Contents:
Phishing has been around since the mid-nineties, with the first-ever malicious email of this kind being discovered in 1995. This now notorious cyber threat rose to global fame in 2000 with the infamous Love Bug virus spread. The email it came in contained an attachment claiming to be a love letter, which tricked a lot of people into opening it. Believe it or not, hackers still use similar techniques today.
Simply put, phishing is so hard to combat because it relies on deception. While systems can be beefed up with layers upon layers of defense, the human factor remains a problem. In this article, I will dive into the world of phishing attacks and everything you need to know about it, from the basic definition to tips on how to advance your strategy and achieve better enterprise protection.
What is Phishing in Cybersecurity?
Phishing is a malicious technique based on deception, used to steal sensitive information (credit card data, usernames, and passwords, etc.) from users. The attackers pretend to be a trustworthy entity (usually by copying the look and feel of a big brand) to trick the victims into revealing their confidential data.
If a phishing attack is successful, it means that malicious third parties managed to gather private data. The stolen information is then used to commit financial theft or identity theft. Hackers also leverage it to gain unauthorized access to the victim’s accounts and create an opportunity to blackmail them for various benefits.
Types of Phishing Attacks
Being able to recognize the different types of phishing attacks out there is an important part of the process of understanding what this cyber threat is. Email phishing is by far the most widely used approach, but hackers are constantly making use of other mediums to carry out their nefarious deeds. The seven most common kinds of phishing attacks are:
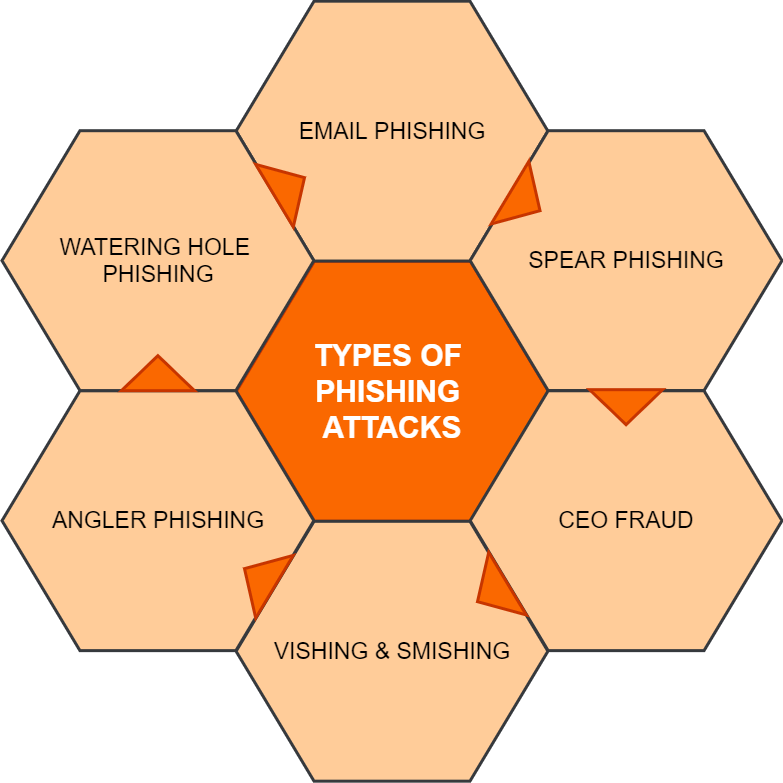
To find out more about what each type of phishing attack consists of, have a look at the dedicated subsections below.
Email Phishing
As I previously mentioned, email phishing is the most common type of phishing attack. It sees malicious actors sending out emails that impersonate the branding and messaging of known brands or company contractors. In them, they cleverly disguise infected links or macro attachments and convince unsuspecting employees to download information-stealing malware into enterprise computers.
Fortunately, there are a few tell-tale signs that help you identify phishing emails. Knowing what they are is essential to recognize phishing:
- Misspelled email addresses. These intentional typos are usually subtle, which makes them hard to detect. Look for clever changes that substitute some letters or numbers for others that look alike.
- Shortened links. It’s never a good idea to click on a shortened link you receive in an email because you might not know where it leads until it’s too late.
- Counterfeit branding and logos. Sometimes, you can tell when the imagery associated with a well-known brand has been replicated by hackers. Look for small spelling errors, slightly off-color tones, and other nearly imperceptible modifications.
Spear Phishing
Although spear phishing is another form of email phishing, it differs from the latter by taking a more targeted approach. To pursue such an attack, cybercriminals start by gathering open-source intelligence, which is found in publicly available sources such as online magazines, social media, or the company website.
