Contents:
Exploit kits (Eks) are collections of exploits – pieces of code or sequences of commands – created to leverage vulnerabilities in software and attack a system. Their goal is to deploy malware onto the victim`s system.
These toolkits are usually spread through malicious or compromised sites and malvertising.
Exploit kits rather focus on vulnerabilities of mainstream applications. Although most are known flaws, lots of users don`t apply patches fast enough or don`t patch at all.
Exploit kits automate the steps of a cyberattack, from reconnaissance to installation. This way, a threat actor with limited skills and knowledge can easily use exploits against a targeted system.
What Is an Exploit Kit Made of
The whole idea of an exploit kit is to include everything a hacker needs in order to launch an attack. Adversaries also use them because they automate certain processes.
Most exploit kits offer:
- a landing page,
- a management console,
- a set of exploits that target specific vulnerabilities,
- obfuscation techniques,
- various malware types.
How Do Exploit Kits Work
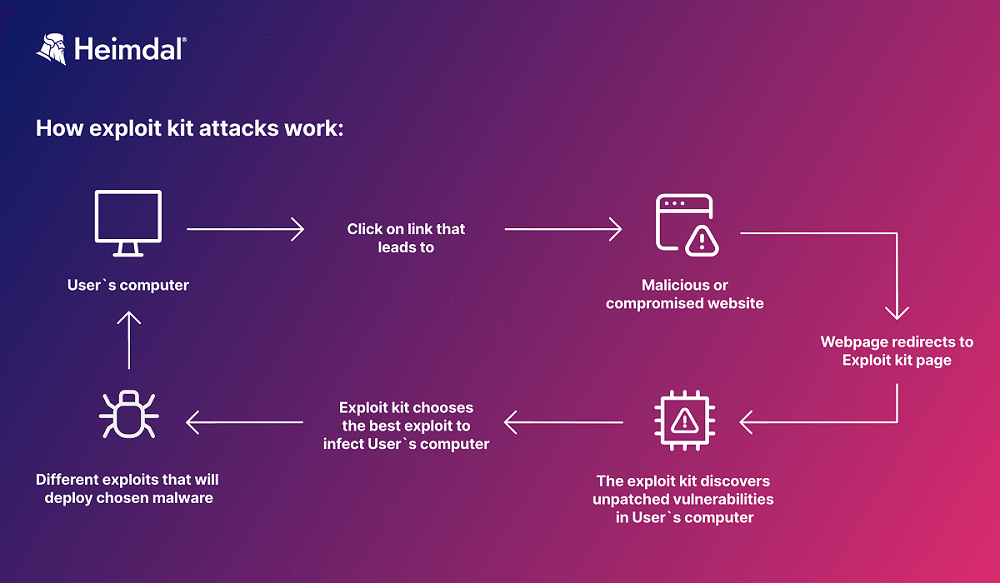
Exploit kits are used to deliver various types of malware, however, they all begin their journey the same way. They need to get online and get in contact with your device.
So, in order to distribute their exploit kits, threat actors will host them on sites they control and do their best to obtain traffic. These might be legitimate, but compromised sites, or specially crafted ones. Threat actors often use hijacking to get more traffic – and victims – on their pages.
Another distribution method is via email, by phishing, and social engineering campaigns.
Once the unsuspecting visitor clicks the link and enters the page that hosts the exploit kit, the toolkit silently starts scanning for vulnerabilities it can exploit. If all the software on the endpoint is updated and all known vulnerabilities are patched, the attack usually stops here.
But if the exploit kit finds a vulnerability that one of its exploits can abuse, it will attack.
Once the exploitation succeeds, the hacker can install and run whatever malware he/she wants on the infected machine.
Why Do Hackers Use Exploit Kits
There are at least three strong reasons why threat actors still leverage exploit kits in their attacks:
- Stealthiness
All exploit kits are meant to work undetected. They silently scan for vulnerabilities while the victim browses the internet.
- Automation
Exploit kits automate the process of finding a vulnerability and using the right exploit to abuse it. The malicious actors use a control panel, included in the toolkit, to monitor closely the effectiveness of the attack.
- Smaller cost
EKs are complex collections of tools and designing each one of them would be harder and more expensive. To cover all the functions of an exploit kit you need malware writers, exploit writers, traffic generators, compromised websites sellers, etc.
That is why hackers prefer renting an exploit kit, instead of building it from the off, to successfully deploy their malware of choice.
The Famous Case of the RIG Exploit Kit
Angler, Nuclear, BlackHole, Fallout, Phoenix, Neutrino, or Fiesta seems to have lived their glory days. But there is one of all times top exploit kits that is still active.
