Contents:
Privileged Access Management is a cybersecurity instrument that any safety-oriented company should have. Use it right and it will help you keep the company’s data and assets safe.
You’re up for a challenging mission! Implementing a top-notch PAM system means finding a perfect balance between safety and users’ comfort.
Key takeaways of this Privileged Access Management Guide
- What is privileged access
- What is privileged access management
- Privileged Access Management common challenges
- Privileged Access Management benefits
- How does privileged access management work?
- Privilege escalation attack vectors and detection methods
- Privileged Access Management related concepts
- Traditional PAM vs Modern PAM
- Privileged Access Management myths
- Privileged Access Management best practices
- Top features of a good PAM solution
What is privileged access?
Privileged access is an increased authority level over an organization’s assets that goes beyond standard user rights. It enables a team member to access and/ or edit restricted data, for example.
It can also apply to systems or software which may or may not communicate with another software. To perform certain activities in a network or computing system that a normal user cannot do, the assigned accounts need privileged access.
Average users can’t normally perform network configuration, cloud instances configuration, admin changes to apps, systems updates, etc. Only privileged users, like System Admins, Web Developers, IT Managers, etc. should be able to do that kind of tasks.
Privileged access works both on-premises or in the cloud.
What is privileged access management?
Privileged Access Management (PAM) is a system companies use to control, monitor, and secure privileged access accounts. PAM combines different methods, technologies, and strategies to keep accounts and data safe.
PAM offers visibility over the rights of persons, applications, or systems in an organization. It also makes it clear how they use those rights and helps manage that usage. This way, PAM protects the organization from both insider threats and external ones.
Proper privileged access management limits the attack surface and maintains the confidentiality and integrity of sensitive data.
As opposed to Identity Access Management (IAM), PAM only focuses on how to manage privileged accounts. In addition, PAM is, just like privileged identity management a subcategory of Identity Access Management, a domain that focuses on all user accounts.
Privileged access management common challenges
Building a Privileged Access Management strategy doesn’t mean the journey is over. Keep an eye on these common PAM challenges that may arise:
Balancing security and usability
Strong security protocols can make systems hard to use and slow down work. You need to assign users all the privileges they need when they need them to do their tasks. Avoid permitting unnecessary privileges, this can bring security risks. Audit and monitor your digital environment constantly. Get the right mix of tight security measures to protect sensitive data. Yet make it comfortable for users to access what they need for work to increase productivity.
Privilege excess risk
When a user gets a new role within a company, they also get new privileges that come with the new position. If the system admin doesn’t check and revoke previous privileges, users can accumulate unnecessary rights. This lack of revising privileges expands the attack surface.
This process of users and identities’ gradual accumulation of unnecessary privileges is called privilege creep. Privilege creep can generate:
- Insider threats as employees might misuse privileges;
- External threats in case a hacker succeeds in taking over an account;
Shadow privilege risk
Sometimes IT providers or system administrators grant end-users with local admin rights or elevated permissions at the domain level. They do it to help them solve certain problems faster.
The practice comes with a significant downside: lack of visibility. In time, it leads to losing track of who has elevated privileges over what asset.
Shadow privilege creates vulnerabilities that malicious actors can easily exploit. To avoid it, implement comprehensive PAM policies and use tools that ensure visibility and control over privileged accounts and privileged credentials.
Privileged sessions centralized management
Centralization is the key. Managing privileged sessions from a single platform comes with lots of advantages:
- streamlines processes,
- enhances security,
- ensures compliance,
- offers better operational efficiency.
However, many organizations ignore how important using a centralized approach for privileged access management is.
Complicated PAM tool interface
An effective PAM tool should also have a user-friendly interface. It should make the system admin’s tasks easier, not complicate them. A good PAM tool enables the IT team to effortlessly grant or revoke access and create users. If the process is easy, employees comply. No one goes out of their way to find workarounds if the process is already straightforward.
Logging privileged sessions
IT admins should log privileged sessions. This is a good practice for both audit purposes and further internal reviews. In case of a cyberattack, logging can help an organization see exactly where the issue occurred.
Privileged session logging can be easily solved with an automated PAM tool. Automated privileged access management enables security teams to track privileged access, generate audit logs, and provide accurate reports. This way, the company avoids fines and reputational damage.
Privileged Access Management Benefits. Why do I need PAM?

Privileged Access Management is like having a performant security system to protect your house. It’s there to make sure that only people who should get inside pass the door. It sees that only you and a selected few can reach the private rooms, like your safe or office. Using PAM is like giving certain keys to just a few trusted people.
Reduces the attack surface
PAM helps prevent unauthorized access to critical systems. By controlling who can access sensitive data and resources, it reduces the risk of security breaches.