With this information under their belt, hackers proceed to pose as someone trusted by the company, which makes them all the more dangerous. Knowing how to identify this type of cyberattack is thus essential in spear-phishing prevention. Here are a few things to be wary of:
- Password-protected macro attachments. If an email attachment asks you for your network login credentials or any other type of details that shouldn’t be shared freely, it’s best to err on the side of caution and report the message.
- Odd requests involving private info. It’s better to be overly suspicious than totally careless. If you receive an email from a coworker asking for confidential data they shouldn’t need, double-check.
- Shared drive links. While most of us use shared drives such as Google Drive or Microsoft OneDrive regularly for work, a link for them can sometimes hide malicious code.
CEO Fraud
Also known as whaling, CEO fraud is an ever more targeted type of spear-phishing where cyber attackers specifically impersonate the CEO of a company. This operation aims to convince employees to disclose confidential banking data, as well as login credentials and other sorts of private information. While this ruse might be the most convincing one yet, it can also be the easiest to spot. Look out for:
- Uncommon requests. Is it typical for the CEO of your company to send out emails to random employees requesting money transfers or login credentials? The answer for most companies is probably not.
- Unfamiliar sender email address. Your CEO would never send an important work request from their personal email address. If the sender’s contacts look unfamiliar, the boss is most likely not the one behind the message.
Vishing
Knowing that email phishing is not the only avenue for this kind of cyberattack is crucial in recognizing phishing. Hackers have learned to leverage other mediums for their campaigns, and vishing is one example of that.
A vishing attack relies on a cybercriminal calling you directly on the phone. During the call, the malicious actor tries to create a sense of urgency to convince you to act on their instructions. Needless to say, their suggestions are not in your best interest.
For example, a lot of vishing attacks go down during tax season, when hackers impersonate the Internal Revenue Service (IRS) over the phone. Their endgame is to convince victims to disclose their social security numbers and other confidential info. There are a few ways to tell if you are getting vished:
- Convenient timing. To create a sense of urgency to the call, cybercriminals choose to center attacks around stressful times.
- Unknown caller number. Phone numbers used for vishing are either from unusual area codes or have their caller ID blocked altogether.
- Unusual calls to action. To further convince you to give out private data, hackers make unusual requests. Think about it, would FedEx ask you what your account password is over the phone?
Smishing
Smishing is another type of phishing that takes place over the phone, this time around via text messages (SMS). Similar to vishing, these malicious communications include a call to action that is usually accompanied by an infected link. Fortunately, there are a couple of easy ways you can tell if this is happening to you:
- Unusual area code. If the sender’s number has an area code you are not familiar with, it’s a potential sign that something fishy is up.
- Delivery status change request. Most smishing attempts come under the guise of status change requests from delivery companies that you collaborate with. Instead of clicking the potentially malicious link in them, check for an email, call your courier service, or go to its official website directly.
Angler Phishing
In the age where Facebook, Instagram, and TikTok reign supreme, it comes as no surprise that hackers have learned to leverage social media platforms to serve their malicious purposes. This practice is known as angler phishing and it relies on a similar mechanism to that of vishing and smishing, making use of social media notifications or direct messages to deliver an ill-intended call to action.
- Peculiar direct messages. Not everyone sending you a DM wants to be your friend. If you receive a message on social media that seems out of place, it’s best to ignore it.
- Links to unknown websites. Is someone promoting a weird website on social media? If you use these types of platforms during your work hours, or even at home, I recommend staying away from domains you are not familiar with.
- Strange notifications. Hackers on an angler phishing campaign will sometimes send you strange notifications, such as adding you to threads or groups you have no interest in. Leave those conversations as soon as possible and don’t engage with any media that is passed around in them.
Watering Hole Phishing
Last, but certainly not least, watering hole phishing is perhaps the most advanced type yet. It starts with malicious actors cunningly researching what websites the employees of an organization access from their endpoints. They then go to great lengths to use those very same pages to deliver their payload, infecting its IP or domain with malware.
For this, hackers usually target websites that publish industry news or that belong to third-party collaborators of the pursued company. When an employee visits such a page, they unknowingly download the malicious code on it as well.
- Browser alerts. Nowadays, browsers can usually detect if a site you are visiting is infecting with malware, so don’t disregard an alert if you receive one.
- Firewall alerts. The same goes for your device’s inbuilt firewall. If it tells you something suspicious is amiss, listen to it and leave the website immediately.
How a Phishing Attack Works
Another crucial step in preventing phishing relies on knowing how it works. Moving beyond the tell-tale signs, the mechanics that go into a phishing campaign are often quite complex. For this reason, you need to familiarize yourself with the process as well to be able to recognize it.
