Privileged access management (PAM) is a key part of modern cybersecurity.
In simple terms, it’s the strategy you use to monitor and control access to the most sensitive assets or data – like confidential customer information or mission-critical servers.
The logic is simple: These assets carry a unique level of risk because of the damage they can do to your organization if they’re accessed by the wrong people.
Therefore, it’s sensible to restrict user access as much as possible.
The theory might be simple, but the execution is far from straightforward.
To get it right, you need the right tools and processes. In this blog, we explain how to do just that.
For the beginning, here are some key insights from the article, at a glance:
Key Insights
- Effective PAM implementation involves identifying privileged accounts, enforcing least privilege, leveraging automation, continuous monitoring, and ensuring compliance.
- Integrating modern PAM protections such as automated credential management, multi-factor authentication, session recording, and real-time threat detection will lead enhance in security with low effort.
- PAM basics and foundations involve managing and monitoring privileged accounts to limit access to sensitive systems, ensuring security, accountability, and compliance.
- The least privilege principle is key in any effective PAM strategy. It ensures that users and systems have only the minimum access necessary, reducing the risk of unauthorized access and enhancing security.
Five Key Steps for Effective PAM Implementation

If you’re looking to implement a privileged access management strategy, you may be wondering where to start.
While every IT environment is different, there are a number of steps that most organizations should follow when implementing a PAM strategy.
Here are the five most important:
1. Identify Privileged Accounts
The first and most important step is to audit and identify all the privileged accounts that exist in your IT environment.
Most organizations will have a range of accounts that they don’t know about – and you can’t effectively implement PAM until you’ve identified them.
These include:
- Shadow/defunct accounts – Privileged user accounts associated with people who no longer work for or with the company. This could be former employees or third-party contractors. Often, these accounts aren’t deleted when the contract ends, which creates an attractive entry point for hackers.
- Extra permissions – When employees are given access privileges for a particular task or project, and keep hold of the elevated access once that need has surpassed. Again, this creates unnecessary entry points.
- Privileged service accounts – APIs, RPA workflows, and other machine identities that require privileged access. If, for example, you’ve programmed an API to retrieve sensitive customer information from a database and surface it in a customer app – that API will require privileged access in the same way as any employee accessing the same information would. These are often neglected and forgotten since organizations assume that privileged access can only be associated with individuals.
To identify these accounts, you’ll need a specialist PAM tool.
These can scan your IT environment to identify all privileges across both user and service accounts, including those you don’t know about.
2. Identify Sensitive Assets And Data
The next stage is to identify what sensitive data and assets your privileged accounts might be accessing.
This can be particularly difficult because it’s not the same for every company.
If a hacker steals a confidential product release, you’re going to have issues. If they steal the working draft of a marketing asset you published last week, you’re probably going to be fine.
The challenge is that no tool can tell you which is which.
Ultimately, it has to be a subjective judgment based on the consequences of having a particular asset or file infiltrated.
Nonetheless, most sensitive assets and data will fall into one of three broad categories:
- Critical assets: This refers to IT assets or endpoints. Common examples here could include critical servers, customer-facing applications, or anything that could lead to loss of business, service, or employee productivity if it were to go down. Generally, access to these assets is given to IT admins, security teams, or DevOps specialists.
- Sensitive data: This includes any employee or customer data that’s covered by compliance regulations like the GDPR. Principally, that’s going to involve financial details and other personally identifiable information (PII).
- Intellectual property: The final category is less clearly defined, as it involves anything that your organization wants to keep under lock and key. This could include upcoming product releases, trade secrets, or simply anything your PR team would disapprove of being leaked.
Once you’ve identified sensitive assets across all these three categories, you can start to implement least privilege.

- Mikkel Pederson, Head of Global Sales Enablement, Heimdal®
Once you’ve identified both privileged accounts and sensitive assets, the next stage is to implement least privilege.
This involves removing unnecessary access wherever possible. In particular, that involves the shadow accounts, extra service accounts, and extended privileges we identified in the first section.
By far the easiest way to do this is to group sensitive files based on who should have access to them.
That way, you can implement role-based access controls for each of these groups.
For example, HR managers would have access to employee address and salary information, but not to sensitive customer information in the CRM. For sales managers, the opposite would be true.
For basic files, this should be fairly straightforward; it’s a case of putting files into folders and controlling access to those folders.
If that data is stored in cloud or SaaS apps, it’s going to be more difficult.
