Would you buy a car without checking if it has an engine? If you did, you’d wish you’d looked under the hood before investing.
The same applies to privileged access management. Without the right controls, you expose yourself to bad actors.
Even with PAM software in place, it’s important to check its features and capabilities.
Key takeaways
- Best PAM solutions offer features like granular access, session monitoring, secure remote access, and automation.
- Basic access control isn’t enough for securing privileged accounts.
- Just-in-Time access and threat analytics limit credential exposure.
- Automation reduces human errors and simplifies privileged access management
- PAM helps meet compliance with detailed audit and reporting.
- Secure credential management and multi-factor authentication prevent unauthorized access to privileged accounts.
Heimdal's PAM Solution provides real-time visibility, session management, and automated response to potential threats.
Simplify Privileged Access Management!
Key features every PAM solution must have
PAM key features make the difference between a solution able to face advanced threats and a simple set of rules and policies. It takes more than using a complex password and removing admin rights for regular users to prevent a system breach. Here are the key features that make a PAM software best-in-class:
Granular access controls
Granular access restrictions enable businesses to set and enforce permissions for each privileged account. This ensures users only have the access privileges they need to carry out their tasks.
A least privilege access policy reduces the risk of unauthorized access to sensitive assets. Granular access controls help enable more precise role-based access.
Session monitoring and recording
The best PAM systems provide session monitoring and logging. They log all privileged users’ activities, including command-line and video sessions.
In Heimdal’s Privileged Account & Session Management dashboard, for example, you can simply click on ‘view sessions’ for details like:
- User Nick Nicholson connected at 09.30 a.m. to the Ubuntu server.
- Connection ended at 09.31 a.m. The session took 18 seconds.
- See video recording of user’s session.
Monitoring privileged sessions enables security staff to detect suspicious activity in real-time. Thus, they can respond faster in case of an incident.
Top PAM solutions securely store the session recordings. This is a feature that you can use to generate reports on privileged user access and activity. These reports are a valuable resource for auditing and PAM compliance.
Just-in-Time (JIT) privileged access
The Just-in-time (JIT) privileged access feature controls when and for how long a user gets elevated privileges. In case an attacker attempts using compromised privileged credentials, applying this principle will narrow down the exploitation time.
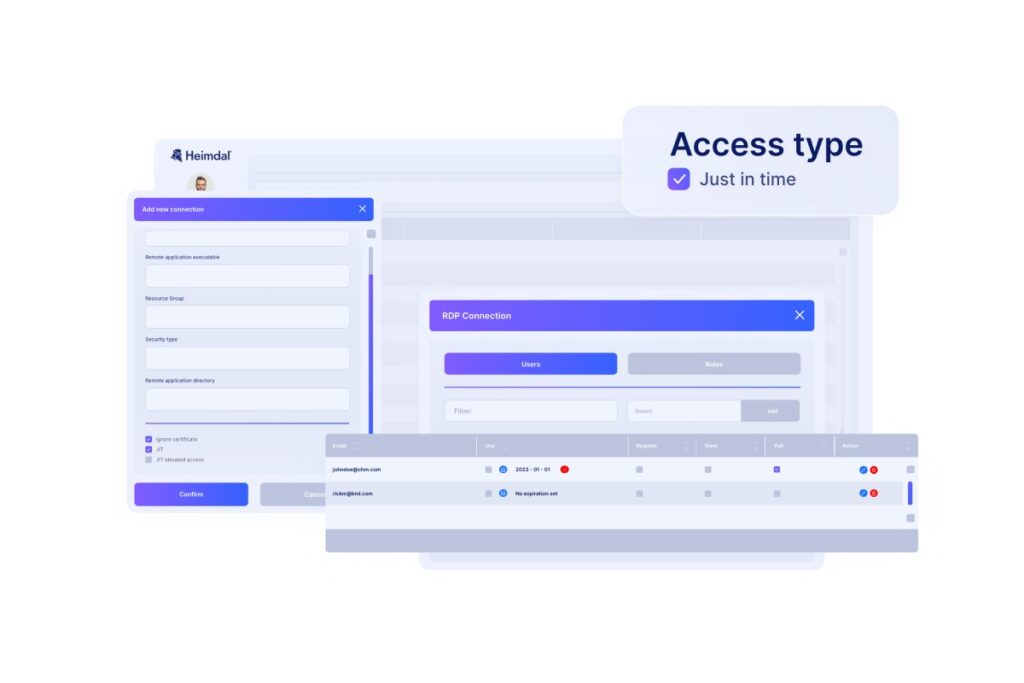
Automated workflows and access requests
Automation in privileged access management tools brings two main advantages.
