Contents:
New warnings are being issued to U.S. healthcare organizations as a new group, the Royal ransomware gang, attacks them.
The Health Sector Cybersecurity Coordination Center (HC3) —HHS’ security team— has concluded that a single group has carried out ransomware attacks against US healthcare organizations. This new analyst note was published on Wednesday.
Since the discovery of H3C, the company has been aware of attacks against the Healthcare and Public Healthcare sector. Due to the reliance on digital records by the healthcare sector, Royal is a potential risk to the HPH sector.
This ransomware group focuses on U.S. healthcare organizations after past successful attacks.
Yesterday, the Royal Foundation claimed that following every healthcare data leak, they leaked all data allegedly stolen from victims’ networks online.
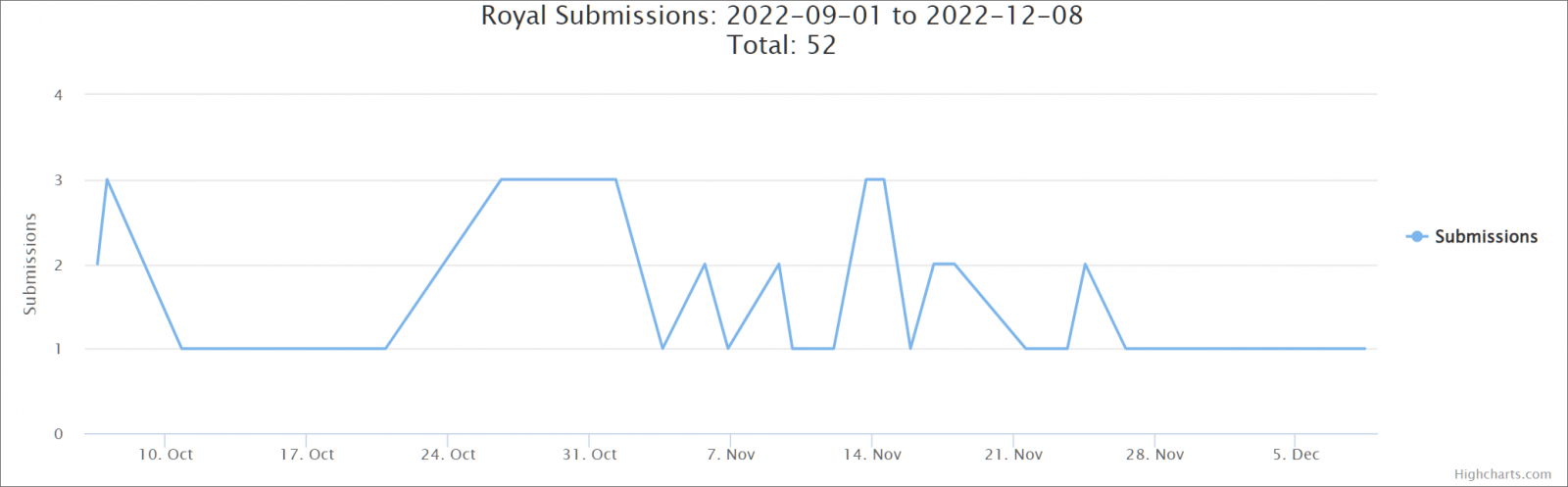
A Sharp Increase in Ransomware Activity Detected since September
The Royal Ransomware gang is a private operation with no affiliates or partnerships. The group was created by experienced threat actors who worked for other groups.
Since September 2022, Royal operators have been ramping up malicious activities. After being spotted in January 2022.
Initially, they used encryptors from other gangs like BlackCat before quickly switching to using their encryptors, such as Zeon. Unfortunately, this particular encryptor generated Conti ransomware notes.
The ransomware gang rebranded again in September and began using a new encryptor that generated ransom notes with the same name.
For ransomware gangs, it’s unusual to use social engineering as a tactic. Typically, they only rely on well-known malware. However, this ransomware gang uses social engineering instead, which has a high success rate when it comes to fooling victims into installing remote software following callback phishing schemes targeting corporate users.
The Royal gang encrypts its targets’ systems and spreads malware through social engineering. Once its targets have been infected, they will demand payment of $250,000 to $2 million.
Royal believes in using multiple strategies to get the job done. For example, they’ve hacked Twitter accounts to tweet details of their target’s activity for journalists to write about. It is just one way Royal gets it done by controlling the attack and putting pressure on victims.
The leaked data will be tweeted at journalists, owners of companies, and victims’ friends with a link to the data. These tweets will be sent before the malware encryption is deployed.
Healthcare Under Attack: What’s Next?
In addition to the ransomware attacks, the federal government also warned about other ransomware operations that have specifically targeted healthcare organizations across the U.S.
The Department of Health and Human Services recently warned against the Venus ransomware impacting healthcare, with at least one entity confirmed to have fallen victim.
Previous alert notifications notified Healthcare and Public Health (HPH) organizations of Maui and Zeppelin payloads deployed by threat actors.
In October, the CISA, FBI, and HHS released a joint advisory warning HPH organizations to stay on the lookout for ransomware attacks.
In July, Colorado-based full-service Texas company Professional Finance Company Inc. (PFC) informed of a quantum ransomware attack from late February that resulted in data breach affecting 657 healthcare orgs.
PFC helps U.S. healthcare businesses and organizations, government agencies, and utility companies collect their invoices with the understanding that on-time payment is always the best way to keep your customers happy.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