Some of these will have PAM protections built in, others will not – so you’re going to have to think carefully about what tools you’re using and if they can offer the protection you need.
It may also be helpful at this stage to consider a CIEM platform to control access to data stored in particularly complex cloud environments.
Whatever tactic you’re using, the goal should be to reduce privileges to an absolute minimum.
That way, there are fewer entry points for hackers to target.
4. Implement Modern PAM Protections
Removing unnecessary privileges is a great first step – but it’s not the only tool in your arsenal.
After all, there will always be accounts that need access to sensitive information, and these identities can still be infiltrated.
But there are a range of other measures you can implement that can improve the defense of those privileged accounts that still need to exist.
Here are some of the most important:
- Credential rotation: A policy to ensure passwords are changed regularly – often combined with restrictions on password strength. Once prompted, end users are required to change their password before logging in. This ensures that leaked or stolen passwords become redundant after a certain period. Rotation policies can be defined through PAM solutions and are available through a range of other security tools.
- Multi-factor authentication: This generally involves a user authenticating via their smartphone upon-sign in, which creates an extra layer of defense. This can occur through an authenticator app, a one-time passcode, or a fingerprint scan. MFA functionality is now common across major SaaS products. They can also be implemented on an enterprise-wide level using PAM products or through a range of Microsoft security tools.
- Password vaulting: A password vault or manager is another increasingly popular tool. Here, passwords are encrypted and stored in a secure app or plugin, often without end users themselves being able to see them. This ensures passwords can be complex, unique, and regularly changed without impacting the user experience. It also avoids the passwords being saved in plain text form through insecure note apps or other media.
- Digital keys and tokens: Similar to password vaulting, this aims to remove text-based passwords entirely. Instead, access can be granted through digital tokens, keys, or IDs, which can be securely provisioned through PAM products and managed centrally by the IT team. Generally, these keys are encrypted, text-based strings of characters that are unknown to the end user and cannot be effectively reproduced in plain text form.
- Physical keys: Items (e.g. USB stick, keycard, fobs, microchips, etc.) that can authenticate individuals. Like with traditional keys, authentication rests on the assumption that only the selected individual has this item in their possession. You may decide, for instance, that anyone with a root admin account needs to authenticate via a password, a fingerprint scan, and a digital key – essentially an extended layer of multi-factor authentication.
- Just-in-time access: Another feature that can be enabled by the most up-to-date PAM or PEDM platforms. This is essentially a series of dynamic policies that grant or revoke access to sensitive assets based on context. This avoids the need for any individual to have ‘always-on’ access, also known as standing privileges. In practice, this means access can be refused if certain ‘risk signals’ (eg. new device, new location, unpatched vulnerabilities) are detected. When access is granted, it is generally done for specific reasons and for time-limited periods.
The most up-to-date products will allow you to create and implement PAM policies to decide which types of authentication should be used in which scenarios.
A good place to start is to implement MFA on all privileged accounts and use a password vault as default for all digital credentials.
Then, you can consider implementing digital keys, tokens, and just-in-time policies to enable access to more sensitive assets and data.
Whatever approach you choose, the best PAM policy by far is to create a layered defense.
No single policy will stop 100% of attacks, so it’s important to use a combination of different techniques.
5. Monitor, Audit, And Repeat
By now, we’ve identified sensitive assets, eliminated unnecessary privileges, and implemented a range of policies to keep your IT environment safe.
You might assume the job is complete at this point – but it’s important not to rest easy.
The policies you create will need to be continually reviewed to ensure you get the right balance between security and usability.
All security policies have some impact on the user experience. And when that impact becomes too severe, employees generally start finding cumbersome workarounds to avoid them – which isn’t great for security.
It’s important, therefore, to work out what the impact of your policies is so you can decide where they’re most necessary.
So how do you do this? The first stage is the most obvious: Talk to your team.
This will give you an idea of how they perceive the policies and where the biggest issues are.
If security measures on relatively low-risk assets are creating a lot of unnecessary friction, this could be a sign they’re not needed.
It’s also important to monitor what risky behavior is being detected in your IT environment.
This could be something simple like a login from a new location or something more complex like an unpatched vulnerability, or suspected malware.
This will give you an idea of the biggest risks and, by association, what policies you can put in place to mitigate them.
Generally, this information is available through most standard PASM products via ‘session monitoring’ functionality.