Mitigates insider threat
PAM tools limit the potential damage that can be caused by insiders. It strictly manages privileged accounts and ensures that no trusted user can misuse their access.
Helps with compliance and auditing
PAM helps meet compliance standards. By logging and monitoring privileged access sessions, makes it easier to demonstrate compliance during audits.
Bolsters operational efficiency
Using an automated PAM solution reduces the complexity and time involved in managing access rights across various systems. PAM enables you to better manage privileged accounts.
Increases visibility
A centralized privileged access management solution brings better control and insight into access-related risks. PAM provides a clear view of who has access to what and helps identify potential security risks in time.
Prevents lateral movement
Restricting privileged access has at least one more important benefit. If the attackers take over an account, PAM prevents them from escalating their privileges. So, hackers won’t be able to move laterally and access more sensitive areas inside the system.
How does privileged access management work?
Privileged Access Management (PAM) controls and monitors access to critical resources in your network.
Its job is to manage and secure special accounts that have the right to change configurations or access sensitive data. Here are the key steps of an effective PAM process.
Privileged Accounts Inventory
The first step is to identify and track all the privileged accounts across your systems and applications. At this level, it is important to acknowledge the nature of the privileged accounts and assets in your system. Privileged account types are:
Privileged User Accounts
This first category also breaks down into several categories. These are:
- The superuser accounts
IT admins normally use these privileged user accounts. They need them for users’ removal or addition, to perform app or system configurations, install software or files, execute commands within the system, etc. In a Windows environment, these superuser accounts are also called administrator accounts. In a Linux/Unix environment they are called root.
- The local administrative accounts
These accounts serve for maintenance on workstations, servers, network devices, servers’ mainframes, etc. They can pose a risk if passwords are reused.
IT teams use local administrative access for making changes to local devices or machines. Thus, they install software or apply changes on operating systems. However, their rights are limited to the local host. Phishing attacks can enable hackers to take over such an account. Gaining access to one machine is enough to get a foothold into the network.
- The domain administrative accounts
These privileged accounts grant special access to all servers and workstations in a network. They are also known as accounts with god-mode privileges.
The risk is hackers can use them for lateral movement across a network, without being noticed.
- Emergency accounts
These are the same with break glass accounts or firecall accounts. IT teams use them to give admin access to users when necessary. Of course, this only happens with the IT management’s approval. The process is usually manual and this triggers security risks.
- Privileged business users
Sometimes, employees from other departments, like marketing, HR, finance, etc., need access to sensitive information or databases. They get to use privileged business user accounts and can only modify the data stored in specific databases. Since these users aren`t usually highly trained cybersecurity wise, you should always control access to this type of privileged accounts.
Privileged services accounts
This second category refers to permissions that non-human entities, like applications and services, own.
- Application accounts
This type of account gives apps access to different databases, or to other apps. They can also perform batch jobs and scripts running. The passwords for these accounts are kept in unencrypted plain text files. This makes the application accounts vulnerable to APTs (Advanced Persistent Threats).
- Service accounts
Applications and certain services use service accounts to communicate with the operating system. This is how you can access or modify operating systems.
- Active directory or domain service accounts
This type of accounts helps interact with the operating system. An Active Directory service account helps managing computers and users. You can use it to organize data or change passwords, for example.
Secure Credential Storage
PAM involves storing passwords and other credentials in a secure, encrypted database. This way no unauthorized user will be able to access and misuse sensitive credentials.
Access Control
PAM solutions enforce strict access control policies. Users must request access to privileged accounts. This access is granted based on predefined policies and the principle of least privilege.
Session Monitoring and Management
When a privileged user accesses a system, their session is monitored and managed. So, privileged session management can include:
- logging the session
- real-time monitoring
- terminating the session if the PAM tool detects suspicious activity
Regular Audits and Reporting
PAM solutions conduct regular audits and generate reports on privileged access. This step is essential for
- meeting compliance
- understanding access patterns
- identifying potential security risks
Password and key rotation and management
System admins should regularly enforce credentials changing, to prevent unauthorized access. A privileged access management solution can automate the changing passwords and keys process. You can change credentials after each use or after a set period, depending on your PAM policy.
Privilege Escalation Attack Vectors
Privilege escalation enables attackers to obtain more permissions within a system after exploiting a flaw to gain unauthorized access. Getting higher privileges lets hackers do more damage.
The most common privilege escalation attack vectors are:
- Credential Exploitation
- Unpatched known vulnerabilities and zero-days
- Misconfigurations
- Social Engineering
- Malware
You can detect privilege escalation attacks by using:
- Audit system logs
- Anomaly detection tools
- Behavior analysis
- Password monitoring
- Intrusion detection systems (IDS)
Privileged Access Management related concepts
Privileged Access Management relies on several related concepts. Each one of them plays a critical role in securing privileged access:
Principle of the Least Privilege (PoLP)
Only grant users the access rights necessary for their role. This way you minimize the risk of privilege abuse.
