Contents:
During the recent Rackspace ransomware attack, the company confirmed hackers accessed customer data. Rackspace staff and cybersecurity researchers have been investigating the incident since it occurred, and new information has emerged.
The attack, which Rackspace first confirmed on December 6, 2022, impacted the company’s hosted Exchange Email service, forcing the web giant to shut it down following the incident. When Rackspace learned of the incident, the company said it did not know how the data got affected.
According to Rackspace, the hackers gained access to PST files, commonly used to store backup and archived copies of emails, calendar events, and contacts from Exchange accounts and email inboxes.
At the time of the Rackspace ransomware attack, approximately 30,000 customers used Rackspace’s hosted Exchange service.
A Deep-Dive Into the Attack
On December 2, 2022, customers attempting to connect to Rackspace’s Hosted Exchange environment began experiencing difficulties. The company soon confirmed that a data breach had occurred due to a ransomware attack.
Customers, primarily small and medium-sized businesses, stopped receiving and sending emails in addition to losing access to archived emails.
Rackspace offered them a free Microsoft Exchange Plan 1 license and advice and support for switching to Microsoft 365, in addition to working on recovering customers’ historical email data to help them regain email capability.
Most impacted customers now have access to some or all of their data, but more than 5% have downloaded malware into their mailboxes.
Several of our customers have data backed up locally, archived, or don’t need historical data, Rackspace said, but they are still working to recover as much data as possible.
According to an external Rackspace advisor, the company delayed applying the ProxyNotShell and patching the vulnerability due to reports that it caused “authentication errors,” which the company feared could bring down its Exchange Servers.
In addition, Rackspace had previously implemented Microsoft’s recommended mitigations for the vulnerabilities, which Microsoft had deemed effective in preventing the attacks.
By targeting a critical flaw (CVE-2022-41080) that allows remote privilege escalation on Exchange servers, the exploit (dubbed OWASSRF) allowed attackers to bypass Microsoft’s ProxyNotShell URL rewrite mitigations.
Additionally, they exploited CVE-2022-40882, the same bug used in ProxyNotShell attacks, to gain remote code execution.
The root cause of this incident is highly likely to be a zero-day exploit associated with CVE-2022-41080. Despite being part of a Remote Code Execution chain that was exploitable, Microsoft did not disclose CVE-2022-41080 as a privilege escalation vulnerability.
So the obvious question is, who was responsible for the attack?
Rackspace blamed the breach on the Play ransomware group, a relatively new gang that recently claimed attacks on Antwerp, Belgium, and the H-Hotels hospitality chain. Rackspace’s stolen data is not currently listed on the ransomware group’s leak site, and it is unknown to this day whether Rackspace has paid the ransom demand.
According to the incident report update, the Play threat actors gained access to Rackspace’s networks by exploiting CVE-2022-41080, a zero-day flaw patched by Microsoft in November and previously linked to ransomware incidents.
A Quick Overview of the Play Ransomware Gang
Play ransomware (PlayCrypt) is a new ransomware gang that began in June 2022. The operation has claimed a steady stream of victims worldwide. Play has recently been in the news for attacking Argentina’s Judiciary of Cordoba and the German hotel chain H-Hotels.
Play’s attacks primarily target organizations in the Latin American region, with Brazil as their primary target. They’ve also been spotted carrying out attacks in India, Hungary, Spain, and the Netherlands.
Play is well-known for its big game hunting strategies, such as using Cobalt Strike for post-compromise and SystemBC RAT for persistence. They have recently begun exploiting Microsoft Exchange’s ProxyNotShell vulnerabilities.
The group’s tactics and techniques are similar to those used by the ransomware groups Hive and Nokoyawa, leading researchers to believe the same people run Play. Let’s look at Play ransomware, its tactics and techniques, and how businesses can protect themselves from this type of threat actor.
Tactics & Techniques of Play Ransomware
Play was observed near the end of December 2022 using a method to exploit two ProxyNotShell vulnerabilities in Microsoft Exchange to gain initial access to environments.
The flaws in ProxyNotShell are as follows:
- CVE-2022-41040 – Microsoft Exchange Server Privilege Escalation Vulnerability.
- CVE-2022-41082 – Remote Code Execution Vulnerability in Microsoft Exchange Server.
