Contents:
Cybersecurity researchers warns that a new data-wiping trojan has hijacked judicial courts and mayoral offices in Russia. This type of malware usually pretends to ask for a ransom, but in this case, the trojan is designed to be destructive by wiping data from files stored on victims’ computers.
At first glance, the malware, dubbed CryWiper, appears to be a tool designed to scramble files and demand money from the victim.
But now researchers have found evidence of a data-destroying function. This is why if victims pay the hackers, they won’t be able to recover their files, which are permanently deleted. These kinds of cyberweapons are called “wipers” for this reason.
Fedor Sinitsyn, a cybersecurity researcher at Kaspersky, recently said that CryWiper corrupted files on targeted devices and displayed messages demanding payment for decryption- 0.5 Bitcoin (nearly $17 thousand).
Sinitsyn found that the program does not restore victims’ files after they pay: they are deleted without the possibility of recovery. Moreover, code analysis allegedly shows this is no mistake – attackers seek both to gain financially and to destroy targets.
The creators of CryWiper write in the ransom note that your files have been encrypted, and you can only get them back if you pay. However, this is a ploy, as the data is gone for good. The activity of CryWiper has shown that even those who do pay sometimes get their files back.
CryWiper stores ransomware demands in the README.txt file and did just that with this case.
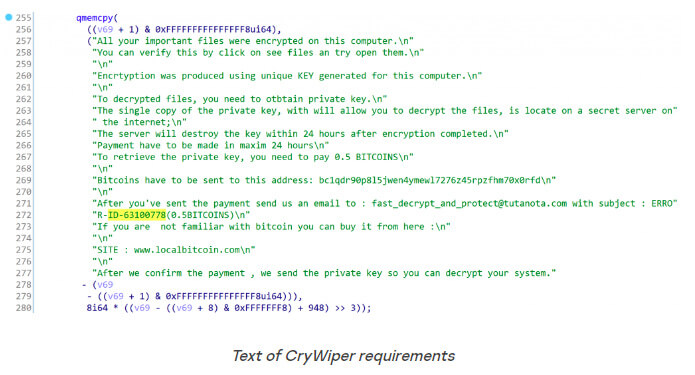
This tool provides the following:
- The Bitcoin wallet address for paying the ransom.
- The email address for contacting the attackers.
- A unique infection ID.
Multiple entities that have carried out wipers of this kind have been linked to Russia’s conflict with Ukraine. Still, Kaspersky has not attributed the CryWiper attack to any specific group or entity.
Some wipers have been more effective in Ukraine than others, such as WhisperGate, HermeticWiper, IsaacWiper, and CaddyWiper. In addition, our tests show that DoubleZero is not performing well in the Russian market.
‘Seven different wiper malware attacks have been discovered in Ukraine – all clearly in line with Russia’s interest in the war,’ Fortinet, a cybersecurity company, said back in March.
“Wipers” are operations involving the destruction of targets whose loss is in the enemy’s interest.
A DDoS attack might be motivated by a desire to cripple critical infrastructure. For example, someone may want to cause chaos or damage an enemy target.
Russia wasn’t the only target of this malware. RuRansom infected targets in March, posing as run-of-the-mill ransomware. However, the malware’s authors openly state that their attack is a response to Russia’s invasion of a neighboring country.
Often, successful attacks against wipers rely on network security being weakened. Therefore, Kaspersky advises network engineers to take precautions such as:
- Behavioral file analysis solutions provide your organization with endpoint protection.
- A managed detection and response (MDR) service will allow you to detect an intrusion and respond timely to the situation.
- With dynamic analysis of mail attachments and blocking malicious files and URLs, email attacks will be more complex than ever.
- If you want to detect and block malicious activity promptly, you must have up-to-date information about intruders’ methods.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, YouTube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








