Contents:
Yesterday, all the organizations that had their files encrypted with Ragnarok ransomware received some good news! It seems that the threat actor decided to abandon its operations and also made public the master key that will decrypt its victims’ files.
Why Did the Ragnarok Ransomware Group Discontinue Operations?
The reason why the gang shutdown is still unknown, all we know is they unexpectedly removed all the impacted orgs. from their leak website, and instead left instructions on how to decrypt the encrypted files.
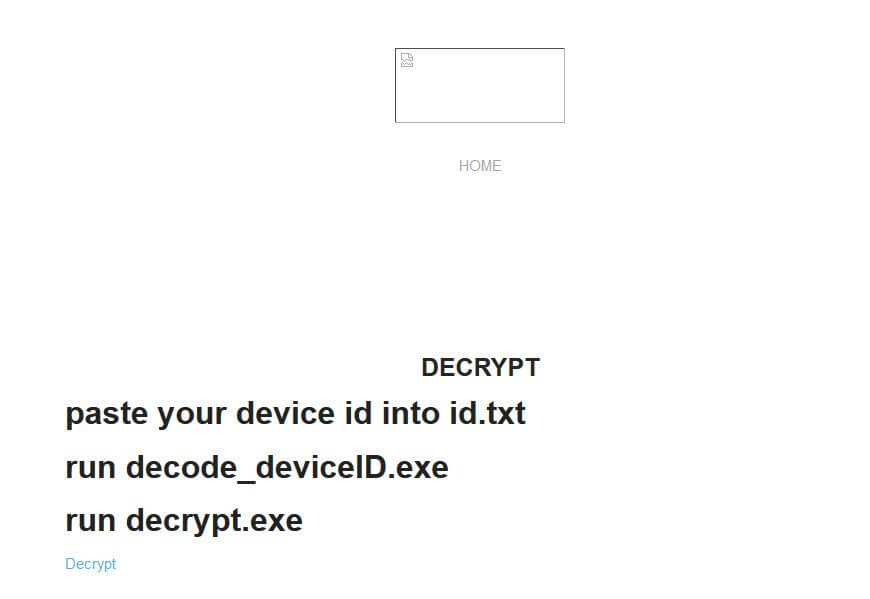
All you can find at the moment on the Ragnarok ransomware actor site is a very short message linking to an archive consisting of the master key and the binaries that go with it in order to use it.
In the picture below you can see that everything else disappeared, including the visual components.
Between July and August 2021, 12 organizations from Spain, France, Thailand, Hong Kong, Malaysia, U.S., Italy, Estonia, Sri Lanka, and Turkey fell victims to Ragnarok ransomware operations, as shown by the list displayed on the gang’s leak site.
The victims are operating in multiple industries varying from manufacturing to legal services.
The impacted companies were added to the actors’ leak website and threatened to have their encrypted files leaked in order to convince them to pay the requested ransom.
BleepingComputer was told by a ransomware specialist that the Ragnarok decryptor released yesterday contains the master decryption key.
[The decryptor] was able to decrypt the blob from a random .thor file.
More and More Ransomware Gangs Release Decryption Keys
Emsisoft, an organization that helped thousands of ransomware victims over the past 10 years is currently working at a universal decryptor for Ragnarok ransomware. According to BleepingComputer, it will be released very soon.
Discovered by the cybersecurity researcher Karsten Hahn in 2020, Ragnarok ransomware became notorious when it was found that the actor exploited a certain vulnerability in the Citrix Application Delivery Controller (ADC) to launch the random code and install malware on the targeted machine.
One of the ransomware gangs that released a decryption key in 2021 is Conti ransomware that provided the Ireland’s Health Service Executive (HSE) with a free decryption tool a week after the attack.
Also, in June Avaddon ransomware group released 2394 decryption keys for each of their cyberattack victims.
Here is a list of the ransomware decryption tools released until now. As my colleague Alina mentioned, some of them are easy to use, while others might necessitate additional experience in the tech field.
If you don’t have technical skills, you can always ask for help on one of these malware removal forums, which feature tons of information and helpful communities.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