Although it was released in 2014, the RIG exploit pack continues to spread malware and be a threat to companies` safety. After announcing it will shut down, RIG 2.0 had a successful comeback in 2022. Its exploits targeted two Internet Explorer vulnerabilities, CVE-2020-0674 and CVE-2021-26411.
In February 2023, the RIG exploit kit was reportedly infecting endpoints via Internet Explorer. At the moment, BleepingComputer stated that the malicious toolkit attempted about 2,000 intrusions daily and had a 30% success ratio, which was the highest in its operational history.
RIG EK was observed exploiting old Internet Explorer vulnerabilities and distributing malware families like Dridex, SmokeLoader, and RaccoonStealer. It then successfully leveraged over two-year-old known vulnerabilities: CVE-2021-26411, CVE-2016-0189, and CVE-2019-0752.
All three vulnerabilities could have been fixed through patching. Also, they were all Internet Explorer flaws, a browser that Microsoft had replaced with Edge. Nevertheless, millions of employees were still using Internet Explorer on companies` devices, at that time.
Finally, in June 2022, Internet Explorer went out of support, and in February 2023 Microsoft disabled it for Windows 10.
The RIG exploit kit attacks were great examples of what using outdated software, and endlessly postponing patching can lead to.
How to Protect Against Exploit Kit Attacks
Building a strong defense strategy against exploit kit attacks is based, first of all, on keeping software up to date. Consequently, neglecting to patch old endpoints, and postponing updating applications to new versions equals inviting threat actors to breach your system.
In many cases, this doesn`t happen because lack of knowledge, experience, or poor time management. The reason is that beyond a certain number of devices that a company uses, manually patching in time every one of them is, to say the least, a burden. Manually patching 100, 200, or thousands of endpoints in 2023 is not just boring, but an unjustified time and resource-consuming method.
So, in order to protect a company`s endpoints against exploit kit attacks, here is my set of recommendations:
Automated Patch Management
An automated patch management solution that covers the whole process, from scanning to testing, deploying, and reporting leaves no door open for threat actors. It is, for the moment, the fastest and most efficient way to avoid an exploit kit attack. Make sure you patch in time all software, plug-ins, and browsers.
Last but not least, automation of processes brings down the pressure on your IT team.
Employees Education
According to the 2023 Data Breach Investigations Report, 74% of last year`s breaches involved the human element. The numbers point to social engineering attacks, human errors, or privileges misuse.
So, regularly training your colleagues to recognize phishing emails and avoid clicking on ads and popups really can make the difference. It`s true, phishing campaigns are becoming harder to spot every day. To make it even harder, hackers now use generative AI tools to create better texts. This is what leads to my next recommendation.
DNS Filtering
DNS layer security keeps threats that result from inbound and outbound traffic away. Use a DNS filtering solution to bolster your company`s cybersecurity posture and block all potentially malicious communication.
NextGen Antiviruses
Antiviruses detect and remove known threats, so even if they`re not sufficient by themselves, they still have an important role in a company`s defense strategy.

Heimdal® Patch & Asset Management Software
- Schedule updates at your convenience;
- See any software assets in inventory;
- Global deployment and LAN P2P;
- And much more than we can fit in here...
How Heimdal® Prevents Exploit Kit Attacks
Heimdal`s Patch Management solution provides users with an automated and comprehensive way to manage software patches and updates. It enables IT teams to save precious time and focus completely on their other tasks. Additionally, for increased security reasons, all patches, updates, and hotfixes are encrypted before storage and deployment.
Speed, flexibility, and convenience are three things that raise Heimdal`s Patch Management product above any other similar tool.
It offers:
- Automated vulnerability management and rapid deployment of security-critical patches and updates.
- The possibility to install and update software anytime, anywhere.
- Customized software deployment. Administrators can deploy custom, in-house software and patches that are not available in the Heimdal Patch & Asset Management catalog.
- The possibility to create inventory reports for assessments and compliance.
- A unified vision that allows you to manage all software, be it internal, 3rd party or Windows related, from a unified interface.
Wrap Up
There is no such thing as perfectly safe software. All applications have vulnerabilities, so hackers will keep trying to discover them first and then find a way to exploit them. In this equation, the best thing you can do is take prevention measures. Luckily, the current automated patch management methods make things a lot easier for both security and IT teams.
In the battle against exploit kit attacks, patch management that automatically checks for and applies available updates, patches, and hotfixes, is your number one ally.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security