Privileged Account and Session Management (PASM)
Manage and monitor sessions of privileged accounts to ensure secure and compliant use.
Privileged User Management (PUM)
Control and audit the actions of users with privileged access to detect suspicious activity in time.
Credential Vaulting
Store credentials, like privileged account passwords and keys, in an encrypted vault.
Privilege Elevation and Delegation Management (PEDM)
Provide users with temporary privileges as needed for specific tasks. Then audit and revoke them if not necessary anymore.
Privileged Task Automation
Automate routine tasks that require privileged access. Use an automated PAM solution to reduce the need for direct human intervention. Thus, you’ll reduce human error risks.
Identity Federation
Link a person’s identity across multiple systems. This way you can streamline privileged access management.
Access Request Workflow
Implement a process for users to request privileged access. Review, approve or deny access based on your company’s PAM policies.
Traditional PAM vs Modern PAM
Traditional PAM was based on two things:
- a complex pattern of password vault
- privileged session manager (PSM) systems
It was not very efficient, as it slowed down the workflow.
Modern PAM solutions rely on the principle of least privilege, where users have the minimum level of access to do their job. Thus, it limits both insider and external threats, while allowing employees to do their tasks smoothly.
Privileged Access Management Myths
A privileged user can’t be tricked into giving up their credentials.
Privileged users are all human. Highly cybersecurity wise educated people are also exposed to phishing attacks and social engineering. Repetitive tasks fatigue, a momentary lack of attention can lead to divulging login data.
Privileged access management solutions are difficult for administrators to manage
Automated PAM solutions take the pressure of IT admins. They reduce manual tasks drastically and by that avoid human error that can lead to system breaches.
PAM is the answer to all cybersecurity issues.
Building a PAM strategy and using an automated PAM solution is a strong step in bolstering an organization’s cybersecurity posture. However, it is not enough. To keep their data and assets safe, companies also need patching, DNS filtering, E-mail security and ransomware encryption protection.
Privileged Access Management best practices
To efficiently implement a privileged access management strategy, use a PAM best practices checklist.
- Audit regularly privileged user accounts and revoke unnecessary privileges.
- Perform a risk assessment
- Apply separation of duties and segmentation of systems to prevent lateral movement
- Remove local admin rights
- Constantly monitor all privileged accounts and session logging
- Apply the Principle of Least Privilege
- Foster a cybersecurity awareness culture
- Use multi-factor authentication for all admin accounts
- Automate your PAM strategy with a Privileged Access Management Tool
Top features of a good PAM solution
Before you choose a privileged access management solution, check if it has these features that make system admins’ work easier.
- password management capabilities:
– auto-generation
– auto-rotation
- can create an approval workflow for escalating and de-escalating users’ rights
- supports management of the privileged account lifecycle, monitoring, control and sessions logging included
- uses the just in time principle (JIT), allowing only a limited amount of time for the users’ privileged session
- automates PAM tasks, like creation and deletion of users or user account configuration.
- enforces multi-factor authentication for admins.

Heimdal® Privileged Access Management
- Automate the elevation of admin rights on request;
- Approve or reject escalations with one click;
- Provide a full audit trail into user behavior;
- Automatically de-escalate on infection;
Heimdal Privileged Access Management
Heimdal’s Privileged Access Management makes it easy to manage user rights and file executions. It includes a Zero-Trust feature that checks unknown apps for safety.
Also known as Heimdal® Privilege Elevation and Delegation Management, it allows IT teams to manage lower-privilege accounts with controlled administrative rights. Users can manage their elevated PAM sessions via a user-friendly dashboard. You can also access the dashboard from your mobile.
What can you use the Heimdal dashboard for?
- track privileged sessions
- block system file elevation
- revoke admin rights
- request admin privileges
The tool works on both domain-joined and non-domain-joined computers, and offers two methods:
- ‘Run with PAM’ for single-file elevation
- ‘Administrator Session’ for broader admin rights
What does the PAM module display?
Our PAM module in your Heimdal Agent gives you data about the following aspects:
- Accepted elevations
- Pending elevations
- Denied elevations
- Username
- Reason
- Request date
- Status
- Duration
What does the privileges & app control – PAM view display?
Here you’ll find all the information that the Heimdal Agent collects from your company’s endpoints
- history
- approvals in pending status
- most escalated processes
- most escalating hostnames
- compliance reports
- processes that the Zero Execution Protection engine detected
Case Study
To better understand what exactly Heimdal PAM does, we will provide details including which apps our PAM elevates, on how many endpoints PAM ran, and more.