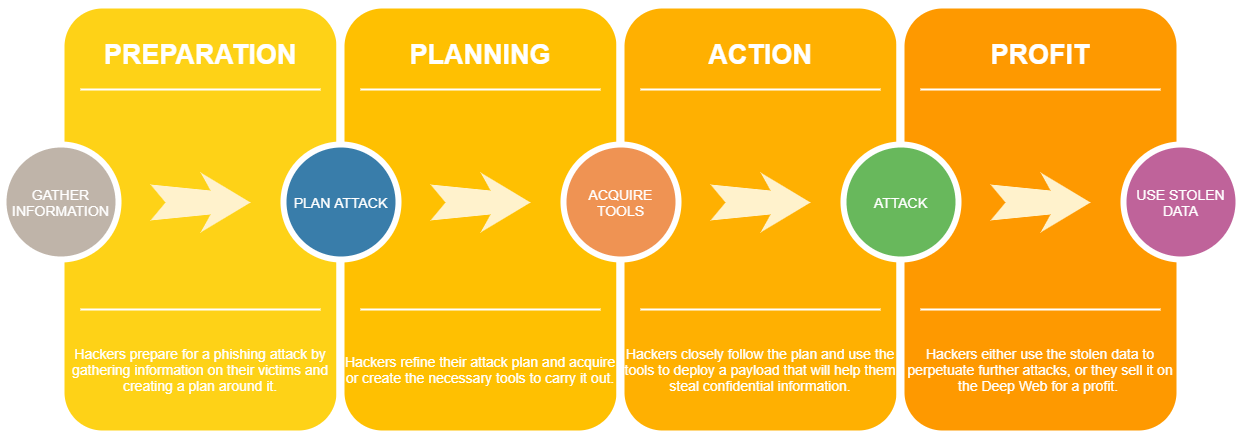
Phishing attacks are based on social engineering, which is highly efficient because it relies on psychological manipulation. This approach has four main stages:
- Preparation
- Planning
- Action
- Profit
There are five steps hackers take within these four stages, namely gathering information, planning the attack, acquiring tools, attacking, and using the stolen data to their advantage. With methods such as pretense, baiting, tailgating, or impersonation under their belt, hackers manage to convince employees that the messages they receive are genuine communications.
Sometimes, malicious actors go as far as to instill fear in their victims by alerting them of an inexistent crisis. Their biggest play is to create a false sense of urgency to their requests so that targets don’t have the time to double-check their veracity.
Once the manipulation via social engineering is successful, there is also the question of the payload. Some hackers choose to deliver their attack via an infected link, while others choose attachments that carry malware. Unfortunately, the result is almost always the same and consists of them stealing your company’s valuable private data.
Phishing Statistics
Now that we’ve established why phishing attacks are successful, you might be wondering – just how successful are they? How well do social engineering tactics work? The unfortunate answer to both of these questions is very, as the following statistics demonstrate.
- According to the FBI’s 2020 Internet Crime Report, phishing was the most widespread type of cybercrime perpetrated in 2020.
- Not only that, but incident numbers nearly doubled from 114,702 in 2019 to a whopping 241,324 phishing attacks in 2020.
- What is more, the FBI recorded 11 times more complaints regarding phishing in 2020 compared to 2016.
As for the preferred medium of delivery for phishing attacks, I’ve said it twice and I’ll say it again – email reigns supreme. However, it’s not the only possibility out there. Below, you will find some numbers on this topic that better clarify what the threatscape for this type of cyberattack looks like.
- On the authority of Verizon’s 2021 Data Breach Investigations Report, 96% of phishing attacks are carried out over email.
- Malicious websites are the driving force behind 3% of phishing campaigns, while phones make up just 1%. Vishing and smishing fall into the latter category.
- Symantec’s Internet Security Threat Report published in February 2019 revealed that 65% of cyberattackers favored spear phishing as an MO.
- The second-largest segment consisted of watering hole websites, which made up 23% of the statistic.
- In the lower ranks, Symantec identified infected software updates with 5%, web server exploits with 2%, and data storage devices with 1%.
Are companies equipped to face this ever-evolving threat? Regrettably, the data points towards a strong no. Most companies are affected by phishing attacks, and here are the numbers to prove it.
- Proofpoint’s 2021 State of the Phish Report revealed that 74% of organizations in the United States fell victims to successful phishing attacks.
- In addition to this, 60% of organizations lost data as a result of a successful phishing attack.
- Furthermore, 52% of the organizations that participated in the study had essential credentials or accounts compromised.
- On top of that, 47% of them were infected with ransomware, while 29% were victims of malware.
- Finally, 18% of the companies that responded in the report experienced financial losses as the main consequence of a successful phishing attack.
7 Essential Phishing Prevention Tips
The numbers clearly show that many companies are still unprepared in the face of email-based cyber threats. Achieving complete phishing protection is a difficult goal to set, but there are some things that you can do about it. Here are seven essential prevention tips to get you started.
