Contents:
There’s a new malware threat spreading fast on the Internet, and this time it’s targeting Facebook users.
If you get this suspicious link via Messenger from one of your Facebook friends, don’t click on it!
This malware, which replicates over Facebook’s internal messaging system, Messenger, is circulating and spreading heavily. This is a form of social engineering used to trick people and steal sensitive data.
Here’s how it works
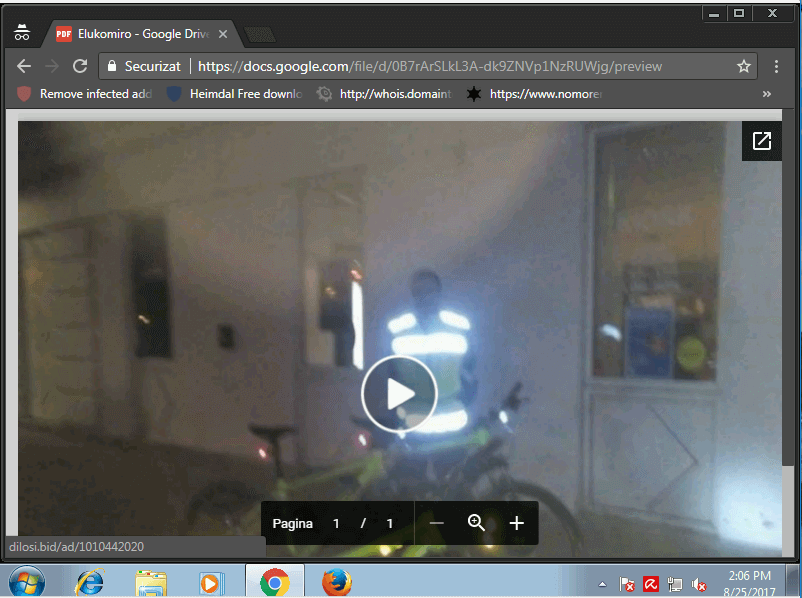
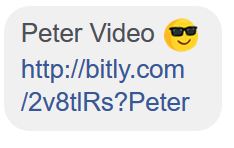
The message includes a BIT.LY link (Bit.ly is a URL shortening service) which contains a video with the person’s name. Once the user clicks on the malicious link, it redirects the entire traffic through a big chain of malicious domains.
Un-shortening the URL leads to (sanitized for your protection):
https [://] docs.google [.] com/file/d/0B7rArSLkL3A-dk9ZNVp1NzRUWjg/preview
Here is a selection of the malicious URLs involved in delivering and keeping the distribution covert (sanitized for your online safety):
Http: // bitly [.] Com / 2v8tlRs? [Name of recipient]
https://docs.google [.] Com / file / d / [unique ID] / preview
http: // dilosi [.] Bid / ad / 1010442020
q.redirecting [.] Website
FlashPlayerPro_0851280053.exe
The final destination is a domain where the malware, in this case adware, is downloaded from.
This strain of adware tracks cookies, monitors your online activity, and shows different ads that lead to potentially malicious URLs.
Researchers have discovered that this campaign uses various attack angles, such as a browser extension for Chrome and Firefox, or a binary package that installs adware on users’ computers. The binary package is offered to Safari and Microsoft Edge / Internet Explorer users.
According to SecureList, when using the Firefox browser, it sends users to a website displaying a fake Flash Update notice, and then showing a Windows executable.
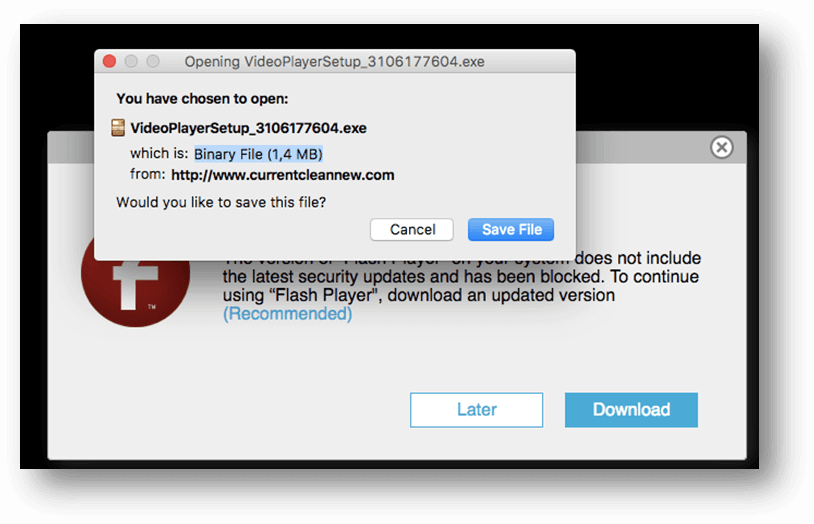 Source: SecureList
Source: SecureList
The browser extension for Chrome is a downloader, which will download a file to your personal computer.
Here how it looks:
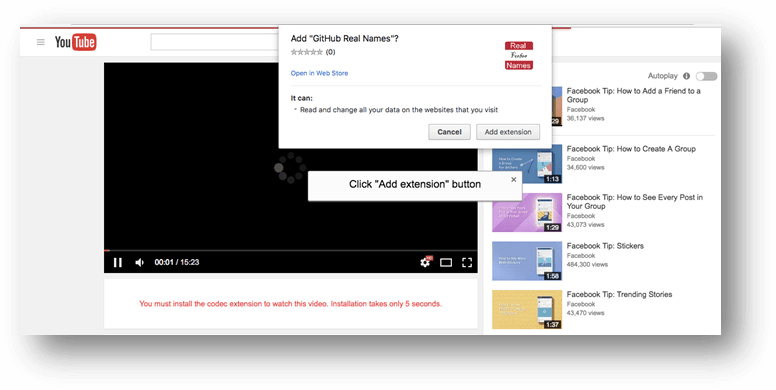 Source: SecureList
Source: SecureList
The adware is installed via (sanitized for your online safety) this website: www.currentcleannew.com and is named as a “VideoPlayer”, which looks like a playable movie that users are tempted to access.