PAM Basics: How Privileged Access Works And Why It’s Important

- Mikkel Pederson, Head of Global Sales Enablement, Heimdal®
The key principle of PAM is to govern access to sensitive data and assets based on who actually needs it. Generally, privileges are given to specific users based on their roles.
It can be as simple as granting the IT team access to critical endpoints and HR workers access to sensitive employee information.
This isn’t a new or revolutionary concept.
But today’s IT environments are increasingly complex, consisting of servers, cloud instances, RPA workflows, IoT devices, and a whole range of other assets and endpoints.
Managing and restricting assets like these is a lot more complex than it once was.
That’s where the concept of least privilege comes in.
Simplify PAM!
Heimdal's PAM solution provides real-time visibility, session management, and automated response to threats.
Least Principle: The One Key Principle of Effective PAM

- Bogdan Dolohan, Head of Technical Support, Heimdal®
Over the last ten to fifteen years, the way we interact with technology at work has fundamentally shifted.
Once, it was common to travel to work, enter the office using a physical keycard, sit down at a wired desktop, and enter a password.
Most, if not all, IT endpoints were connected to a physical network, generally wired up to a server.
In this context, privileged access security was much more straightforward. If you could control access to a user’s specific machine, you could happily assume they were safe once they’d logged in.
Then, the cloud changed everything.
In a remote-first, multi-device world, organizations have to be much more targeted and tactical about the security measures they use and where they apply them.
This is where least privilege comes in.
Today, least privilege is essentially the bedrock of modern privileged access. The principle dictates that access should only be given to accounts that absolutely need it.
Ideally, it should also be extended to ensure access is only given when it’s needed as well.
On the surface, this is fairly straightforward.
But as we’ll discover, implementing that principle can be a more complex business.
What PAM Solution Do I Need?
Read more: Top 11 Privileged Access Management (PAM) Software Solutions in 2024
In these increasingly complex IT environments, achieving effective privileged access management (PAM) requires the right tools.
Over the last decade, a range of products have evolved to help manage the complexities of privileged account access in a remote, cloud-first world. But as new threats and ways of working emerge, new tools are required to help manage them.
This means there are now several types of PAM solution on the market, each with a different set of goals, tools, and policies.
For IT teams, this can make things uniquely complicated, because it’s not immediately obvious what security products you need.
If you have a relatively simple IT environment with few customer-facing servers and limited sensitive information, your PAM policies can be fairly simple.
But the more complex technology you add, the more specialized policies you’re going to need to help protect them.
To add to the confusion, there’s also significant crossover between the different products, meaning there’s a good chance that one tool becomes redundant once you upgrade to another.
Here are some of the most common types of PAM products on the market:

1. Privileged Access And Session Management (PASM)
The most common type of PAM solution. They help detect, manage, and monitor the use of privileged accounts, giving IT admins the ability to delegate and review permissions from a central dashboard.
They also generally feature analytics to monitor privileged sessions and activities, and often also include policies that let you define how complex passwords must be and how often they’re changed.
2. Privilege Elevation And Delegation Management (PEDM)
A more advanced PAM solution. It provides more specific and granular identity-based controls, and allows security teams to implement more stringent and dynamic controls, with a particular emphasis on just-in-time access (more on this below).
3. Cloud Infrastructure Entitlements Management (CIEM)
While traditional PASM tools are useful, they generally focus on identities at the operating system and file level.
This leaves an important gap for cloud-based services and infrastructure, which CIEM products aim to fill.
Generally, they monitor permissions and access across cloud instances, DevOps environments, databases, or any other cloud-hosted apps or websites.
4. Password Management Tools
Heimdal®: A Unique Approach to Privileged Access
Here’s the secret to effective privileged access management: It’s not all or nothing.
In this blog, we’ve explained a range of PAM techniques, tools, and features that can help you govern access to the most sensitive assets and data.
There’s no silver bullet here, and the right solution is going to be different for every company.
That’s why it’s so important to create a layered approach with multiple PAM defenses across your privileged accounts.
But as we’ve explained, there are several different types of PAM solution available.
To build this layered approach, organizations often end up building an unwieldy network that combines password managers with PASM, CIEM, or PEDM tools.
The more you add, the more complex and ineffectual the resulting solution becomes.