#1 Provide Ongoing Security Awareness Training
Human error remains one of your biggest liabilities when it comes to enterprise cybersecurity. And with new types of cyberattacks emerging all the time, it can be very difficult for the average person to stay up to date. For this reason, your company should provide employees with ongoing security awareness training.
Well-informed staff is your company’s first line of defense against complex cyber threats. In terms of prevention, there are a few topics this training needs to approach for it to be successful. After participating in it, your employees should ideally be able to:
- Recognize the different types of phishing attacks;
- Distinguish between secure and malicious links;
- Identify malicious attachments even in seemingly benign emails;
- Avoid pop-ups and other suspicious online activity;
- And know how and when to change the passwords on their accounts.
#2 Boost Your Company’s Email Security
As I previously discussed in the section of phishing statistics of this article, the overwhelming majority of phishing attacks arrive via email. Therefore, the next priority of your strategy should focus on boosting the security of your company’s digital communications.
Popular email services such as Gmail or Microsoft Outlook already have a layer of protection against malicious messages built into them. However, if you want to prevent phishing and thwart even the most advanced attacks, you will need to beef up your spam filter.
Heimdal™ Email Security can help you achieve this. A revolutionary malware protection system, it protects your digital communications with more security vectors than any other platform on the market. Lightweight and easy to deploy, its cutting-edge spam filtering features automatically detect and remove malicious attachments, filter through infected IPs and domains, and identify suspicious links.
Heimdal® Email Security
When paired with Heimdal™ Fraud Prevention, our product becomes a state-of-the-art email protection suite. By their powers combined, the two modules leave no avenue for hackers to use your company’s digital communications as an entry point into your organization. With over 125 vectors and a live monitoring team at your fingertips, your phishing protection will be significantly improved.
#3 Use a Strong Antivirus Solution
An antivirus solution can also help to protect against phishing attacks, as it is designed to scan files for any traces of malicious code injection. Upon threat detection, this type of tool will stop the infected file from executing itself, which means that hackers won’t be able to deliver their payload in your organization’s network.
However, standard tools won’t fare well with advanced attacks, which is why your company should use a next-generation antivirus on its endpoints. An NGAV comes with advanced scanning features, as well as firewall integration, making it the logical choice.
#4 Keep All Browsers Up to Date
Attackers sometimes use vulnerabilities in outdated applications to breach organizations, and browsers are unfortunately the most weaponized. Developers release security patches for them all the time, but unfortunately, many employees fail to install them promptly, regardless of their position.
To fix this oversight, your enterprise needs an automatic software updater. This type of solution manages vulnerabilities, applying software patches as soon as they are released and effectively closing gaps in security.
#5 Use a DNS Traffic Filtering Solution
To further enhance your company’s digital defenses, my recommendation is to use a DNS traffic filtering solution to add on top of your security. With this tool under your belt, you can scan and log traffic, as well as block any malicious domains that are found.
This is something that our Heimdal™ Threat Prevention can do for you, effectively augmenting your phishing prevention strategy with protection against infected links. By covering this base, as well as all the aforementioned ones, your enterprise will stand a chance against advanced cyberattacks perpetrated by criminals that want to steal sensitive data.
#6 Disable Pop-Ups and Macro Attachments
As a final line of defense, you have the option to disable pop-ups and macro attachments. Those are two mediums through which phishing attacks are very often delivered. However, please keep in mind that this can also become quite cumbersome to manage at an enterprise level. My suggestion here is to go on a case-by-case basis – is the effort worth the reward? If not, then maybe stick to everything else on this list except this point.
#7 Implement an Incident Reporting Policy
At the end of the day, no line of defense is 100% secure. Even the most bulletproof cybersecurity solutions and the best-trained employees can be tricked by malicious actors. In case this happens to you, having an incident reporting and mitigation policy in place can make all the difference in the world.
First and foremost, set up a chain of authority. Who is the most suited person or department in the company to handle a cyberattack promptly? Be it your system admin or the IT department, that’s who employees who notice suspicious emails or any other type of malicious activity should report to.
Once the incident is reported, the person or department in charge should also have a response plan. In terms of mitigation, the first step will always be to isolate the affected endpoints. Next, the security team should take systems offline to stop the payload from spreading. If your data is backed up, restoring it should be simple enough. The goal here is to stop hackers from getting to what they want most – confidential information.
Wrapping Up…
Recognizing phishing attacks that target your enterprise communications is the foundation of a successful prevention strategy. For this reason, investing in continuous awareness training is the first thing to do.
After doing so, you can easily dedicate the rest of your cybersecurity budget to tools that complement the footing you laid down. This is where Heimdal™ comes in. If you feel that you are ready to take your enterprise’s digital defenses to the next level, then don’t hesitate to reach out at sales.inquiries@heimdalsecurity.com, and let’s have a chat.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