Here is an installation package that will be installed as default to the
c: \% program files% \ Fahi folder
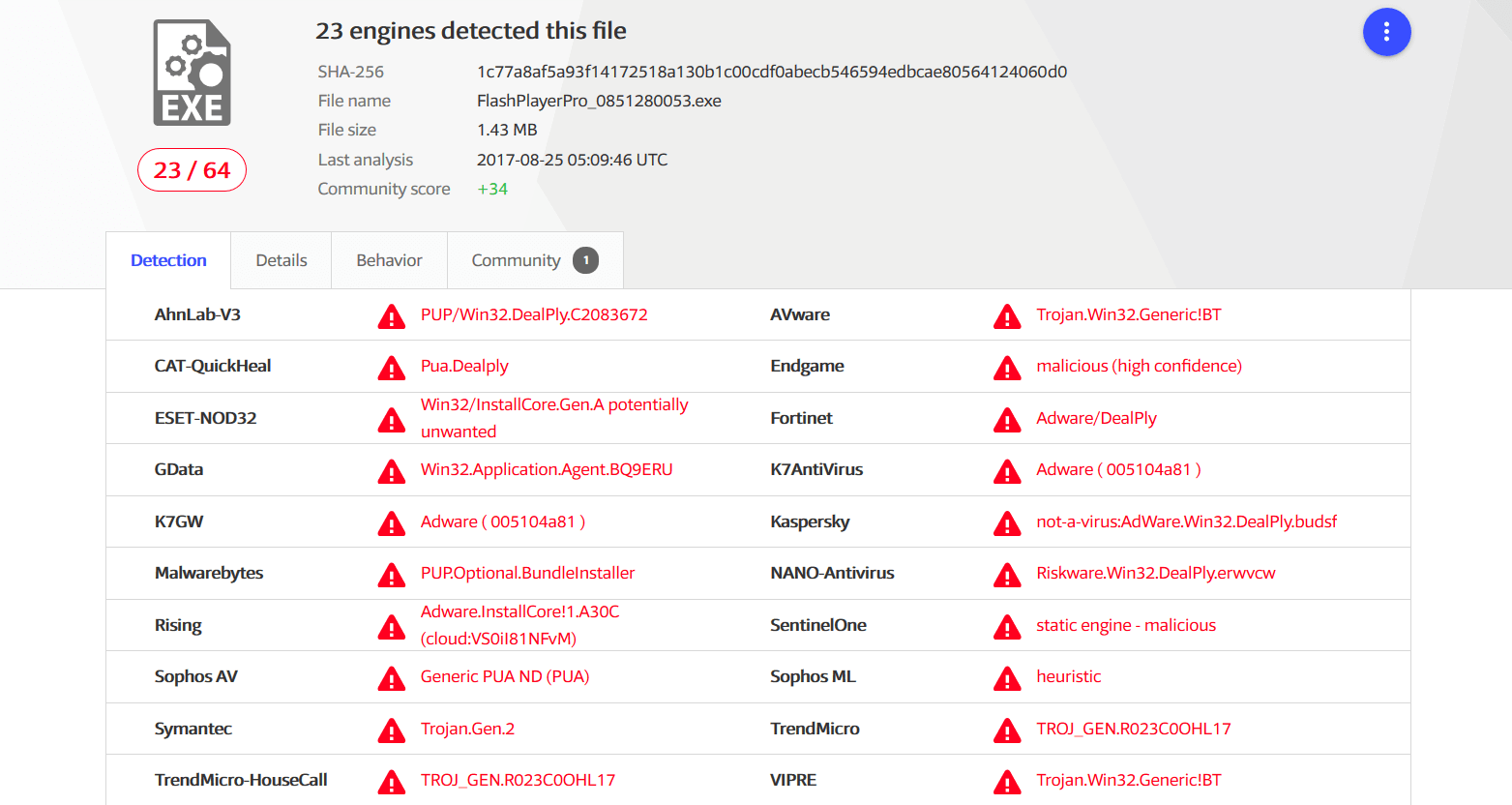
VirusTotal indicated that 23 of 64 antivirus solutions were detecting this malicious code at the time this article was posted.
Source: VirusTotal
That’s what we know about this new malware so far. We’ll keep you informed as new details emerge.
Until then, we strongly recommend being careful while navigating online. Once again: don’t click on suspicious links, and remember to install all the latest updates for any apps your may be using. Couple that with a robust security tool that can block such malicious domains and you’ll make your online life a lot safer.
Our guide can help you how to easily backup all your files on the computer and protect your valuable data.
Facebook security-wise, here are some useful tips to help you stay away from online scams:
- Do not accept friend requests from people you don’t know
- Do not share your password with others
- When logging in, use two-factor authentication
- Avoid connecting to public and free Wi-Fi networks
- Keep your browser and apps updated
- Use proactive cyber security software.
To enhance your online privacy, read our full guide on Facebook security and privacy.
*This article features cyber intelligence provided by CSIS Security Group researchers.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security