Here’s an example of some encrypted files by Play ransomware:
The flaws affect Exchange Server 2013, 2016, and 2019. If successful, an attacker could use ProxyNotShell to gain elevated privileges and run PowerShell in the context of the system, allowing them to execute arbitrary or remote code on vulnerable servers. Additionally, even though Microsoft patched the vulnerabilities in November 2022, Play could circumvent Microsoft’s URL rewrite mitigations for the Autodiscover endpoint.
Play then maintained access by using legitimate Plink and AnyDesk executables. They also used anti-forensics techniques on the server to conceal their activities.
The following diagram depicts the Play ransomware infection process:
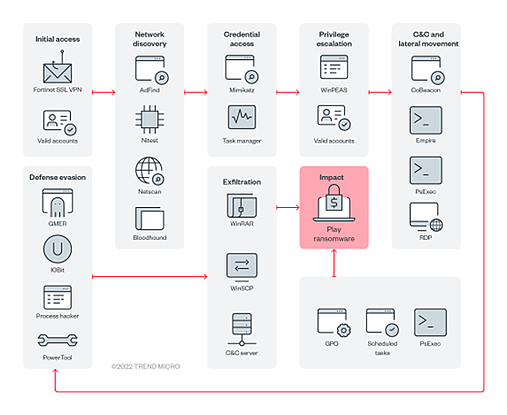
As shown above, Play’s infection chain includes using compromised valid accounts or unpatched Fortinet SSL VPN vulnerabilities to gain access to a company’s networks.
During their attacks, they employ living-off-the-land binaries (LOLBins) (i.e., WinSCP for data exfiltration and Task Manager for Local Security Authority Server Service for dumping and credential cracking).
Play, like other ransomware gangs, also employs the double extortion model on their victims. Before deploying their ransomware, the threat actor steals data and archives the victim’s files with WinRAR before uploading them to file-sharing sites.
Cybersecurity researchers investigated several Play ransomware intrusions in which they suspected the threat actors used ProxyNotShell as their entry vector.
However, after analyzing and reviewing their logs, they determined that there was no evidence of exploitation of CVE-2022-41040 for initial access but that “corresponding requests were made directly through the Outlook Web Application (OWA) endpoint – signifying a previously undisclosed exploit method for Exchange.”
Researchers also discovered evidence of a possible link between Play and Quantum ransomware. Quantum is known as a Conti splinter group.
Conti Team Two took over the ransomware operation in April 2022 but kept Quantum’s original name. Quantum is also known for using Jormungandr, their version of BazarCall, and hiring people specializing in OSINT, spamming, design, and call center operations.
What Did Rackspace Do Following the Attack?
Following the incident, the company decided not to rebuild the Hosted Exchange email environment, pointing out that it had already planned to migrate to Microsoft 365 before the hack.
Rackspace began advising customers to migrate to Microsoft 365 after discovering the breach. Meanwhile, the cloud company has been working on recovering email data from compromised servers, with more than half of it recovered so far.
Rackspace confirmed that the Play ransomware group carried out the attack. The company is not currently listed on the leaked website of the cybercrime gang. It is unknown whether Rackspace has paid the ransom.
Meanwhile, due to this incident, several class-action lawsuits have been filed against Rackspace across the United States.
Rackspace stated that the ransomware incident could result in revenue loss for its hosted exchange business, which generates approximately $30 million annually. The company also indicated that it might incur additional costs due to its response to the incident.
Conclusion
Unlike most ransomware operations, Play gang affiliates use email as a negotiation channel. As a result, they do not include a link to a Tor negotiations page in ransom notes delivered to encrypted systems.
However, before deploying ransomware payloads, they steal data from their victims’ networks and threaten to leak it online if the ransom is unpaid.
Rackspace will not provide any further updates on the incident on its status page. Still, it has promised to share more details about the attack in the future to assist other defenders in preventing similar attacks. However, there are a few things you can do in the meantime.
How Can Heimdal® Protect You Against Ransomware Attacks?
As with most ransomware attacks, Heimdal provides its customers with an exceptional integrated cybersecurity suite, including Ransomware Encryption Protection. It is 100% signature-free and universally compatible with any antivirus solution, ensuring superior detection and remediation of all types of ransomware.
We recently summarized five ways Heimdal can assist you from ransomware attacks. Please also read our articles on preventing and mitigating ransomware attacks and how ransomware spreads to broaden your knowledge.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
For more cybersecurity news and topics, follow us on LinkedIn, Twitter, Facebook, and YouTube.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










