Contents:
Royal, a ransomware operation that launched in January 2022, is ramping up quickly, targeting corporations with ransom demands ranging from $250.000 to over $2 million. The group consists of vetted and experienced threat actors from previous operations.
The group does not operate as a Ransomware-as-a-Service (RaaS), but instead, it’s operating as a private group without affiliates. According to BleepingComputer, the group first began utilizing the encryptors of other ransomware operations, such as BlackCat for example, before beginning using its own encryptors, the first being Zeon, an encryptor that generates ransom notes similar to Conti’s.
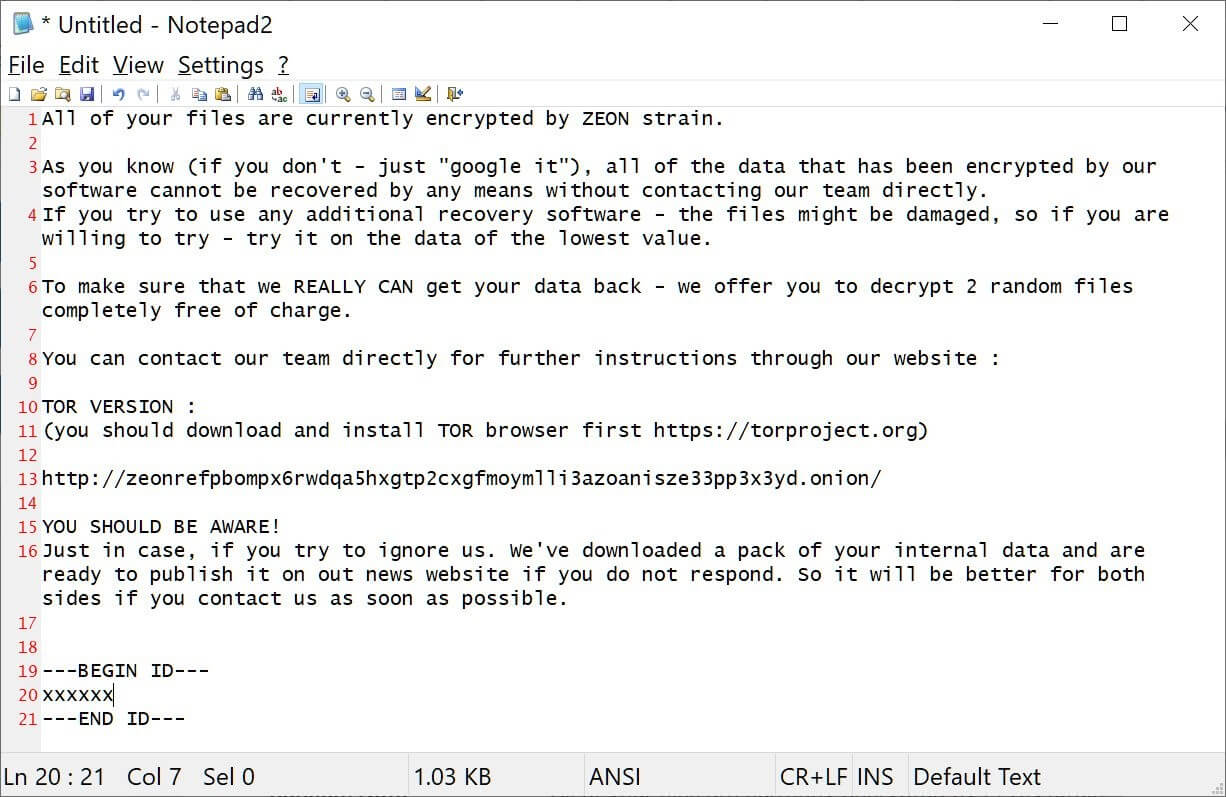
Zeon Ransom Note (Source)
How Royal Attacks Its Victims
The group has been operating quietly so far, not using a data leak site. BleepingComputer created a picture about how the gang operates. Apparently, the group utilizes targeted callback phishing attacks, where they would impersonate software providers or food delivery companies and send subscription renewal emails. The emails contain working phone numbers which the victim can contact to cancel the subscription, but in reality, they are being redirected to a service hired by the threat actors.