- First, it makes managing access requests more effective. Automating the approval and revocation of privileged access saves time. It reduces the IT and security teams’ redundant work volume and ensures an ongoing workflow.
- Second, automation reduces the chances of human error. According to the 2024 DBIR report, human error is one of the most frequent causes for data breaches.
Privileged threat analytics
Privileged threat analytics uses advanced algorithms and machine learning. Its superpower is analyzing privileged users’ behavior to find anomalies in access patterns. Here are some examples of such indicators:
- login at unusual hours
- login from restricted geographical areas
- frequent and failed login attempts that could point to a brute force attack
- privileged user requesting access to files and systems that exceed their usual permissions level
Credential management
Effective credential management is essential for any PAM solution. This feature enables safe storing and managing for privileged credentials. Privileged credentials include:
- passwords
- SSH keys
- certificates
A strong PAM system automates password rotation and expiration. This prevents password reuse, a common vulnerability in case of a password spraying attack.
Automated discovery and management
Automated finding and managing privileged accounts and credentials keep the privileged assets inventory up to date. This reduces the risk of orphaned accounts and privilege creep.
Not revoking old permissions when a user’s work responsibilities change results into privilege creep. Consequently, users having excessive privileges increases the risk of misuse, insider threats, or security breaches.
Secure remote access
Organizations that adopted remote or hybrid work environments need to secure remote access for their employees. Secure remote access is also an issue for companies that run offices worldwide.
Using industry-standard protocols like Secure Shell (SSH) or Remote Desktop Protocol (RDP), along with a top privileged access management tool enables privileged users to initiate secure remote connections.
Understanding Privileged Access Management (PAM)
Privileged Access Management (PAM) is a set of tools, processes, and policies that controls, monitors and secures high-level privileged accounts.
The best PAM solutions work like a chief keyholder in a castle. They grant privileged access only to those who need it and only when necessary.
Just as the chief keyholder knows who should receive a key, for which room, and for how long, a PAM system ensures precise control over access.
To maintain security and avoid privileged access risks, the keyholder also:
- monitors activities within the unlocked rooms.
- audits access regularly.
- assesses whether a key should be retrieved or kept by the holder.
Privileged access risks
Privileged rights mismanagement puts the company’s safety at risk. Here’s why.
System Administrators or System Engineers accounts have elevated permissions. They can access sensitive data, install, configure, and execute various software on the company’s machines.
Leaving a default username and password on for such an account can enable attackers to:
- create back doors for a third party;
- lock legitimate users outside the system;
- deploy malware;
- disable security measures, etc.
So, managing privileged accounts and sessions should get your full attention.
Benefits of Privileged Access Management
Some of the key advantages of adopting a robust PAM solution are:
Low unauthorized access risk
By enforcing strict access controls, PAM reduces the risk of unauthorized access to sensitive data and systems. In addition, implementing the principle of least privilege helps reduce the impact in case of a breach. The risk of lateral movement will be lower if hackers manage to compromise privileged credentials.
Heimdal's PAM suite makes enforcing the least privilege principle across your organization seamless and effective.
Implement Least Privilege with Ease!
PAM’s continuous monitoring capabilities also help detect security threats in real-time. If it detects suspicious activity, the tool can terminate and report the privileged session.
Logging privileged sessions supports forensic teams to track an attacker in case of a cyberattack.
Two other factors that lower the unauthorized access risk are PAM’s automated password management rotation and multi-factor authentication.
Enhanced compliance with regulatory requirements
PAM solutions help organizations comply with GDPR, HIPAA, and SOX. They provide detailed audit logs and reports of privileged access activities. This creates a clear and safe trail of privileged users’ activities which is essential for meeting audit requirements.
Furthermore, automated workflow reduces non-compliance risks by cutting human error and keeping exact track of all privileged access.
Increased efficiency and productivity
Through automation, PAM solutions can reduce the workload on IT and security teams.
Automated discovery and privileged credential management streamline the management of privileged accounts.
Instead of having a System Administrator check and approve all privileged access requests that can occur in a 1000 people company, imagine it all happens with a few clicks and setting the right PAM policies.
John from Accounting will be happy to access the database he needs and carry on with his task without interruptions. Streamlining the work process gets easier even for organizations that work in shifts or across different time zones.
Meanwhile, instead of responding to redundant access requests, the IT staff can focus on other issues.
