Contents:
VPNOverview security researchers have found evidence of a data breach that may have exposed the sensitive information of 100,000 medical staff, including doctors, nurses, and other employees at important hospitals all over the US.
PlatformQ, a leading provider of digital engagement solutions in healthcare and education, as described on their website, accidentally made public a database backup contained in a misconfigured AWS S3 bucket. Based on what they discovered, the VPNOverview security researchers think that the leak was marketing data for the generic drug Zarex.
The experts found a treasure trove of confidential information in a backup database and across thousands of other documents. According to the research conducted by VPNOverview, the information is associated with the marketing of Zarex, a generic medicine used to treat and prevent ulcers in the stomach and intestines.
VPNOverview lead cybersecurity researcher Aaron Phillips declared:
It seems like the spreadsheets were being imported into the marketing database. I took a screenshot of the Zarex directory. A lot of the files had personal information, and we found all that same information in the database.
The Leaked Data
Full names, personal email addresses, job roles, business addresses, home, work, and personal phone numbers, as well as national provider identifier (NPI) numbers, were among the sensitive data that was exposed by the leak.
It’s critical to mention that NPIs, 10-digit codes used to identify medical specialists and providers, are frequently used on Medicare or Medicaid forms.
Additionally, the identifiers can be used to search publicly available government databases that contain even more specific information about individual healthcare professionals, including mailing addresses, practice addresses, and other identifiers.
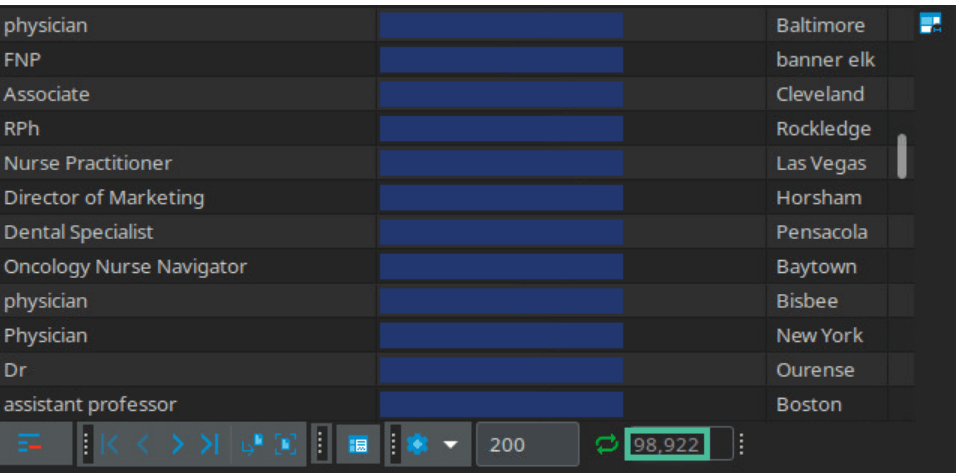
The database the security team recovered had 98,922 entries. They discovered a few dozen test entries, but most of the database included sensitive data.
An indication that these are personal email addresses rather than contacts that are available to the public is email handles like @gmail.com, @yahoo.com, and @verizon.com.
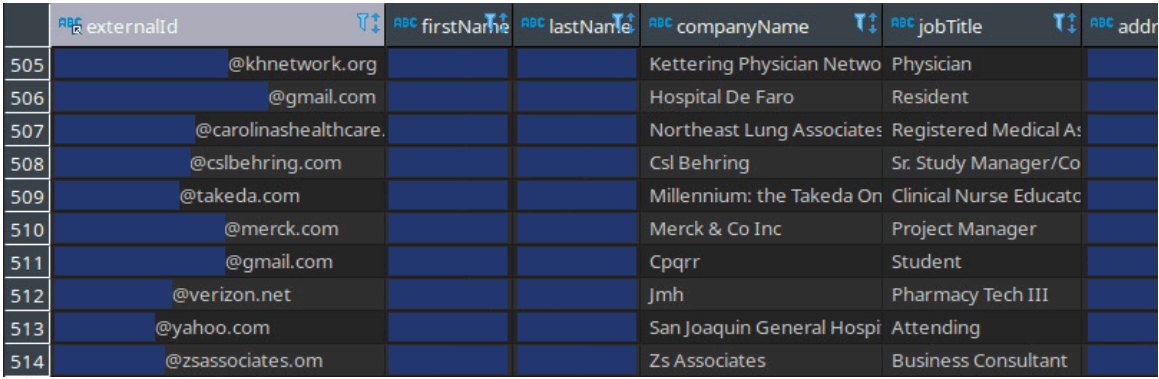
One thing that stood out to me was the large proportion of personal email addresses. If this data had been scraped from a federal registry, I would expect most of the email addresses to have healthcare domains. A lot of the addresses don’t match up with the federal registry, either. This looks like marketing data that was mishandled to me.
Although 255 different medical facilities were impacted, the following is a list of some of the significant ones where staff members’ data was disclosed:
- Yale New Haven Hospital
- Cleveland Clinic
- Barnes-Jewish Hospital
- Johns Hopkins
- Mount Sinai Medical Center
- Beaumont Hospital
- Saint Francis Hospital
- Memorial Hermann-Texas Medical Center
- Tampa General Hospital
- Massachusetts General Hospital
- Duke University Hospital
- Miami Valley Hospital
- MedStar Washington Hospital Center
- Houston Methodist Hospital
- Medical City Dallas
- Northwestern Memorial Hospital
- Henry Ford Hospital
- New York Presbyterian Hospital
- University of Maryland Medical Center
- Hackensack University Medical Center
VPNOverview Contacted PlatformQ to Announce the Breach
In February 2022, PlatformQ was informed of the breach but didn’t get back to VPNOverview. By April 2022, the researchers found that they had removed access to the database and spreadsheet files, thereby closing the leak.
PlatformQ was contacted again on several occasions but never responded.
The consequences of exposing this much confidential info are extremely dangerous. Threat actors could use this information to plan extremely targeted spam emails, phone calls, and texts. It may also allow for targeted phishing attacks and identity fraud.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