When the victims call the number, Royal would use social engineering to convince the victim to install remote access software, thus gaining initial access to the corporate network. They engage in the same actions frequently performed by other human-operated ransomware operations once they have gained access to a network. They use Cobalt Strike to spread throughout the Windows domain, collect credentials, steal data, and finally encrypt machines.
A victim of Royal declared that they target virtual machines by directly encrypting their virtual disk files (VMDK). The group prints out the ransom notes on the printers connected to the network, or are creating them on encrypted Windows devices. These notes are named README.TXT and contain a link to the victim’s private Tor negotiation page.
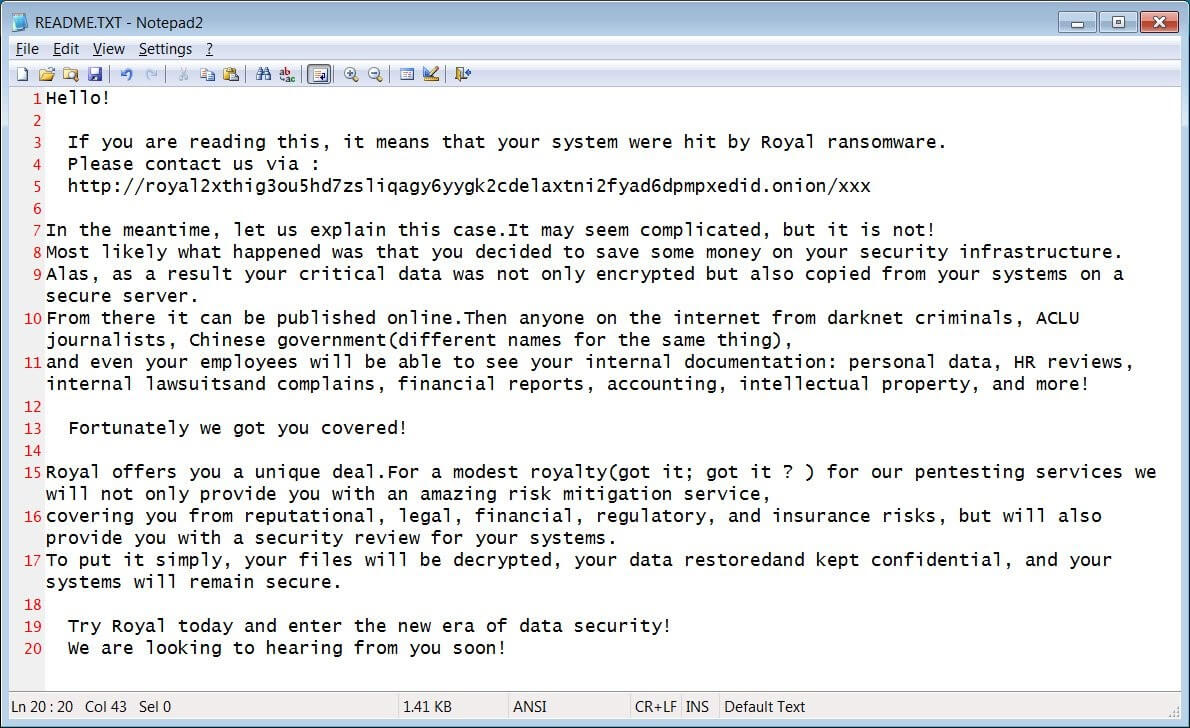
Royal Ransom Note (Source)
The Tor negotiation site isn’t an unusual method. Through the site, the victim negotiates directly with the ransomware operators. The ransomware gang will provide their demand, with ransom demands ranging from $250.000 to over $2 million. To prove that they have the company’s data, Royal will decrypt a few files and share lists of the stolen data.
The group claims to steal data for double-extortion attacks, but it does not appear that a data leak site has been launched under the brand so far. It is strongly advised for network, windows, and security admins to keep an eye on the actions of this group, as they are quickly escalating their operations and will likely grow to become a significant enterprise-targeting ransomware operation.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










