Contents:
First spotted last week, new ransomware attacks against Ukrainian organizations have been traced back to the notorious Russian military threat group Sandworm.
The RansomBoggs ransomware has been discovered on the networks of various Ukrainian organizations, according to researchers from the Slovak software company ESET, which first identified this wave of attacks.
While the malware written in .NET is new, its deployment is similar to previous attacks attributed to Sandworm.(…) There are similarities with previous attacks conducted by Sandworm: a PowerShell script used to distribute the .NET ransomware from the domain controller is almost identical to the one seen last April during the Industroyer2 attacks against the energy sector.
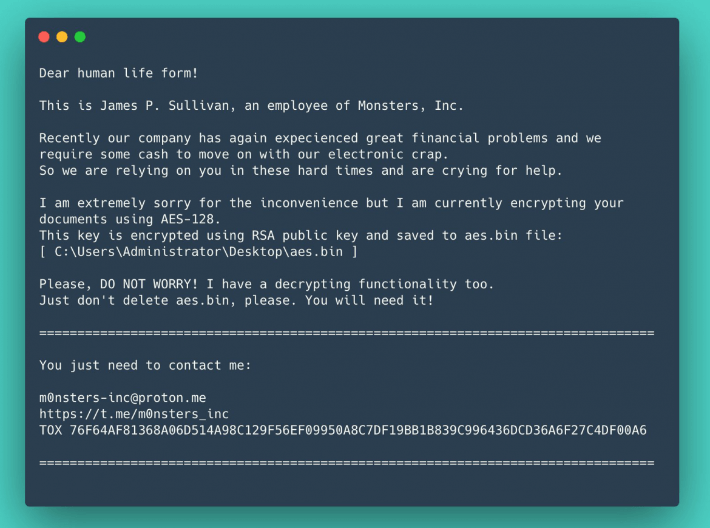
The Gang Uses an Alias from Monsters Inc. to Sign the Ransom Notes
The “POWERGAP” PowerShell script, which was used to distribute RansomBoggs payloads on the victims’ networks, was also responsible for delivering CaddyWiper destructive malware in assaults against Ukrainian organizations in March, explains Bleeping Computer.
RansomBoggs encrypts files with AES-256 in CBC mode using a random key (randomly generated, RSA encrypted, and written to aes.bin) and appends a .chsch extension to all encrypted files once it has been sent across a victim’s network.
The RSA public key can either be hardcoded in the malware or passed in as an argument, depending on the attack version. The ransomware uses the identity of James P. Sullivan, the protagonist of the Monsters Inc. film, to leave ransom notes on encrypted devices.
Since October, transportation and logistics organizations in Ukraine and Poland have been the subject of Prestige ransomware attacks, and earlier this month, Microsoft connected those attacks to the Sandworm cyberespionage group (tracked by Redmond as IRIDIUM).
According to the MSTIC), “the Prestige campaign may highlight a calculated shift in IRIDIUM’s destructive attack calculus,” meaning that there is a greater risk for those that provide or transport help to Ukraine. Overall, it could pose a threat to Eastern European groups that the Russian government sees as aiding in the conflict.
A Two-Decade History
Sandworm, a group of elite Russian hackers active for at least two decades, may be part of Unit 74455 of the Russian GRU’s Main Center for Special Technologies (GTsST), explains Bleeping Computer. They were linked to the KillDisk wiper attacks on Ukrainian banks and the 2015–2016 Ukrainian blackouts.
Sandworm is also suspected of developing the June 2017 NotPetya malware. In October 2020, the U.S. Department of Justice charged six gang members with coordinating hacking operations linked to the NotPetya ransomware attack, the PyeongChang 2018 Olympic Winter Games, and the 2017 French elections.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










