How to implement privileged access management in your organization:
Effective privileged access management is a bit like maintaining a particularly unruly hedge: There’s no point trimming it back once and then leaving it indefinitely. If you want to keep on top of privilege creep, PAM needs to be a constant and iterative process. Here’s what that involves:
- Identify privileged accounts – First, run a privileged account scan to identify all elevated rights across user and service accounts. Ideally, you should have a centralized inventory that is regularly monitored and updated.
- Identify sensitive assets – Then, determine what critical systems and data privileged users may need to access. This will largely include sensitive data (personal and financial information for customers/employers), intellectual property, or critical IT assets.
- Remove unnecessary access – Then, eliminate any unnecessary privileges across user and service accounts.
- Implement modern PAM protections – There is a whole range of tools at your disposal to protect admin accounts. This could include role-based access controls, just-in-time access, multi-factor authentication, and more.
- Monitor privileged accounts – The best PAM tools also include features to monitor activity on privileged accounts. Using anomaly analysis, this can help you proactively identify suspicious behavior, so hackers are identified before they can do damage.
💡Deep dive: Effective Privileged Access Management Implementation: A Step-by-Step Guide
How to conduct a successful privileged access management audit:
Conducting a privileged access management audit is an important way to diagnose the health of your PAM strategy and understand how to improve it. This is important to do when rolling out a PAM policy and should be reviewed at regular intervals thereafter.
Check out the full guide below to find out the key steps to an effective PAM audit.
💡Deep dive: How to Conduct a Successful Privileged Access Management Audit
How to create a privileged access management policy:
Creating a PAM policy is similar to the steps we took in the ‘implementing privileged access management’ section above. But crucially, this involves a series of subjective decisions about what PAM protections you’re going to include and how you’re going to implement them.
These include:
- Which sensitive data/assets exist in your organization that require protection?
- What tools you’re going to use to govern access, including PASM, PEDM, CIEM, password management tools, and more?
- Which risk signals require a response, and what those policies will be? Eg a user logging in from a new location could require multi-factor authentication.
- How you’ll govern password policies. This could involve rules to enforce password strength and rotation, or implementing password vaults, multi-factor authentication, and more.
💡Deep dive: What Is a Privileged Access Management Policy? Guidelines and Benefits
💡Deep dive: How to Create an End-to-End Privileged Access Management Lifecycle
How to manage cloud-based PAM security
Today, there are few IT environments that don’t depend on some level of cloud technology.
For privileged access management, this creates key challenges. Often, each cloud app or environment will have its own set of privileges – making it difficult to manage these centrally.
However, a series of cloud-specific PAM features can help manage these challenges:
- Continuous monitoring: This involves session management tools to monitor activity on privileged accounts and respond to suspicious events.
- Just-in-time access: Removing standing privileges entirely can make it much easier to avoid privileges developing on cloud apps or instances that you don’t have visibility over.
- Automated discovery: Privileged account discovery can help us identify accounts and identities across cloud apps that may not be officially sanctioned or monitored by IT.
- RBAC controls: This can reduce the confusion and hassle of managing admin rights. Since there are fewer job functions than individuals in an organization, it’s easier to delegate permissions based on a user’s place in the org chart.
- Password encryption: Security tools are increasingly evolving past the need for end users to remember plain text passwords. Instead, a combination of multi-factor authentication, password vaults, encryption, and tokens can be used to authenticate users based on more reliable factors.
💡Deep dive: A Guide to Effective Cloud Privileged Access Management
💡Deep dive: The Complete Guide to PAM Tools, Features, And Techniques










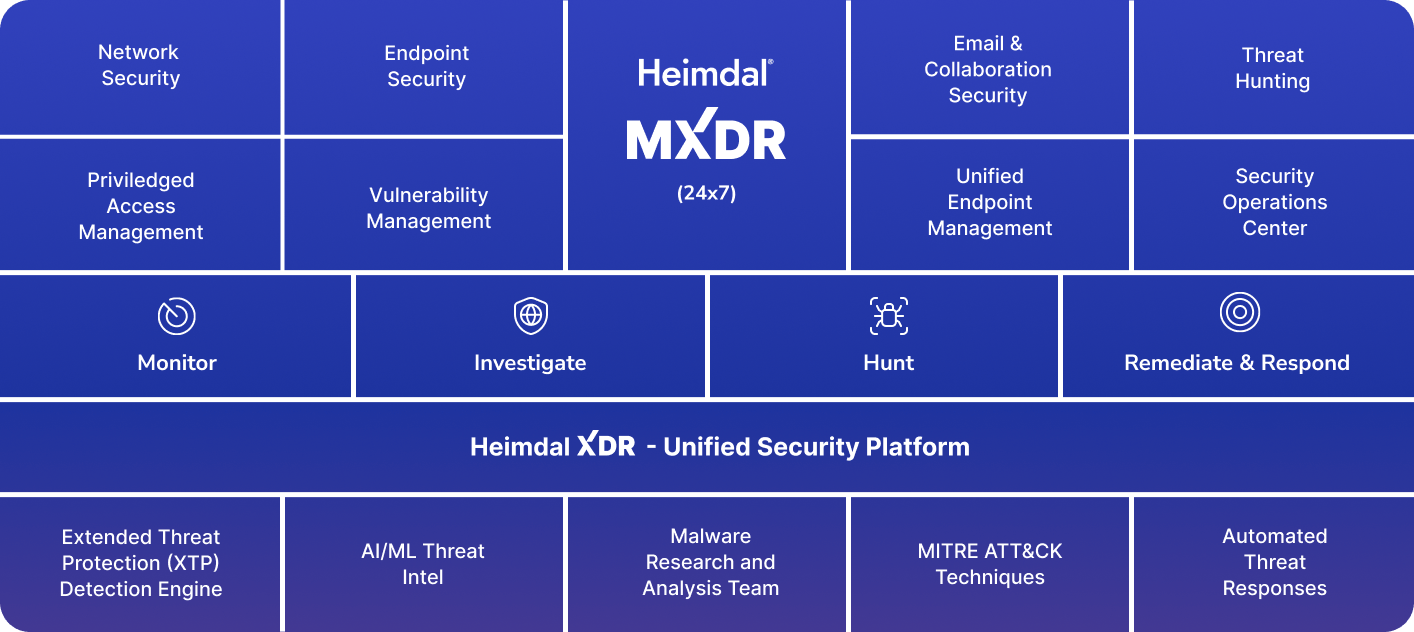
 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security


 “If you work in marketing, you should be able to make changes to articles on the website. But you shouldn’t go into development code or finance databases. So privileged access management is all about identifying you as a user and your role – and setting up rules for what you should be able to see and engage with in the company based on it.”
“If you work in marketing, you should be able to make changes to articles on the website. But you shouldn’t go into development code or finance databases. So privileged access management is all about identifying you as a user and your role – and setting up rules for what you should be able to see and engage with in the company based on it.”