From a file elevation perspective, the main elevated apps from Heimdal’s Privileged and Access Management tool are
- powershell
- command prompt (cmd)
- Microsoft Smap-In Control
- task manager
- browser
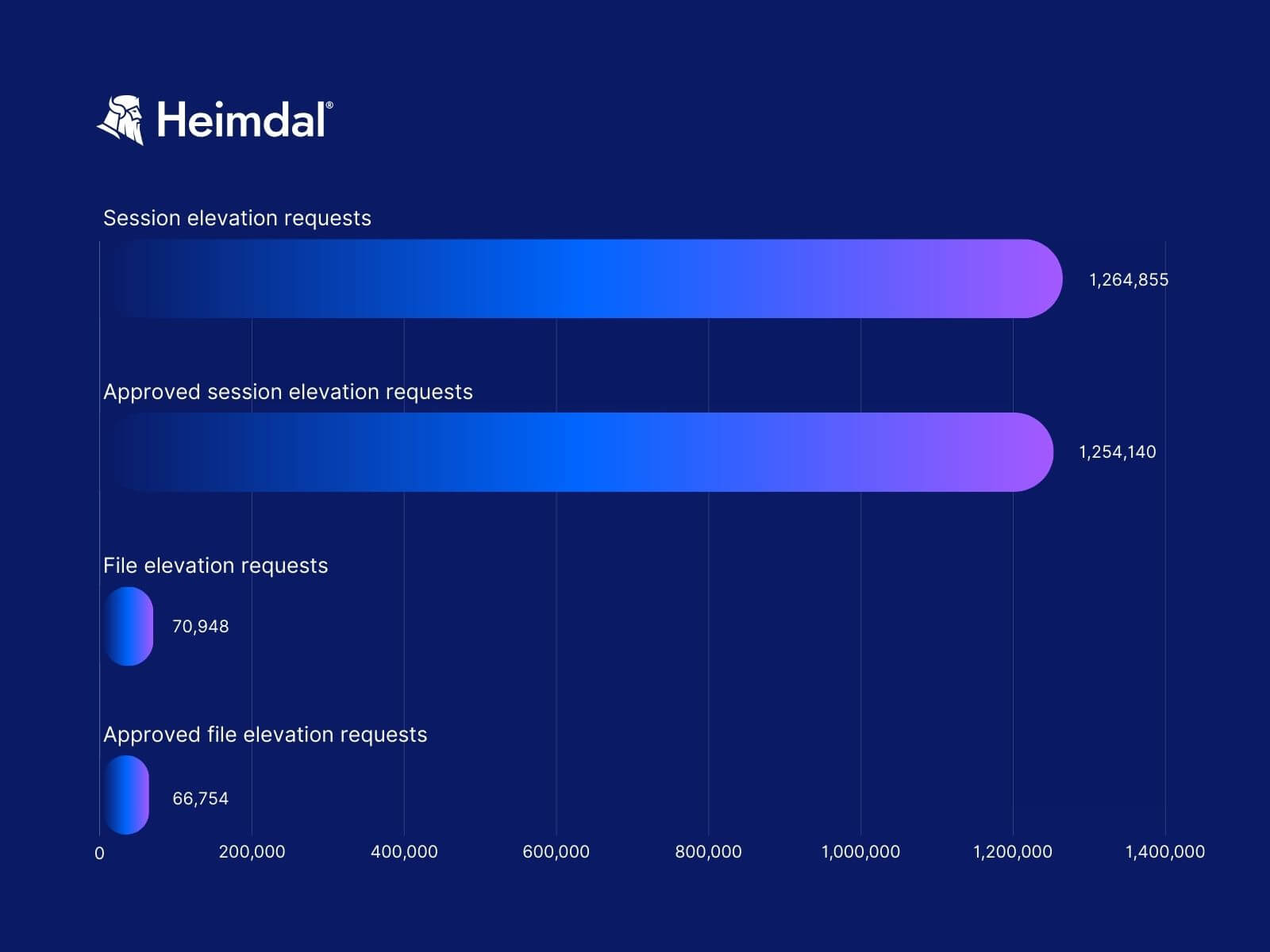
Since the beginning of 2023, our Privilege Elevation and Delegation Management Tool performed 1,264,855 session elevations and 70,948 file elevations. Out of those, the tool approved 1,254,140 session elevations and 66,754 file elevations.
Now do the math. How much time would an admin team have spent to check all that for:
- user’s accountability
- infection sources
- potentially malicious software installation?
Conclusion
Privileged Access Management is an essential component of a robust cybersecurity strategy.
It prevents both internal and external threats by managing and monitoring privileged access to critical systems and data.
Automated PAM tools enable IT managers to control, audit, and report on privileged activities. They help with maintaining security, complying with regulations, and risks mitigation.
Adopting a comprehensive privileged access management solution is a proactive step towards strengthening an organization’s overall security posture.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube, for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







