Contents:
XACML stands for “extensible access control markup language” and is used as a technique of fine-grain authorization because of its flexibility.
The XACML standard defines not only a language for access control policies but also a language for request and response as well as a reference architecture. Access control policies may be expressed via the usage of the policy language (who can do what when).
The request/response language allows for the expression of questions about the permissibility of certain access (questions), as well as the description of replies to those questions (responses). A standard for the deployment of essential software modules inside an infrastructure is proposed by the reference architecture.
This standard’s purpose is to enable the effective enforcement of rules.
The Attribute-Based Access Control (ABAC) protocol is supported by XACML, and assessment may be carried out using the supplemental data that is acquired from the Policy Information Point (PIP), which is described by the XACML standard design.
Terminology
- PAP – Policy Administration Point Point which manages access authorization policies
- PDP – Policy Decision Point Point which evaluates access requests against authorization policies before issuing access decisions
- PEP – Policy Enforcement Point Point which intercepts a user’s access request to a resource, makes a decision request to the PDP to obtain the access decision
- PIP – Policy Information Point, the system entity that acts as a source of attribute values (i.e. a resource, subject, environment)
- PRP – Policy Retrieval Point Point where the XACML access authorization policies are stored, typically in a database or the filesystem.
How Does XACML Work?
The following is an example of how an XACML request normally proceeds:
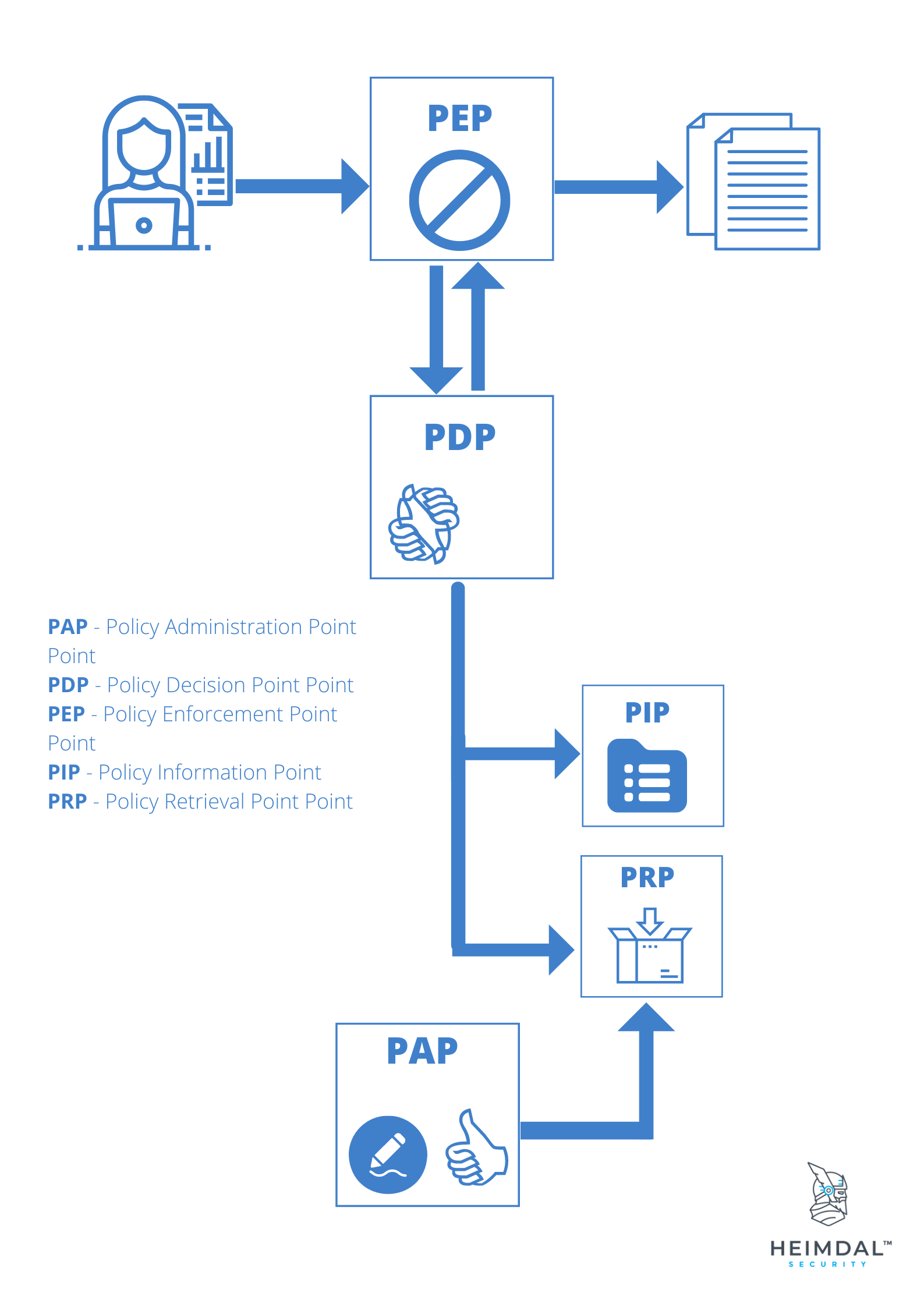
- The PEP reads a request that was sent by a user and rejects it there.
- The PEP alters the request such that it is now an XACML request.
- The request is communicated to the PDP by the PEP.
- The PDP compares the permission request to the access rules it has defined and decides whether or not the request should be granted.
- These guidelines are administered by the PAP. Attribute values stored in Policy Information Points may also be accessed if it becomes required.
- In the end, a judgment is taken at the PDP, and it either returns the value “Permit,” “Deny,” “NotApplicable,” or “Indeterminate” to the PEP in the form of a boolean.
The Structure and Syntax of the XACML Policy Language
The XACML policy language is comprised of a number of essential features that make it possible to implement fine-grained authorization across a variety of deployment patterns, including cloud, on-premises, and hosted environments. These elements may be found in the XACML policy language.
Rule
A rule is the fundamental building block of any policy. As a result, it accomplishes the purpose of the policy, which is to either grant or refuse permission. A rule may provide a goal, a condition, some advice, or a set of duties to be fulfilled.
Policy
One or more rules, an algorithm for rule verification, optional obligations, and advice are the components that make up a policy. Policies may also be written as advice. The policy serves as the basis upon which the XACML PDP may carry out its functions.
Policy set
A collection of policies that may be found in a variety of places makes up what is known as a policy set. The components of a policy set are as follows: the policies themselves, an algorithm for merging policies, optional obligations, and guidance.
Target
A target provides the XACML PDP with the ability to determine which policies or rules are relevant to a particular request. Target statements serve the purpose of defining pertinent qualities for the rule, policy, or policy set they are associated with.
Conditions
Conditions are a component of rules and are used to compare the values of attributes in order to determine whether or not an attribute is “True,” “False,” or “Indeterminate.” Checking to determine whether a subject’s username is the same as a resource’s owner property requires the use of a condition, which is shown in the XACML example that can be seen below.
Wrapping Up
XACML provides the essential building blocks companies need to iterate adding layers to solve both existing problems and those that may arise in the future.
It comes with a collection of features and functionalities that have been thoughtfully crafted with dynamic authorization using the ABAC paradigm in mind.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Managing privileges is a fundamental aspect of any cybersecurity strategy. Make sure you have the proper PAM tool and be a step ahead of hackers!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