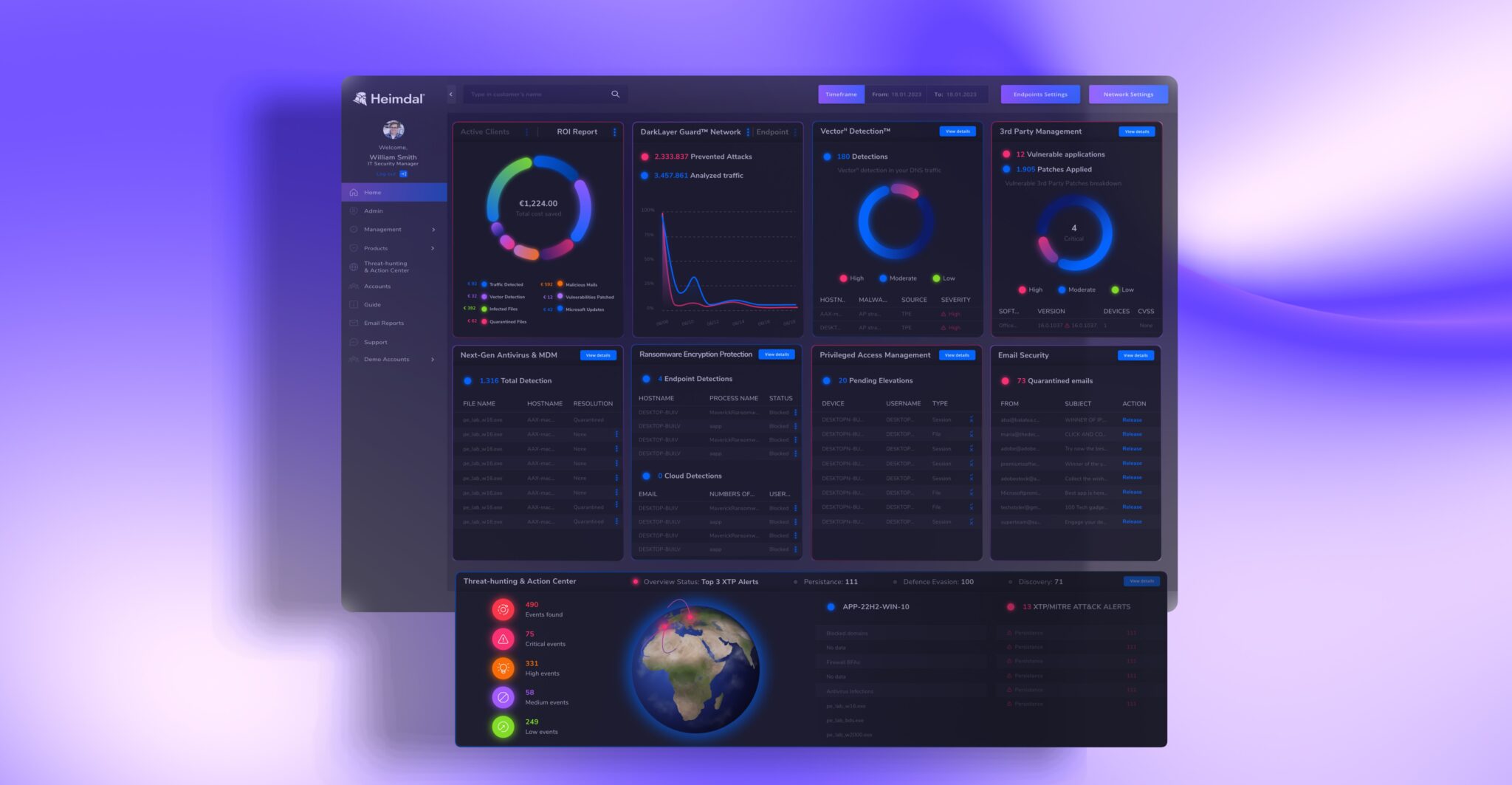
At Heimdal®, we take a different approach. Instead, our entire range of privileged access management (PAM) tools is available through one simple PAM module. This includes:
- Enterprise credential vault: A secure vault to ensure passwords are safely monitored, stored, and managed.
- Session monitoring: Real-time session analytics, recording, and playback – offering unique insights into the behavior of privileged users and simplified auditing and compliance.
- Advanced role-based access controls: Through an intricate RBAC system, you can optimize permissions management and minimize the risk of over-privileged accounts.
- Just-in-time access: Dynamically grant or revoke access based on contextual signals, ensuring privileged accounts can still be locked down if certain risks are detected.
All of this is available through the PAM module on our XDR platform.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








