar patterns in small and large businesses alike.
The thing is that smaller businesses probably have the most to lose when impacted by a damaging cyberattack. According to Expert Insights, organizations with less than 500 employees lose, on average, $2.5 million per attack. For mid-sized organizations, losing this much money in a data breach is disastrous.
Moreover, being the victim of a cyberattack significantly damages a company’s reputation which also has long-term impacts on revenue and brand equity.
2020 saw a dramatic increase in cybercrime as cybercriminals seized on newly created and vulnerable remote environments. Today, malicious actors are still exploiting gaps in organizations’ remote and hybrid infrastructure, and cybercrime is on the rise.
As threat actors increasingly target medium-sized businesses, Zero Trust technology can provide the most effective cybercrime defense and a continuous security foundation for long-term remote and hybrid work.
A common misconception is that Zero Trust is only for enterprises. While it’s true that enterprises prioritize the protection of their networks and information by implementing the newest technologies and approaches, mid-sized businesses need Zero Trust security implemented as well.
10 Reasons Mid-sized Businesses Need Zero Trust Security
The absence of a Zero Trust architecture can lead to numerous challenges for mid-sized businesses in the cybersecurity landscape:

1. Increased Vulnerability to Attacks
Without Zero Trust, mid-sized businesses frequently depend on traditional perimeter-based security models. These systems are becoming increasingly ineffective, exposing the network to external threats like phishing attempts and ransomware attacks.
2. Insider Threats
In the absence of a Zero Trust model, employees sometimes have more access to the network than they need to perform their tasks. This increased access level opens the door to potential insider threats, both intended and unintended.
3. Inadequate Access Control
Traditional security models typically don’t provide granular control over who has access to what within the network. Without Zero Trust, it’s harder to implement the Principle of Least Privilege (PoLP), leading to potential security gaps.
4. Compliance Risks
Lacking a Zero Trust model could put a mid-sized business at odds with rigorous data protection standards such as GDPR, CCPA, or HIPAA. Being non-compliant could result in significant fines and reputational harm.
5. Resource Drain
Older security models often require more maintenance and manual oversight, which can be resource-intensive. This can be particularly challenging for mid-sized businesses that may not have extensive IT departments.
6. Slow Response to Threats
Traditional security models may be unable to provide real-time monitoring and analytics. Without the quick verification methods inherent in Zero Trust, identifying and neutralizing a threat could take longer. This delay increases the potential for damage.
7. Inefficiency in Remote Work
As remote work grew more common, maintaining secure access to corporate assets became more difficult. A lack of Zero Trust makes it difficult to securely extend the organizational environment to remote locations.
8. Difficulty in Partner Collaboration
Mid-sized businesses often need to collaborate securely with multiple partners. The absence of Zero Trust can make secure data sharing and role-based access a laborious and risky operation.
9. Data Leakage
Without a Zero Trust architecture to monitor and manage data flows meticulously, the likelihood of sensitive information leaking outside the organization is increased.
10. Reactive Instead of Proactive
Lastly, without Zero Trust, security procedures are often reactive rather than proactive. This means that instead of preventing breaches, the focus turns to minimizing damage after a breach has taken place, which can be far more expensive and damaging.
The Road to Zero Trust for Mid-Sized Businesses
The first thing medium-sized organizations must do is to embrace an anomaly detection mindset: presuming everything is malicious behavior. This is part of the psychological adoption of security that comes as a challenge with a Zero Trust approach.
They also need to understand that implementing Zero Trust does not imply a lack of trust in their employees; rather, it relieves them of the responsibility of keeping data secure. In order to get the buy-in of the staff, it’s critical to communicate this accordingly and to do so while leading with empathy. Mid-sized businesses that adopt a Zero Trust security model will enable their employees to work remotely and safely, reducing the risk of cyberattacks.
Now more than ever, it’s imperative for companies of this size to safeguard their systems. Implementing Zero Trust is a proactive approach that can effectively futureproof these systems, ensuring robust security measures are in place.