Better visibility and control
Privileged access management solutions that use a unique dashboard give companies full visibility and control to all privileged accounts and activities.
The IT team will be able to see who gets access to what, when and for how long, no matter if the privileged accounts are owned by employees, third party operators or apps. They can also see how those accounts used their elevated privileges and what happened during the privileged session.
In case of an attack, full visibility and control will enable fast and precise incident response.

PAM vs Basic Access Controls
Basic access controls limit who can access certain systems, regardless of the permission level. Traditional access controls lack depth and specificity.
An effective PAM solution does more than set permission rules. It enforces granular access control, monitoring, and credential management. These key features help:
- preventing unauthorized access
- avoiding compliance breaches
- stopping hackers from using compromised privileged accounts for malicious activities
On the other hand, traditional access control only covers:
User authentication
Basic access control systems typically require users to authenticate through a username and password. Most of them don’t use multi-factor authentication. So, if a hacker compromises these credentials, they’ll be able to use the account as they like.
Granting role-based permissions
Depending on the user’s role or group, a traditional access control system will allow or deny access to certain files, systems, or functions.
Static access rules
Users get continuous access to specific systems or resources, regardless of needs or behavior related changes. For example, if a privileged account engages in a suspicious activity, the basic access control solution will not be able to detect it and deny further access.
Unlike PAM solutions, basic access control doesn’t monitor privileged sessions or analyze suspicious activity.
Cybersecurity Expert Robertino Matausch explains how Heimdal’s Privileged Account & Session Management solution helps protect critical infrastructure.:
Heimdal Privileged Access Management
Heimdal’s Privileged Access Management suite addresses modern IT issues by streamlining and automating processes. Another great advantage of this solution is that you can manage all privileged accounts and sessions from a unified dashboard.
Some of Heimdal’s PAM suite key features are:
- Granular Access Control and secure remote access. The solution enables direct access to remote servers. No agents, no plugins, and no other software. The remote connection is safeguarded through encrypted channels.
- Credential vault and multi-factor authentication. Heimdal’s Privileged Account and Session Management offers various authentication methods for secure connection passwords: Local User, Microsoft Azure, and Local AD Login.
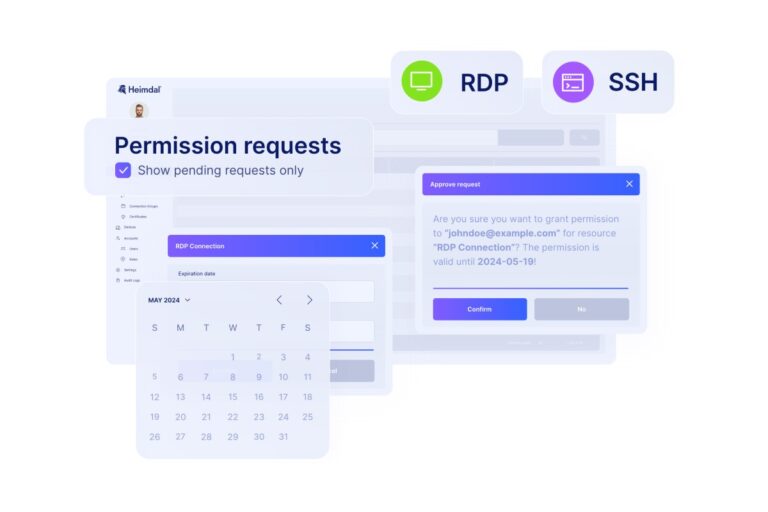
- Automated workflows and access requests. Book a demo to see how Heimdal’s just-in-time access request system offers safely managed temporary permissions.
- Threat analytics and risk management. Along with real-time session monitoring, you get deep insights into user behavior. You’ll gain comprehensive visibility and valuable forensic data. Session recording and playback capabilities will also support your audit and compliance needs.
- Seamless integration. PAM works with existing security systems, like IAM and SIEM. This ensures a smooth transition into your security strategy.
- Works both on premises and in cloud and provides continuous security as the company grows.
Follow Cosmin Toader, Heimdal’s CTO, in a product walkthrough that showcases some of Heimdal’s PAM features that your company could benefit from:
Conclusion
Applying PAM best practices boosts security, ensures compliance, and improves efficiency. Smart PAM solutions help implementing the best security measures across your infrastructure. Heimdal’s PAM suite turns handling privileged accounts and privileged sessions into an effortless task.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