There is a lot for these organizations to consider when developing a Zero Trust security model. The process of building and implementing it on their own can be overwhelming, which is why managed service providers (MPSs) are actively collaborating with midsize businesses to facilitate their adoption of a Zero Trust security approach and enhance their operational security.
Organizations of all sizes, not only medium-sized ones, need to keep in mind that Zero Trust security is more than just a singular tool, technology, or product. Rather, it’s a security strategy that involves employing a combination of tools to implement specific methods intended to reduce cyber risks. Rushing to buy singular tools without first laying out broad strategies could present serious challenges for IT Managers.
This is why security cybersecurity experts advise taking a step-by-step approach when moving away from perimeter-based systems. Simply put, adopting a Zero Trust security strategy is worth the effort, but only if done in small steps.
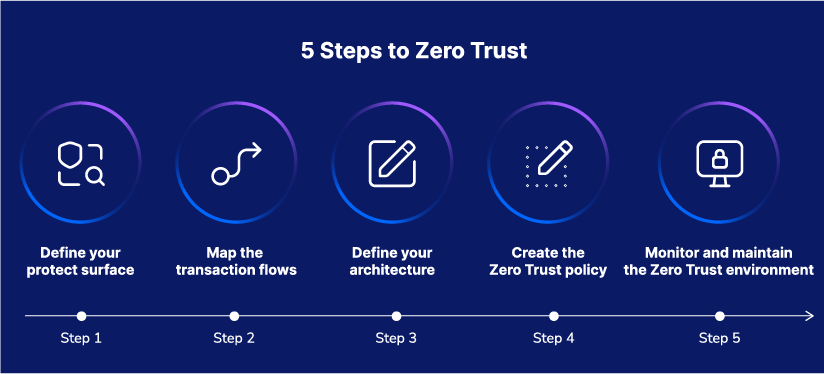
Such small steps forward are crucial since it takes quite some time to launch a full-fledged Zero Trust program. Prioritize the steps that are most important to your company, and begin with the specific network assets that employees rely on the most.
Conclusion
Overall, when it comes to revamping their information security architecture, medium-sized companies should have the following aspects in mind:
- Any type of business can follow the best practices that are often implemented by larger organizations.
- Most organizations, regardless of size, can implement strong identity authentication, “least access privileges” policies, and user integrity verification. It is easier to strengthen security postures in smaller organizations.
- It is preferable to create a roadmap and get started than do nothing and wait for a breach to happen.
Heimdal®’s Approach to Zero Trust
To implement Zero Trust for mid-sized businesses, a multi-layered strategy is needed, including defining assets, creating a risk profile, establishing identity and access management, applying layered authentication, monitoring network activity, implementing the least privilege security strategy, and last but not least, ensuring that you remove the possibility for surprises, unwanted and unapproved phenomena on the machines/endpoints. These actions are essential for protecting corporate assets and reducing the likelihood of a cyberattack.
Privileged Access Management (PAM), Application Control, and Internet Traffic control tools can play an essential part in covering numerous of the above actions.
Looking at Zero Trust from the user access perspective, Privileged Access Management (PAM) adopts a centralized approach to managing and limiting access to critical data and systems, making sure that users, after they are authorized, have only the right permissions they need to do their job.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Heimdal’s Privilege Elevation and Delegation Management (PEDM) product might be the perfect solution for your organization. Our solution will provision your users with Just-In-Time administrative rights in a seamless, secured, and controlled way. This will enable them to elevate certain pre-approved applications to administrator level or new applications upon request and approval by IT while removing the risk of them having a local administrator account (which will immediately dispel/disable/destroy the Zero Trust strategy that your organization invested so much in establishing).
Moreover, it also contains a Zero Trust Execution Protection technology that will immediately block any software missing a trusted certificate, eliminating the risk of executing malicious software on their machines.
Alternatively, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










